Michael Rodler
@f0rki
Followers
609
Following
3K
Media
43
Statuses
6K
for some reason I like analyzing code; also 🤘 (he/him) also @[email protected]
Joined December 2011
RT @mehunhoff: 🚨 Our latest #Ghidrathon release has out-of-box support for Python 3 modules that don’t support multiple Python sub-interpre….
github.com
This release includes out-of-box support for Python modules that do not support multiple Python sub-interpreters running in a single process e.g. numpy, PyO3, Transformers, etc.. Note: to start us...
0
4
0
RT @FoundryZero: For too long has it been a mild inconvenience to not have the features of GEF in LLDB. We at Foundry Zero feel you deserv….
github.com
LLEF is a plugin for LLDB to make it more useful for RE and VR - foundryzero/llef
0
32
0
RT @seanmonstar: New #rustlang h2 release: v0.3.20 🦀. This includes several bug fixes found with additional fuzzing (thanks @f0rki!) Worth….
github.com
Bug Fixes Fix panic if a server received a request with a :status pseudo header in the 1xx range. (#695) Fix panic if a reset stream had pending push promises that were more than allowed. (#685) F...
0
1
0
RT @dystopiabreaker: one day google is going to randomly kill 8.8.8.8 for no reason and a double digit percentage of the internet as well a….
0
373
0
RT @JinshengBa: To avoid incomplete and incorrect citations in papers, I wrote a script to automatically correct BibTex files: https://t.co….
github.com
Search, check, and autofix your BibTex files! Contribute to bajinsheng/bibtidy development by creating an account on GitHub.
0
11
0
RT @michaelmarcozzi: 🥁I am looking for students and postdocs:. PhD student // 3 years, fully funded // Fuzzing . P….
0
19
0
yeah @ctfhacker released it :D this is an awesome project (although I might be biased).
AWS open-sourced a fuzzer. "load a raw memory dump and register state into a KVM virtual machine (VM) for execution. At a point in execution, this VM can be reset to its initial state"
0
1
2
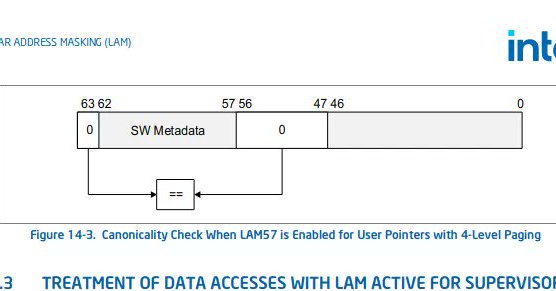
RT @kayseesee: Intel LAM support is merged to Linux upstream!.(LAM makes HWASAN possible, similar to Arm's top-byte-ignore). .
phoronix.com
Since 2020 Intel engineers have been working on Linear Address Masking (LAM) as a feature similar to Arm's Top Byte Ignore (TBI) for letting user-space store metadata within some bits of pointers...
0
28
0
RT @vxunderground: Today VirusTotal announced that each sample uploaded will be accompanied by "Code Insight". Code Insight uses Sec-PaLM,….
0
495
0
RT @mtarral: This is also the main fuzzer driving our initative to secure and harden the Linux kernel for Confidential Computing 🔐!. And it….
github.com
Linux Security Hardening for Confidential Compute. Contribute to intel/ccc-linux-guest-hardening development by creating an account on GitHub.
0
1
0