e1abrador
@e1abrador
Followers
279
Following
5K
Media
12
Statuses
2K
Open-source tool maker and Penetration tester. Public tools here: https://t.co/9YuVjVb5Q5
Spain
Joined August 2019
I have created a #CrackMapExec module to search for interesting files on compromised machines. Mainly focused when you have a large number of compromised machines and it is unfeasible to search 1 by 1 for files with useful information. thx @mpgn_x64 for the awesome cme project!
2
20
148
RT @asobanca_ve: Para una demostración realizaron un Ataque de Arquitectura Social en el II Congreso Internacional de Ciberseguridad🧠🦾 http….
0
1
0
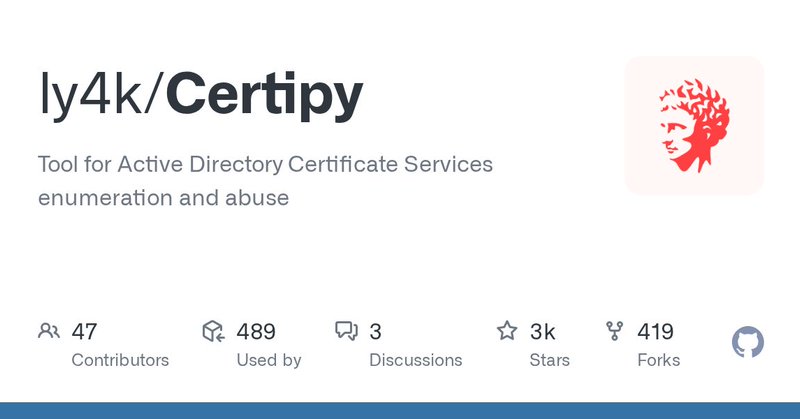
RT @sekurlsa_pw: Certipy v5 .▪️ESC16 (new).▪️ESC13 & ESC15.▪️Post exploitation of ESC12 & ESC14.▪️LDAP Signing and LDAPS channel binding de….
github.com
Tool for Active Directory Certificate Services enumeration and abuse - ly4k/Certipy
0
43
0
RT @Defte_: You have got a valid NTLM relay but SMB and LDAP are signed, LDAPS has got Channel Binding and ESC8 is not available. What ab….
0
205
0
RT @Jhaddix: Next week is our next run of our Attacking AI course!. Check out the expanded syllabus ⬇️ . 📢 Last Mi….
0
121
0
RT @doopsec: Just released SCCMHound! A BloodHound collector for SCCM. SCCMHound allows both attackers and defenders to construct BloodHoun….
0
102
0
RT @nbk_2000: Ok humans, for the next 6 hours @_Ali4s_ @e1abrador and I are answering #ReconRoyale questions. Ask us anything you want a….
0
6
0
RT @al3x_n3ff: A lot of cool new features for the MSSQL protocol just got merged into NetExec🔥. - RID brute forcing, made by @Adamkadaban….
0
97
0
RT @nbk_2000: For people into #ReconRoyale me and my teammates (@_Ali4s_ and @e1abrador) will do an AMA regarding how we keep winning. We'l….
0
12
0
RT @nbk_2000: Congrats @hasan_zmzm for winning the last round of #ReconRoyale !!! 🐾. It's not easy these days😸.
0
2
0
RT @nbk_2000: For people into #ReconRoyale if you'd be interested in an AMA on how me and my teammates (@_Ali4s_ and @e1abrador) keep winni….
0
11
0
RT @d4d89704243: We've just updated our URL Validation Bypass Cheat Sheet with a new IP address obfuscator by @e1abrador, and new payloads….
portswigger.net
The strength of our URL Validation Bypass Cheat Sheet lies in the contributions from the web security community, and today’s update is no exception. We are excited to introduce a new and improved IP a
0
29
0
Encode IP was mentioned on bsides by @GodfatherOrwa < 3 🔥🔥🔥🔥 soon a new version with more encoding techniques will be on bapp ; )
0
0
1
#bambdas That will test all the HTTP history requests for most common vulnerable SSRF parameters:.
0
0
2
RT @thebinarybot: 🛠️It's #ToolThursday and today I recommend you all to checkout "Burp-Encode-IP". #bugbounty #cybersecurity .
0
8
0
RT @GodfatherOrwa: Burp Ex.403 Bypasser.5GC API Parser.Active Scan++.Backslash Powered Scanner.CO2.IP Rotate.J2EEScan.JS Link Finder.JS Min….
0
316
0
RT @Jhaddix: Ok fam. I’m giving away TWO free tickets to my course which takes place in two/three weeks. All you have to do to win is lik….
0
698
0
RT @hack_git: Burp-headerSnipper. This extension will improve the user reporting experience. The extension is used to snip any header from….
0
20
0