Dedaub
@dedaub
Followers
9K
Following
597
Media
212
Statuses
805
Security audits, static analysis, realtime threat monitoring https://t.co/UZhGss2vbL
Joined January 2021
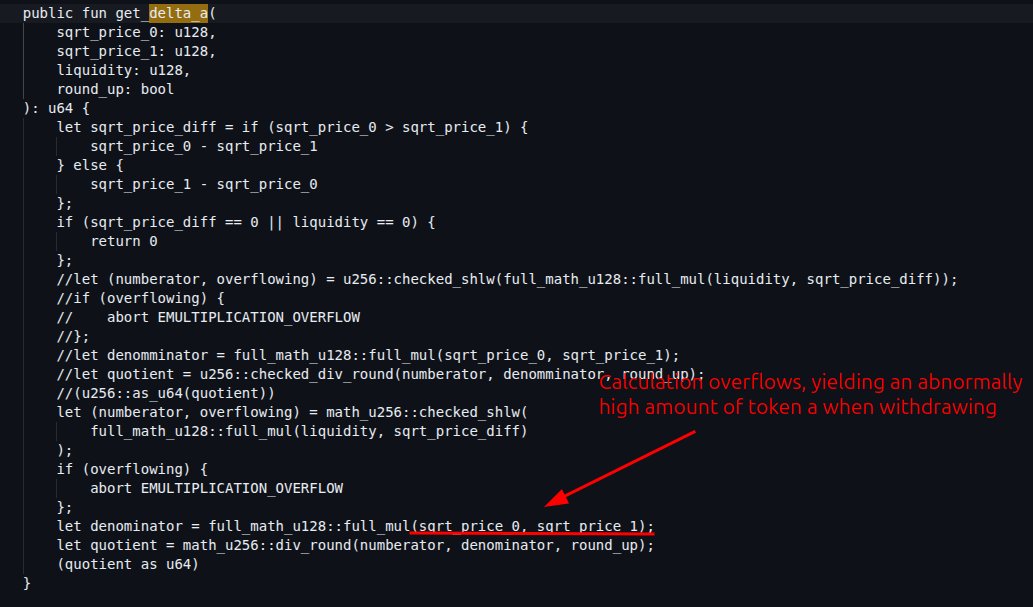
The Cetus AMM @SuiNetwork hack of $200M stolen is due to a flawed overflow check. The attacker added massive liquidity with just 1 token by exploiting a bit truncation vulnerability in the AMM math. Full details below ↓.
10
32
165
Cetus AMM on the @SuiNetwork has suffered a catastrophic ~$200M hack🚨. Root cause: an arithmetic overflow in the liquidity calculation that allowed an attacker to withdraw astronomical amounts of tokens from a small liquidity position. How did they pull this off? 🧵
26
98
480
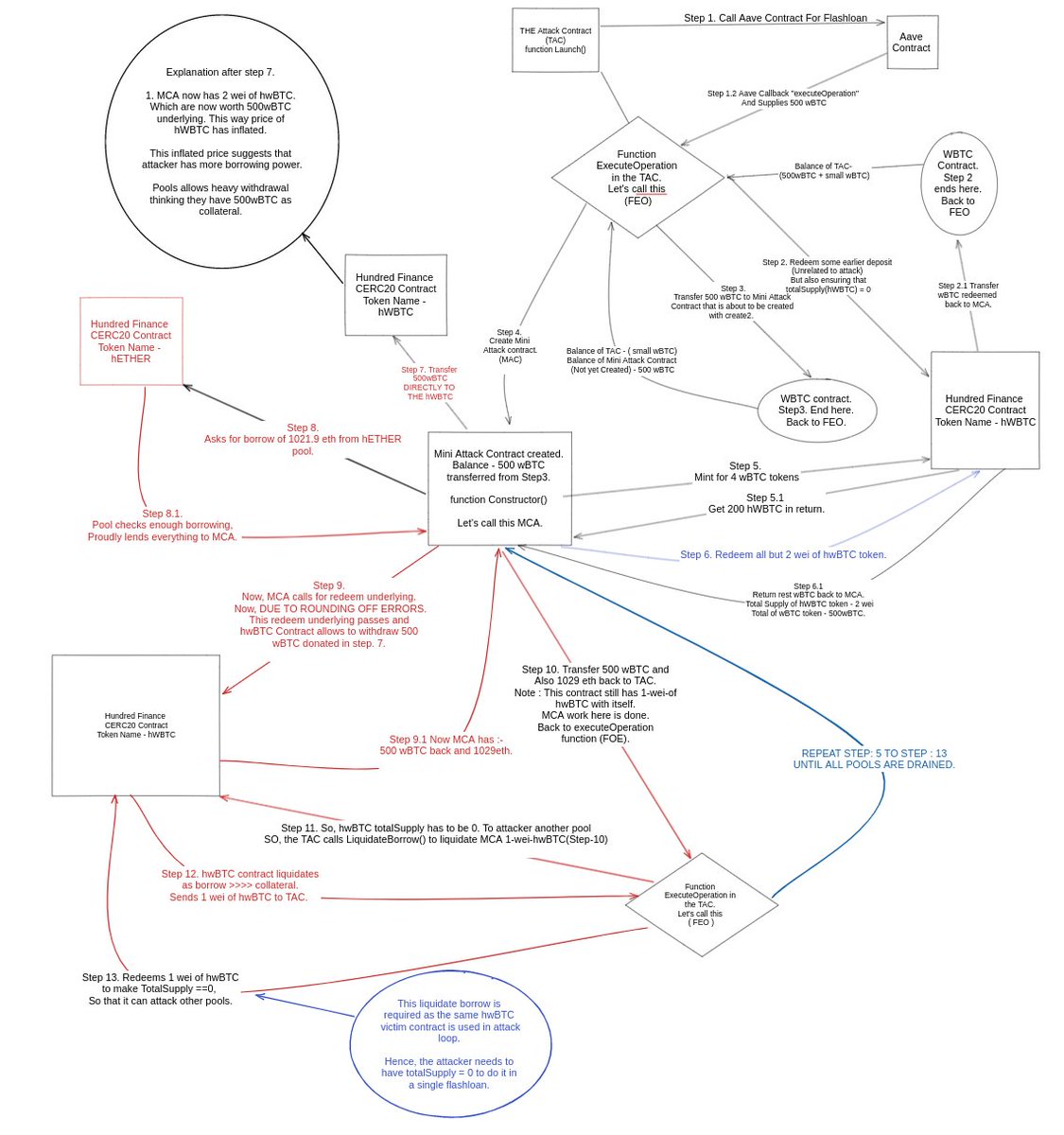
A number of Comp forks have been hacked, chiefly Hundred Finance. @compoundfinance V2 forks, satisfying conditions, e.g., cToken.totalSupply == 0, can be drained. However, no active protocols on @FantomFDN are affected. We verified this hours after the original attack w/Watchdog
9
46
204
A few days ago we disclosed one of the largest vulnerabilities. Ever. The disclosure helped protect @MultichainOrg and @FantomFDN . Learn all about it in our article.
6
51
199
Watchdog analyses operate on the actual bytecode of contracts (via decompilation as seen here). As a result, compiler bugs can also be caught by these analyses. Yesterday's @CurveFinance hack could have been prevented had a cross-reentrancy analysis on this codebase been run
1
10
107
We're excited to announce that @coinbase has engaged Dedaub as a security services provider for core contracts on Base. We look forward to further secure this fast-growing ecosystem. Congrats on a successful launch and opening @BuildOnBase mainnet to everyone!
5
17
94
TL ; DR 💔. The @TeamUnibot hack would have been prevented, for very little effort, had they checked the analysis warnings produced by Watchdog. Vulnerability was flagged 3 full days before hack / 10 minutes after deployment. Source code not required.
2
13
98
🔍 We've just completed an audit of @illuminexswap for @OasisProtocol.IllumineX is a privacy-preserving protocol performing cross-chain exchanges. It runs on Oasis Sapphire, a confidential EVM-based network that leverages Trusted Execution Environments.
5
15
83
🚀 Big news! . We’re excited to partner with @Immunefi on Magnus, the fully-integrated SecOps command center for onchain security. More on this partnership here: .#ImmunefiMagnus
2
7
79
Here at Dedaub, we aim to help DeFi projects launch without critical vulnerabilities. We’re thrilled to establish a channel partnership with @chainlinklabs to help support the Chainlink Build program with Web3 security technologies and comprehensive audits.
1
10
78
We are excited to be selected as @OasisProtocol Sapphire's preferred security partner. At Dedaub, we are committed to strengthening the security of projects like Sapphire's, utilizing our expertise in DeFi, privacy-preserving protocols, and advanced cryptography.
1
13
67
Couldn't agree more, @Chainlink! Security is non-negotiable in the Web3 space🔒. We're proud to be working with projects like Chainlink that set high standards for security 🤝. Looking forward to meeting like-minded teams at #SmartCon 2023!.
All Web3 projects need to put security first. Meet @dedaub at #SmartCon 2023 and learn how their auditing solutions help secure some of the most reliable Web3 protocols in the industry. Sign up now👇.
1
8
63
Five (5) lines of code in one file that would have led to the draining an entire ecosystem of protocols through the Multichain bridge. Over a USD 1B of WETH was available to be transferred due to “Phantom Functions”. Co-founder Yannis Smaragdakis at @TheTrustX @EFDevconnect
1
5
61
Announcing the integration of Contract Library ( with the following chains:. @arbitrum .@BuildOnBase .@FantomFDN .@ethereum . Coming soon: @optimismFND & @avax. Contract Library is a code explorer offering unique & indispensable features such as: (see 🧵)
4
7
43
Recently, a client asked us about an observed @CurveFinance anomaly: when there is a buy order for an asset, the price *after* the buy can be *lower* than the price *before*. (And similar for sell/higher price.) How is this possible? Buying should raise the price, right? (1/15).
2
11
39
In DeFi, edge cases aren't edge cases - they're attack vectors. AMMs are particularly vulnerable as they involve complex mathematical operations across extreme ranges. Contact us if you need help securing an @Aptos or @SuiNetwork project.
1
1
41
We have found small functions in projects like @uniswap or @CurveFinance where the gas may increase by an order of magnitude. In our report, some recommendations are addressed to compiler engineers. There are lots of ways gas cost increases can be mitigated on future contracts.
4
3
34
Our team has successfully audited the EVM assembly implementation contract for EIP-4788. The contract stores the last few beacon block roots on #Ethereum - using ring buffers to manage data. Despite the small size, we found issues, which have now been resolved. Find out more 🧵👇
2
4
35
Let's delve into the @thestandard_io exploit that occurred on November 6th, 2023. It is an excellent opportunity to re-emphasize that protocols should use defensive checks/assertions at every point their code interacts with a DEX.
1
3
33
#Uniswap recently introduced the Universal Router. It unifies ERC20 and NFT swapping into a single swap router. Users can perform heterogenous actions, e.g., swapping multiple tokens and NFTs in one tx. This router embeds a scripting language for all sorts of token actions.
1
1
29
We are proud to receive the generous, first-ever R bounty/Founders bounty (many thanks @RobertMCForster, @ArmorFi, and @immunefi) for the recent @PrimitiveFi vulnerability Disclosure.
0
6
26
Last November, #Uniswap introduced the Universal Router unifying all sorts of heterogenous actions & improving UX, e.g., swapping multiple tokens and NFTs atomicly. However, on some token transfers, the code can reenter the Router and claim any tokens temporarily in the contract.
4
0
28
How can metamorphosis happen?. Q: Doesn't CREATE use the factory's nonce as part of entropy which determines new contract address?. A: SELFDESTRUCT instruction *resets* this nonce!. The contract factory for the malicious proposal was recreated using CREATE2 at predictable addr.
Explore Tornado Cash attacker's transactions here. Interestingly, how did attacker's contract get recreated at the same address, despite being created using the CREATE opcode?. More on that soon. .
1
0
26
This week, together with @drdr_zz and @wh01s7 of SecuRing, we tackled a backlog of warnings from the Dedaub Watchdog tool, notifying around 100 holders of vulnerable accounts, with some $80M in funds exposed. (@_trvalentine had earlier produced the PoC.).
2
7
23
Please revoke your approvals ASAP. Someone is exploiting this.
1/A critical vulnerability that affected 6 tokens (WETH, PERI, OMT, WBNB, MATIC, AVAX) has been reported and fixed. All assets on both V2 Bridge and V3 Router are safe, and cross-chain transactions can be done safely. More info👇.
2
12
24
@eulerfinance Root cause analysis 🔬. The attacker's goal in the first 6 steps is to enter a position with a health factor as low as possible (underwater) but still escape liquidity checks. This is done 2 ways 👇
1
2
21
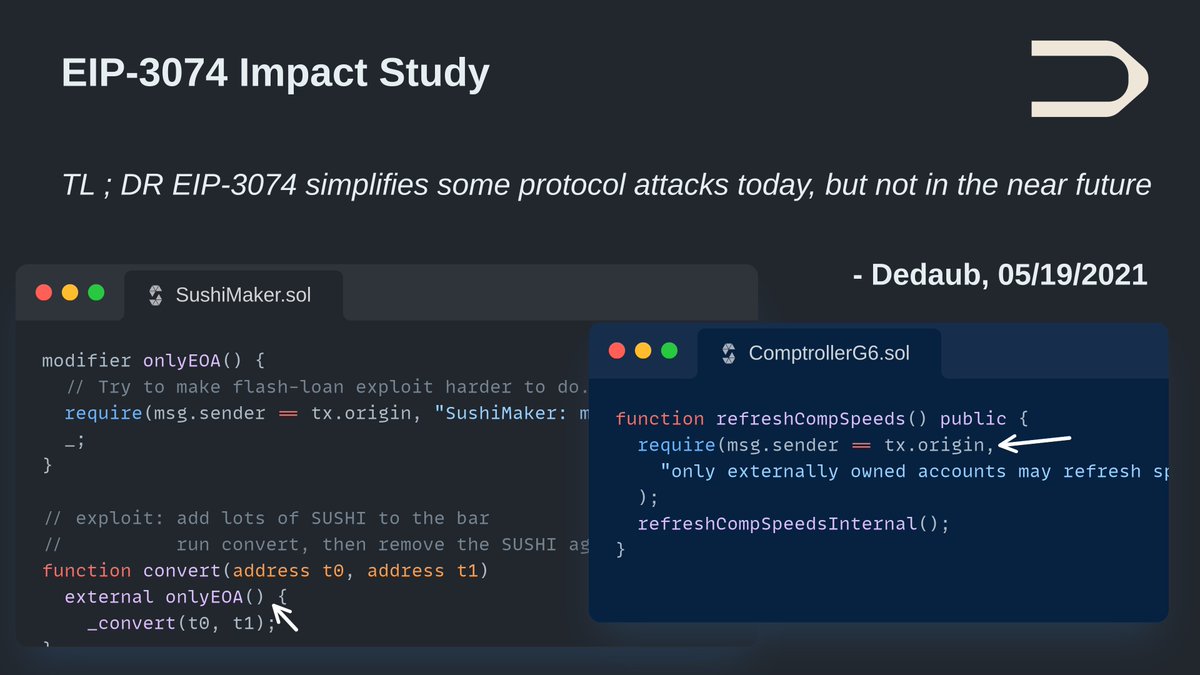
The @solidity_lang team will be disabling function pointer equality starting Solidity 0.9. We're not aware of any uses of function equality in known protocols. Fore more info:.
1
1
22
(Announcement). We are working with @eigenlayer and are at advanced stages of finishing an audit covering important systems of EigenLayer, including:. - EigenDA, the first AVS (actively validated service).- EigenLayer middleware. Stay tuned for updates.
1
0
22
One of the exploit txs was frontrun by a generalized frontrunner. On-chain negotiations between @CurveFinance deployer and frontrunner on the return of funds:
0
4
20