James Northey
@darkrym11
Followers
64
Following
3
Media
0
Statuses
6
SOC Analyst @HuntressLabs | Malware junkie | 5+ yrs in Military Cyber Always learning, always curious
Australia
Joined June 2025
In a recent investigation @HuntressLabs we uncovered how attackers used LFI for log-poisoning with an AntSword Shell to drop Nezha and then Ghost RAT. Big shoutout to @CyberRaiju and @birchb0y learnt heaps from them while working this one.
1⃣ The @Huntress team uncovered a campaign by a likely China-nexus threat actor. The most novel finding is use of a publicly available tool called Nezha as a post-exploitation C2 agent. This is the first public reporting of the tool I've seen.
0
4
16
For those who want to go step-by-step and actually learn the reversing process, I’ve written a walkthrough that starts beginner-friendly and ramps up into advanced malware RE: 👉
darkrym.com
Introduction Join me as we peel back layer upon layer of Python code, shellcode, and executables, each more difficult then the last all in the effort of uncovering a novel attack campaign. An...
0
2
7
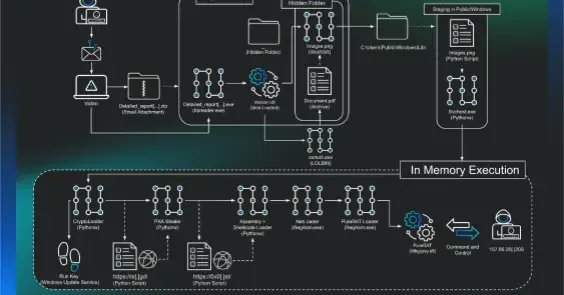
I found a sample of PXA Stealer @HuntressLabs, which wasn’t quite right. After a lot of analysis, I discovered it was loading PureRAT, a commercially available, modular backdoor focused on surveillance of the Victim. https://t.co/HZvLosdbaG
huntress.com
Trace a threat actor's journey from custom Python stealers to a sophisticated commodity RAT. Learn how their tactics evolved and why this shift to .NET matters.
1
6
18