Dan
@cyb3r_dan
Followers
79
Following
23
Media
4
Statuses
60
IT Information Security Specialist | M.S. | CASP+ | CySA+ | Sec+ | Net+ | CCENT
Joined December 2017
Interesting read on the discussion of possible threat vectors in the new 5G systems architecture and why it’s a huge concern #cybersecurity.
1
0
3
Very unethical. Not sure how they though this would be a good idea.
Researchers from University of Minnesota apologized to #Linux Kernel Project maintainers for intentionally introducing insecure code, which led to the school being banned from further contributing to the open-source project. Read: #infosec #cybersecurity.
0
1
1
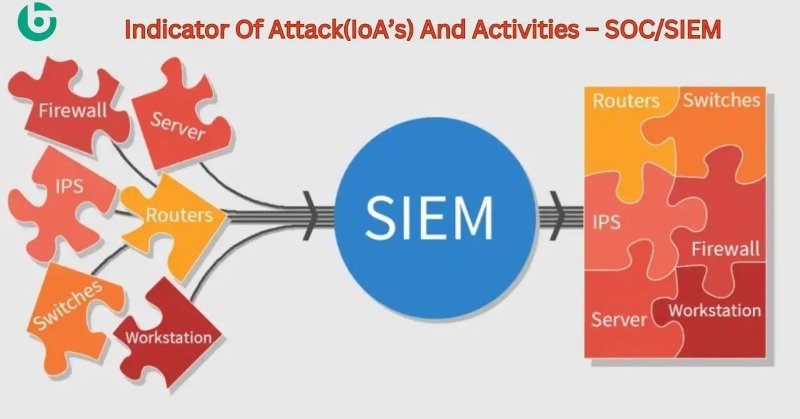
This is a good list of ten common IoC that every analyst should know #cybersecurity
gbhackers.com
Indicator Of Attack(IoA's) And Activities - SOC /SIEM- A Detailed Explanation, security incident and event management security operation indicator of attack
0
0
0
Imagine going to the kitchen to air fry some food and now you have to pay a ransom. RCE vulnerabilities uncovered in smart air fryer #cybersecurity
zdnet.com
Updated: The impacted vendor has not responded or fixed the security issues.
0
0
0
Zero Trust Networks (ZTNs) are invaluable. They address the biggest flaw in the perimeter security model: hosts aren’t protected from each other. Lateral movement and privesc are engrained in a hacker’s methodology. But in ZTNs, hosts are protected from each other #cybersecurity.
Cyber adversaries are getting more organized in their attacks. CIOs and CISOs need a defense strategy which embraces #zerotrust and #SOC modernization, and @splunk's Yassir Abousselham discusses using #data to defend against modern threats.
0
0
0
RT @HackENews: Cheatsheet: XSS That Work In 2021. . #HackENews.#XSS #infosec #bugbountytips #bugbountytip #cybersec….
netsec.expert
XSS Cheatsheet for 2021 and onwards.
0
20
0
“The recent weather-related outages in Texas, while not the result of a cyber-attack, were a stark demonstration of the potential for devastation.” #cybersecurity.
0
0
0
This career pathway tool helps you explore specific cybersec roles and it identifies their core tasks, knowledge, skills, and abilities. It also recommends specific training, certifications, and degree programs related to that role. #cybersecurity #infosec.
👩💻 Are you a current #cybersecurity professional looking to advance your career? Check out @CISAgov's updated Cyber Career Pathways Tool for opportunities to excel in the #infosec industry! .#Careers #CyberWorkforce #IT #Jobs #Skills #NICCS #NetSec
0
0
2
Cozy Bear is conducting widespread scanning and exploitation against U.S. government networks to obtain authentication credentials to allow further access. The five, fixed bugs under active attack affect Citrix, Fortinet, Pulse Secure, Synacor and VMware #cybersecurity #infosec.
Spies and more spies: 5 bugs known to be favorites with the #APT crowd are still unpatched in large numbers of organizations. If you want to be low-hanging fruit for data theft, keep on ignoring #security bugs I guess. #cybersecurity @NSAGov.
0
1
3
Been seeing a big uptick in this on @reddit.
Hackers are abusing Discord, Slack file-sharing to distribute malware. Here's what to be on the watch for —> .
0
0
0
RT @TheHackersNews: There are a lot of jobs in #cybersecurity, depending not only on your skill level and experience, but also what you lik….
thehackernews.com
Find out which jobs are the best and most in demand in cybersecurity.
0
89
0
RT @TheHackersNews: A Hacker Tried Selling Stolen U.S. Military Drone Documents On #DarkWeb For Just $200 —by @Swati_THN. .
0
164
0
RT @TheHackersNews: Hacker Puts RDP Access to a Major International Airport’s Security System On Dark Web Sale For Just $10. .
0
219
0
RT @threatpost: Researchers have discovered two new #Spectre variants - earning them a $100,000 #BugBounty reward from Intel: https://t.co/….
0
27
0
RT @CyberNews4you: Suspect we will see more of this: insurance companies suing security firms for failure to ID malware after paying out $3….
bleepingcomputer.com
Two insurance companies are suing a cyber-security firm to recover insurance fees paid to a customer after the security firm failed to detect malware on the client's network for months, an issue that...
0
5
0
RT @threatpost: Users complained online that their #Galaxy devices are randomly sending photos to contacts - but #Samsung said it isn’t a h….
threatpost.com
After users complained online that their Galaxy devices are randomly sending photos to contacts, Samsung said it isn’t a hardware or software issue.
0
15
0