Ajax
@commial
Followers
1K
Following
212
Media
17
Statuses
235
#Miasm, the reverse engineering framework in Python, has a new home: !.Asm/Dis, IR translation, Emul, Symbolic exec….
github.com
Reverse engineering framework in Python. Contribute to cea-sec/miasm development by creating an account on GitHub.
0
50
60
RT @KensyAtMS: Do you wish Time Travel Debugging was faster and more lightweight? Our latest version lets you decide exactly what you want….
0
26
0
RT @ANSSI_FR: L’@ANSSI_FR lance #Hackropole 🏛 une plateforme regroupant la quasi-totalité des épreuves du France Cybersecurity Challenge #F….
0
172
0
RT @chompie1337: Honored to be invited to speak at @sstic today. Stream my talk “Deep Attack Surfaces, Shallow Bugs” here: .
0
37
0
RT @monoxgas: A short🧵 detailing a Kerberos LPE I discovered while working with @tiraniddo on our BlackHat research. .
0
121
0
RT @IvreRocks: If you use @obsdmd for your #pentest / #redteam or #threatintel notes, you might be interested in the IVRE community plugin….
0
4
0
RT @sstic: Comment bien commencer la nouvelle année ? En soumettant à SSTIC ! Vous avez jusqu'au 30 janvier. Toutes les infos : https://t.c….
0
22
0
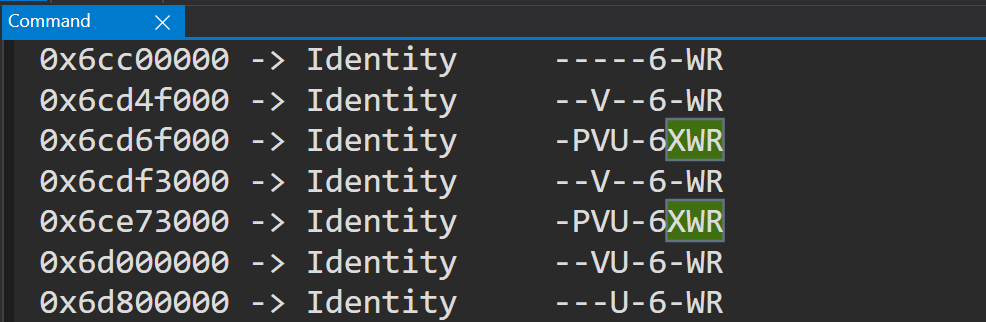
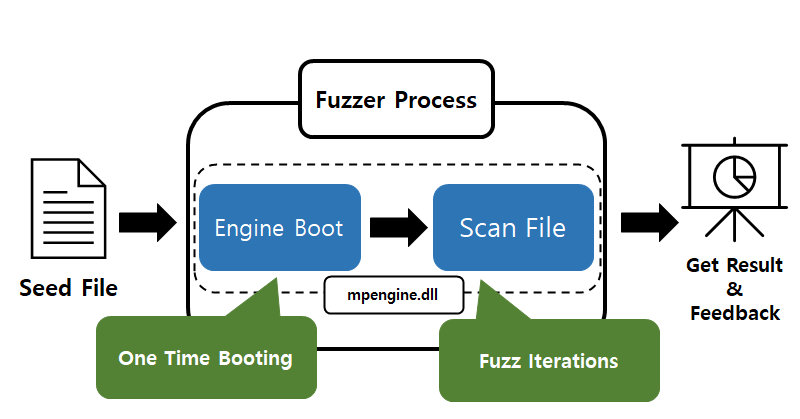
RT @dj_s2w: My first blog post about analyzing windows defender is out! Fuzzing the Shield: CVE-2022–24548 -
medium.com
Author: Daejin Lee, Seunghoe Kim, Donguk Kim, Eugene Jang
0
180
0
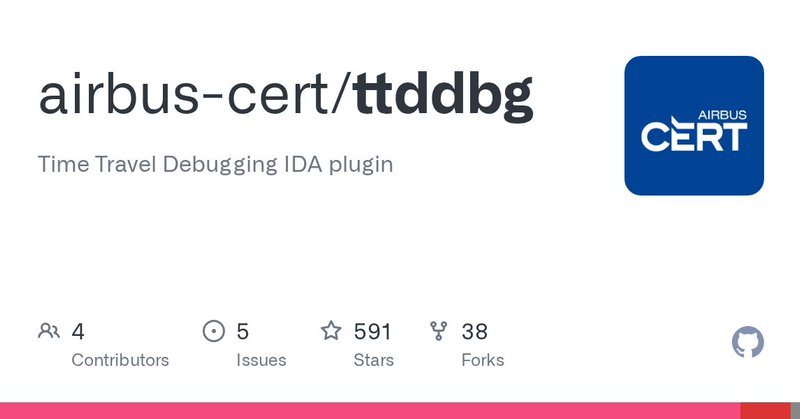
RT @citronneur: The results are out! . We are very honoured to have won first place🥇in the Hex-Rays plugin contest 2022 🎉.Our entry was "t….
0
21
0
New release of featuring more API wrapping (thanks @citronneur), and new examples: coverage (LightHouse compatible) and a trace producer for the awesome Tenet plugin (cc @gaasedelen)
1
16
54
RT @Intel80x86: After 3 years of development, today we proudly announce & celebrate the first release of a new hypervisor-based user-mode &….
0
285
0