monoxgas
@monoxgas
Followers
5K
Following
713
Media
19
Statuses
334
Security engineering, research, exploits, ml. Co-Founder with @moo_hax at @dreadnode
Utah
Joined October 2010
RT @dreadnode: Introducing AIRTBench, an AI red teaming benchmark for evaluating language models’ ability to autonomously discover and expl….
0
37
0
Crazy ride so far. Will and I continue to learn the importance of having a great team around you. I'll take my time here and extend a huge thank you to the @dreadnode team who work extremely hard everyday to build a company with us. You all rock.
Today, Dreadnode announces $14M Series A funding led by @DecibelVC, with @nextfrontiercap, In-Q-Tel, Sands Capital, and Indie VC. Dreadnode exists to show that AI can perform offensive security tasks on par with, and exceeding, human capability. To accomplish this, we’re
1
3
26
Also added in some code we wrote to hack against web APIs: Memory, goals, context pinning, actions, etc. @hanspetrich has been hacking on this stuff internally
0
1
6
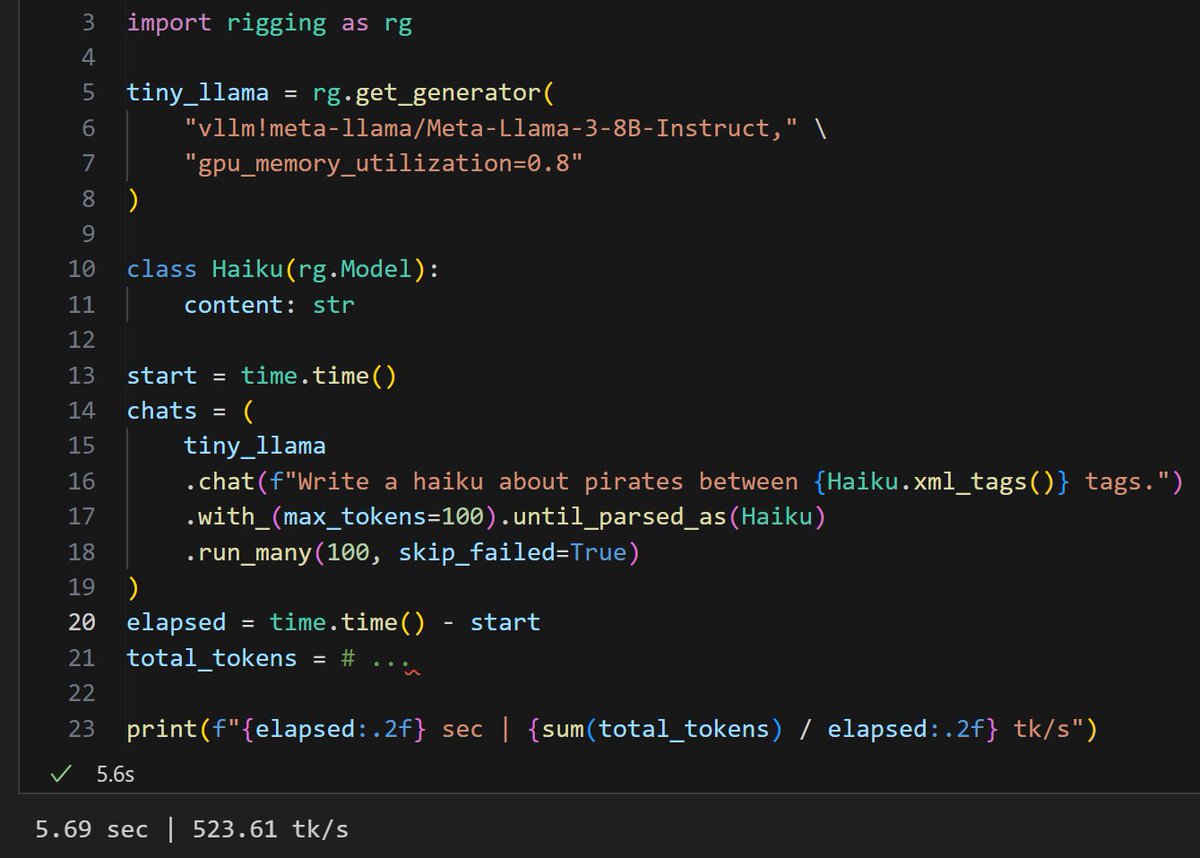
I took an early stab at PGD for LLMs based on (@geisler_si). Neat technique to relax the one-hot for gradient updates + projection. Also got to spend some time with litgpt. Experimental and messy, but enjoy.
github.com
General research for Dreadnode. Contribute to dreadnode/research development by creating an account on GitHub.
2
7
22
Shout to @Rob_Mulla for the 4 new Bear challenges. Awesome place to get started with great walkthroughs. The roadmap is looking 🔥this year.
The first big update is live inside Crucible. New dashboard, never before seen challenges, progress tracking, walkthroughs…. Go check it out!.
0
0
4
The most common ask we got after the @aivillage_dc CTF on @kaggle was to make the challenges available all the time. We took our first steps today and look forward to building out a great ML CTF and learning platform. Hope you enjoy!.
Crucible beta is now open! Free for everyone. Come learn how to hack, evaluate, and work with ML systems in a safe hosted environment. Be on the look out for new challenges and announcements as we expand our materials.
2
3
14
RT @safe_paper: Are aligned neural networks adversarially aligned?.Nicholas Carlini, Milad Nasr (@srxzr), Christopher A. Choquette-Choo, Ma….
0
6
0
This entire attack is trivial with @tiraniddo's NtApiDotNet libraries. I HIGHLY recommend you check them out for any related research. Minimal PoC is here: Worth noting that this will break many Kerberos things until a reboot 😉.
gist.github.com
Minimal PoC code for Kerberos Unlock LPE (CVE-2023-21817) - urbandoor.cs
8
48
124