yan
@bcrypt
Followers
76K
Following
26K
Media
2K
Statuses
20K
security engineering @brave / helped build Let's Encrypt, Privacy Badger, and HTTPS Everywhere @eff / physics alum @mit / rabbit enthusiast
Joined November 2012
could not for the life of me figure out how to buy a bus ticket in Milan. it was literally easier to get a shell 😆
91
646
7K
long thread about a phishing attack that has proper headers from google’s domain but for true DKIM stans, the interesting part starts here.
Here's how it works: First, they register a domain and create a Google account for 'me@domain'. The domain isn't that important but it helps if looks like some kind of infra. The choice of 'me' for the username is clever, as you'll see in a minute.
6
20
146
RT @mer__edith: 📣🚨 BAT SIGNAL: A law in France that would mandate a backdoor in end to end encrypted communications is set for a vote withi….
0
875
0
ecdsa private key leak due to nonce reuse strikes again, this time in the elliptic npm library
github.com
Elliptic's private key extraction in ECDSA upon signing a malformed input (e.g. a string)
1
34
166
RT @scumitchell: I benchmarked over 100 HTML tags so you don't have to and here are the visualized results. Not all HTML tags are created….
0
501
0
RT @chrisrohlf: A little over 10 years ago I and @dugdep stood up the first Yahoo! Red Team when I joined the Paranoids under @alexstamos.….
0
11
0
70 mb/24 hours, call it hurricane comcast.
A massive "bomb cyclone" is set to explode off the U.S. West Coast with hurricane force winds, flooding rains, and enormous mountain snow from Category 5 atmospheric river. Central pressure will fall almost 70 mb / 24 hours reaching 942 mb -- similar to Category 4 hurricane.
5
7
73
reminder that the bcrypt hash function ignores input above a certain length! so if you do bcrypt(username || password) for some reason, a sufficiently long username will make it accept any password. to fix this you can sha256 the input first.
Okta allowing login bypass for any usernames with 52+ characters is insane. Official Security Advisory:
63
1K
6K
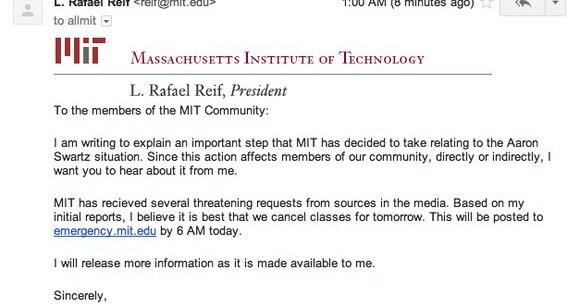
some cool things i've learned since posting:. 1. many other universities have the same issue.2. lots of MIT folks know about this already; see this 2013 article for example IMO this problem is not going away anytime soon so more ppl should be aware of it.
thetech.com
A fake email that appeared to be sent by President L. Rafael Reif addressing all of MIT was sent to all MIT dorms at 1 a.m. this morning, announcing that all classes would be cancelled for Wednesday,...
17
23
744
there is a scam going around where someone says they are interested in hiring you, but insist on using "brave talk" / "wechat" / etc. to do a call. when you click to join the call, it says you have to download an installer which is actually malware.
⚠️ Friendly reminder: Brave Talk will never ask you to download software. Anyone, or any sites, asking you to download Brave Talk are trying to trick you into downloading malware. Brave Talk is only available through
6
73
223