Chi-en (Ashley) Shen (@ashl3y-shen.bsky.social)
@ashl3y_shen
Followers
4K
Following
2K
Media
53
Statuses
754
Security researcher @TalosSecurity / Ex-Google TAG / Black Hat USA & HITCON Review Board / Organizer of @rhacklette41. My tweets are my own opinion.
Zurich, Switzerland
Joined March 2012
🚨 We discovered that some versions of WeChat were vulnerable to CVE-2023-3420 due to the outdated V8 engine in Xweb. We reported this to the vendor in April. WeChat users should update to the latest version to stay secure. More details in #vulnerability.
blog.talosintelligence.com
While this issue was disclosed and patched in the V8 engine in June 2023, the WeChat Webview component was not updated, and still remained vulnerable when Talos reported it to the vendor.
0
25
48
RT @natashenka: While most vendors ship timely patches for vulnerabilities reported by Project Zero, they don’t always reach users. Today,….
0
40
0
Can’t believe it’s only a week away! Join us on Aug 6th at “Hacking the Status Quo” @BlackHatEvents USA with @chompie1337, @natashenka & @InfosecVandana. Truly honored to share the stage with such inspiring voices!.
I’m honored to be joining some amazing women in cybersecurity at the #BHUSA panel “Hacking the Status Quo”. We’ll be sharing the journey of our careers: how we got started and what’s shaped us. Bring your questions and leave with fresh perspective 😊
1
2
18
I shared my journey of how I started in cybersecurity in a @DarkReading interview highlighting women who have navigated and shaped the cybersecurity industry. Excited to dig deeper and meet you all at #BHUSA soon!.
0
0
5
Excited to see another threat intel focused conference taking place in Europe, and it’s organized by threat analyst in the field! The CFP is opened until Sept 1st. Looking forward to see your amazing research!.#What_is_SOS #StateOfStatecraft.
State of Statecraft (SOS) is a new security and intelligence conference purposed to bring together observers of espionage, sabotage, influence, and other unique forms of covert statecraft to share their work with a community hyper-focused on tackling state-sponsored ops.
1
2
5
Had a great time on the @malspace podcast with Julien talking about my PIVOTcon presentation from tracking compartmentalized attacks to thoughts on attribution. Fun convo (and I loved the theme song at the end!). 🎶 Thanks for having me!.
After 365 calendar duels…⏳.@ashl3y_shen on compartmentalized attacks, IAGs, attribution & Swiss cheese 🧀.🎧 #CyberSecurity #ThreatIntel #ThreatResearch.
0
5
10
🧀 We are having a new Rhacklette event on July 11th! I’ll be giving a presentation on the world of spyware! The event is open to FINTA folks including non-members. #Rhacklette #womenincyber.
🌞 Save the Date: July 11th Rhacklette Summer Talk & Picnic! We're thrilled to invite you to our next Rhacklette event featuring @ashl3y_shen, who will take us "Into the World of Spyware". After the talk, we’ll head to the lake for a casual picnic! (1/2).
0
1
7
I'm excited to return to Black Hat USA this year and have the opportunity to give away one briefings pass to the conference. If you're a student or someone who could use a little support to attend, I'd love to hear from you. DM me if you're interested! .#BHUSA
4
6
73
RT @silascutler: Really excited to see this research go live. We found 400 web based HMIs for US Water facilities open on Censys. With the….
0
66
0
RT @chompie1337: Me and the homies are dropping browser exploits on the red team engagement 😎. Find out how to bypass WDAC + execute native….
ibm.com
Previously discovering a method for bypassing even the strictest WDAC policies by backdooring trusted Electron applications, the IBM X-Force Red team continued their research and can now bypass the...
0
238
0
Huge thanks to @vtxproject for updating Synapse to support the new "relationship" context. We’re excited to see this research foster collaboration and push real change across the threat intelligence community.
0
0
5
In blog 2, we dive into the challenges of investigating compartmentalized campaigns. We share our approach to identifying them and propose an extended Diamond Model with a new "relationship" layer to close the analytical gaps.
blog.talosintelligence.com
How do you profile actors and defend your systems when multiple threat actors are working together? In Part 2, Cisco Talos proposes an extended Diamond Model to analyze complex relationships between...
1
0
7
📡New blogs out: Compartmentalized attacks are no longer limited to financially motivated actors, state-sponsored groups are adopting them too. We propose a new taxonomy for initial access groups to reflect broader motivations and affiliations.
blog.talosintelligence.com
Threat actors are teaming up, splitting attacks into stages and making defense harder than ever. In Part 1, Cisco Talos examines their tactics and defines their motivations.
1
20
46
Had an amazing time speaking at @pivot_con last week! Grateful for the chance to share insights and connect with the brilliant minds. PIVOTcon remains my favorite threat intel event in Europe. Huge thanks to the organizers for creating this community and the memorable experience.
0
5
39
A lot of you have been asking, YES!.@HacksInTaiwan 2025 CFP is open! The conference will be host on August 15 - August 16. Submit your talk before June 8th. Looking forward to your submissions! #HITCON #HITCON2025 CFP:
HITCON 2025 - Call for Paper. 今年主題:Perimeter Security is Dead, Long Live Resilience. 隨著攻擊手法日益複雜,傳統邊界防禦機制已難全面阻擋威脅。如何讓系統適應新型攻擊、維持穩定運行,並在受攻擊後快速恢復,正是「Cyber Resilience 網路韌性」的核心精神。從
0
4
5
I’ve seen companies set up detection pipelines that submit files to public sandboxing services 🤦♀️ It made me wonder, could attackers manipulate detections to trigger the pipeline? That might be an overlooked path to launch a supply chain-style attack causing sensitive data leaks.
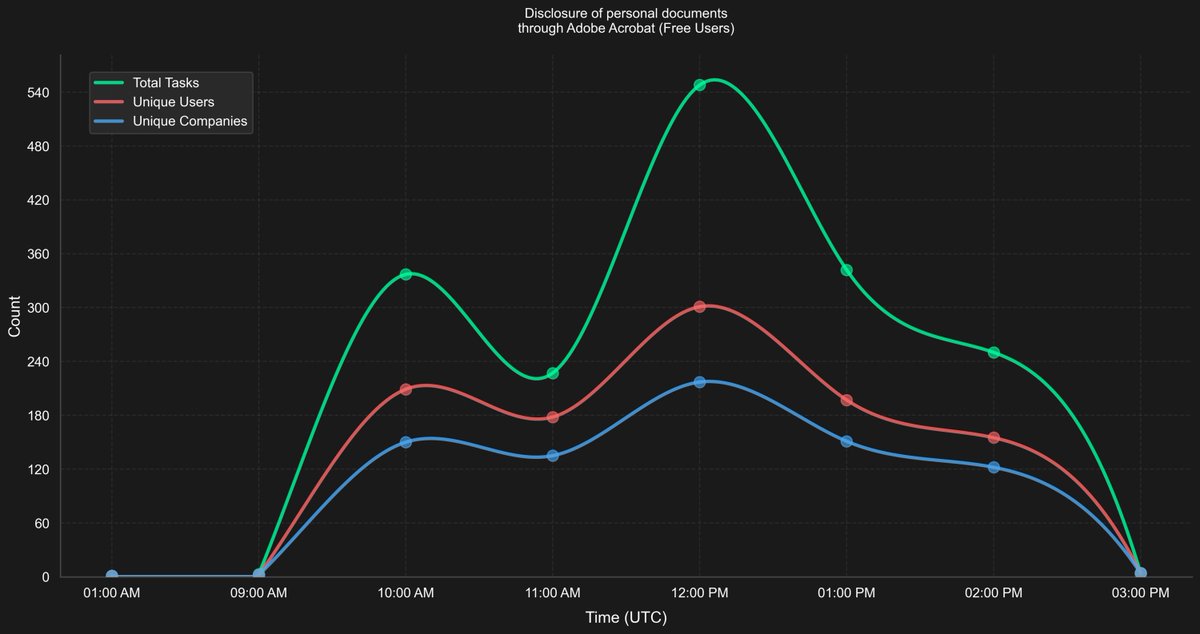
🚨 Important: False positive from MS Defender XDR has led to 1,700+ sensitive docs being shared publicly via #ANYRUN alone. A couple of hours ago we saw a sudden inflow of Adobe Acrobat Cloud links being uploaded to ANYRUN's sandbox. After research, we've discovered that
0
0
5
We just published our investigation into a Cactus ransomware campaign, uncovering TOYMAKER, an IAB group using a custom backdoor LAGTOY. It’s still challenging to identify compartmentalized attacks. We’ll share our approach and solutions at @pivot_con in 2 weeks! #toymaker.
Talos uncovered a major compromise in a critical infrastructure enterprise by an IAB, ToyMaker, and a double extortion gang, Cactus. Learn how ToyMaker infiltrates vulnerable systems:
1
8
24