Katie Knowles
@_sigil
Followers
3K
Following
2K
Media
144
Statuses
1K
Senior Security Researcher @ Datadog. 🐕 Head in the (Azure) clouds. Sometimes blogging, always curious. Aim to be, rather than to seem.
Toronto, Ontario
Joined September 2010
🕵️♀️ Looking to escalate privileges with a first-party Microsoft app? How do federated domain backdoors work? And what's an app reg, really? All this and more in our new @datadoghq Security Labs post: https://t.co/slcZAdelZE
securitylabs.datadoghq.com
Backdooring Microsoft's applications is far from over. Adding service principal credentials to these apps to escalate privileges and obfuscate activities has been seen in nation-state attacks, and...
0
26
61
My gift for Thanksgiving 💜 I wrote for you the blog post I always wanted to read! Happy holiday!🦃 PLEASE READ IT!!! https://t.co/Pr3P3jOh8s
wiz.io
Attackers abuse OAuth flows like device code phishing and ROPC to bypass MFA and gain persistence in Azure. Here's how to detect them with Entra ID logs.
9
82
237
Some amazing research by @CodyBurkard on Azure API Management and Managed Identity certificates. Go read this right now. I was able to replicate it in my environment and it's so nice to see one of these certs again - https://t.co/V795nz0Wnt
0
10
23
Had a great chat with @merill about all things Entra security! Thanks for having me on. 😁
Katie Knowles joined us on https://t.co/v0cFtrPykt last week to share some of her latest research findings and tips for Entra admins to secure their tenants. Check it out at https://t.co/mgGH2IurUX
1
1
9
🎙️ @_sigil has done some amazing research on Entra recently. Here's a recent post she shared about the unique relationship between App Registrations and Service Principals. Here's the full blog post on her app research titled I SPy: Escalating to Entra ID's Global Admin with a
3
30
143
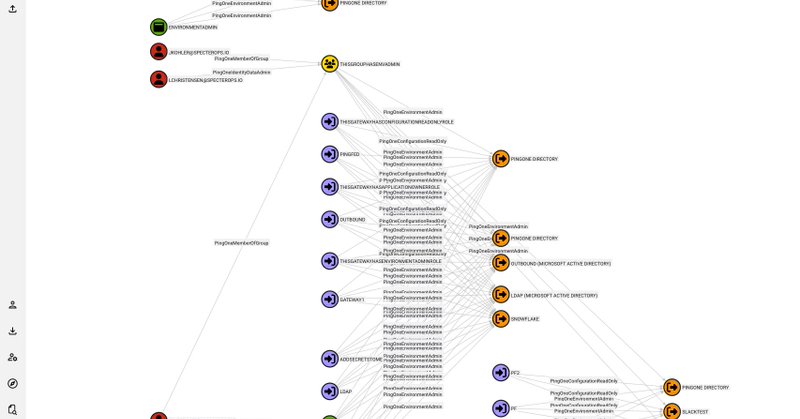
In this post @_wald0 introduces PingOneHound, a BloodHound OpenGraph extension that allows users to visualize, audit, and remediate attack paths in their PingOne environment. The blog post also serves as an introduction to the PingOne architecture. https://t.co/BjD5DPiih1
specterops.io
You can use PingOneHound in conjunction with BloodHound Community Edition to discover, analyze, execute, and remediate identity-based attack paths in PingOne instances.
0
24
50
😈 Copilot Studio agents are great for users... and attackers! Check out our deep-dive on why you should be careful to trust unknown agents, plus background on upcoming app consent changes that will help prevent our demo scenario. https://t.co/fvsL9VoJgL
securitylabs.datadoghq.com
Copilot Studio links look benign, but they can host content to redirect users to arbitrary URLs. In this post, we document a method by which a Copilot Studio agent's login settings can redirect a...
0
5
15
One of the most insecure defaults is getting less insecure at the end of this month. Microsoft is limiting what permissions a user can consent to. This is very interesting for everyone doing #BEC investigations. Curious to see if this will impact malicious app usage. More info
0
8
35
I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog:
dirkjanm.io
While preparing for my Black Hat and DEF CON talks in July of this year, I found the most impactful Entra ID vulnerability that I will probably ever find. One that could have allowed me to compromise...
141
905
3K
💥 𝐂𝐥𝐨𝐮𝐝 𝐋𝐚𝐛𝐬 𝐢𝐬 𝐥𝐢𝐯𝐞! 🏗️ A hands-on lab environment to practice your cloud incident response skills. https://t.co/Kbjp72CmcG We're also doing a giveaway here, to enter: 1. Like this post 2. Comment why you want to have access (Winners announced Monday
12
8
55
😭 Old and busted: Cloud attackers making noisy List/Describe calls. 🔥 New hotness: Laundering enumeration calls through an AWS service silently. Or at least, that used to work, until @datadoghq partnered with AWS to close this gap. Read more here: https://t.co/Xl1eHohEuX
securitylabs.datadoghq.com
Discover how attackers could quietly enumerate AWS resources via Resource Explorer, and how Datadog and AWS worked together to close the visibility gap.
3
9
33
🎉 Exciting news: The Office 365 Exchange Online SP privilege escalation we documented in "I SPy" is no longer possible! We've updated the post to reflect this. Thanks to Eli Guy for the tip on this one: https://t.co/9y68Kk604i
securitylabs.datadoghq.com
Backdooring Microsoft's applications is far from over. Adding service principal credentials to these apps to escalate privileges and obfuscate activities has been seen in nation-state attacks, and...
0
8
29
Why should Microsoft's Nested App Authentication (NAA) should be on your security team's radar? @Icemoonhsv breaks down NAA and shows how attackers can pivot between Azure resources using brokered authentication.
specterops.io
In depth walkthrough for using nested app authentication (NAA), or BroCI, for offensive engagements to access information and resources.
0
21
64
Consent & Compromise: Abusing Entra OAuth for Fun and Access to Internal Microsoft Applications
research.eye.security
The Eye Security Research team has uncovered a new critical misconfiguration that exposed sensitive data at internal Microsoft applications.
2
6
27
Today, together with Jonathan Elkabas, we're releasing EntraGoat - A Deliberately Vulnerable Entra ID Environment. Your own hands-on Entra lab for identity attack simulation. Built for red teams, blue teams and identity nerds. Check it out here👉 https://t.co/5qlXQiSYHS
8
237
703
If anybody is interested in Azure DevOps and how attackers might go about abusing OIDC connections used in pipelines then check out my colleague’s latest blog! https://t.co/frWo1pad8y
labs.reversec.com
Workload Identity Federation - is it all it makes out to be? Does it really prevent attackers from extracting credentials from pipeline identities that use modern authentication technique?
1
6
20
Excited to see folks at DEFCON next week!! Ready to see some great talks and get those conference steps in. 👟
0
1
11
We're looking for a curious AI security researcher to join us! 👀
Join my team! We’re looking for a Senior Security Researcher specializing in Generative AI. You’ll have the opportunity to be a part of one of the leading security research organizations in the industry and shape Datadog’s security products! A 🧵 https://t.co/C74vwOJsiy
0
2
7
This is a great point! Ensuring your cloud admins aren't synced users will prevent the federated domain takeover scenario, as only synced users are vulnerable.
@_sigil Nice talk Katie! The easiest way to prevent the attack you demonstrated is to avoid giving admin permissions to synced users (=no ImmutableID)
0
0
4