_bhamza
@_bhamza
Followers
389
Following
1K
Media
15
Statuses
759
Big milestone: HTTP Toolkit just crossed one million downloads! 🚀 Honestly I didn't think it'd ever get this far, I'm blown away. A huge thanks to all the users, contributors & supporters over the years ❤️. Onwards!
5
2
18
(Automated) Pentesting is already dead I found it interesting how many people misunderstood and ignored the context of my earlier post here, which was about (Tenzai) securing a $75M seed round, and more specifically AI powered automated penetration testing. I’ve been doing a
11
52
333
Syzkaller now supports VirtualBox 🚀 I’ve open-sourced my work to help push fuzzing and kernel security research forward. https://t.co/PpGv6OFIl1
github.com
This commit introduces support for running syzkaller VMs on VirtualBox. VirtualBox integration enables fuzzing drivers of VirtualBox. The implementation includes VM lifecycle operations such as boo...
1
8
38
Runtime Mobile Security (RMS) 📱🔥 v1.5.24 is out 🚀 #MobileSecurity @fridadotre
#AndroidSecurity #iOSsecurity Huge thanks to @n0ps13d Check the changelog 👇👇👇 https://t.co/IlzzZLFqH1
github.com
Runtime Mobile Security (RMS) 📱🔥 - v1.5.24 is out 🎉🎉🎉 CHANGELOG 🌟 Full support for Frida 17+! (Huge thanks to @saullocarvalho for the #153 ! 🥳) 📦 Updated various other dependencies INSTALLA...
1
10
52
release of our new paper (w/ @inzo____) which resulted in CVE-2025-64525: Astro framework and standards weaponization from path-based middleware protection bypass to potential SSRF & XSS + full bypass of CVE-2025-61925 on @astrodotbuild
https://t.co/xTO55gNFu4
12
83
347
TOOL RELEASE: Detect plagiarized code even when variable names change and comments disappear. Vendetect uses semantic fingerprinting to catch copied code that traditional tools miss.
blog.trailofbits.com
Vendetect is our new open-source tool for detecting copied and vendored code between repositories. It uses semantic fingerprinting to identify similar code even when variable names change or comments...
0
25
80
Sometimes, SQL injection is still possible, even when prepared statements are being used. Our researcher @hash_kitten has written up a blog post about a novel technique for SQL Injection in PDO’s prepared statements:
slcyber.io
Searchlight Cyber's Security Research team details a Novel Technique for SQL Injection in PDO's Prepared Statements.
1
79
291
Get your FREE RankSight Score! With actionable plan Unveil your site's future visibility & get your definitive blueprint for top ranking in AI Search. No more blind spots. #RankSight #AISEO #LLMViz #DigitalMarketing
1
2
3
إطلاق النسخة التجريبية من منصة آجُرّوم، منصة لإعراب الجمل والنصوص العربية بالذكاء الاصطناعي مع التدقيق النحوي. تطوير هيثم بن حليمة. https://t.co/rAVQI0W1A0
3
10
28
If you're using chatgpt/AI for solving "every single" security research challenge, then you're not a security researcher anymore, you're a Chatgpt/AI operator. #skipchatgpt
0
1
2
After 2 years from the last release, APKiD v3.0.0 is out !🔥 - "Black Hawk edition" 📃 Changelog: https://t.co/gZsWgRyQtJ 🐍 Pypi package: `$ pip install --upgrade apkid` Thanks to @AbhiTheModder for the stunning work 🙌
github.com
The following SDK got improvements, rules and fixes: Ahnlab V3 Engine (packer/anti_root) Appdome (ELF Aarch64) AppGuard packer (ELF/APK) Arxan (DEX) AY literal obfuscation Beebyte (DLL) BlackObfus...
0
16
43
When choosing a new habit many people seem to ask themselves, “What can I do on my best days?” The trick is to ask, “What can I stick to even on my worst days?” Start small. Master the art of showing up. Scale up when you have the time, energy, and interest.
114
642
4K
🖥️Learn about root detection techniques on Android and how to bypass them in our latest blog: https://t.co/9fKs26Xl3T ☑️Found this interesting? Our courses offer more in-depth insights. Check them out here: https://t.co/n5WRBcePIM
#MobileSecurity #AndroidSecurity #Jailbreak
0
9
37
🚀 To celebrate the upcoming Azure Red Team Expert cert, we're launching the first Cloud PEASS: Azure PEASS! 🔎 It gets Azure/Entra tokens, finds all your permissions, highlights sensitive ones HackTricksAI and tells you how to privesc! 👉 https://t.co/2bfhcf4itb
#hacktricks
github.com
Contribute to carlospolop/CloudPEASS development by creating an account on GitHub.
2
139
456
Introducing https://t.co/NWz6mFk0w1, a small POC code that detects known root-related apps by attempting to launch their activities and monitoring security exceptions. Strengthen your app’s security by identifying potential root access attempts. #AndroidSecurity #RootDetection
github.com
Small POC code that detects known root-related apps by attempting to launch their activities and monitoring security exception. - apkunpacker/RootAppDetector
1
7
47
I've talked to enough web3 SRs to know that your auditing methodology is your bread and butter. This means that you are not only focusing on understanding new bugs. But also make sure that the bugs you've found once upon a time will be found every single time. On your worst
3
3
34
First project in the line: A software cost estimator based on Figma design files: considering nb of screens and the complexity, other factors will be added by time
7
7
30
Made it to top 10 contributors to Servo this year, this is probably the thing I'm most proud of in my life so far as a developer, More to come in the future!
2
4
20
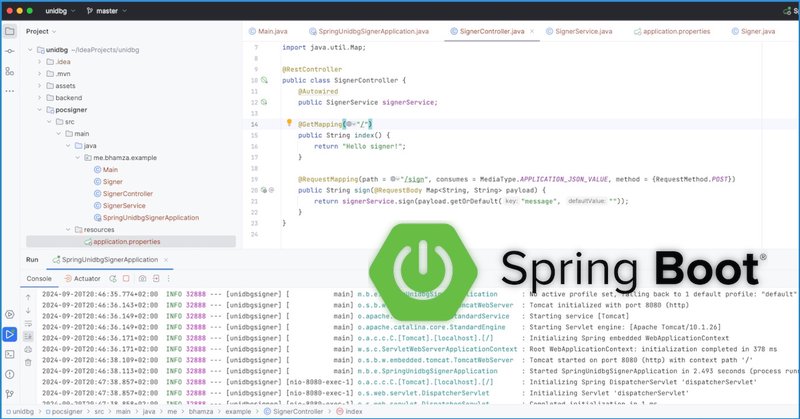
Previously, I covered how to use #unidbg from scratch to emulate an #Android native lib. The PoC was basic & slow. In this new blog, I'll demonstrate where the bottleneck is, and how we can make it production-ready by using Spring boot https://t.co/lHVvkbKfCh
#mobilesecurity
bhamza.me
Introduction In the last blogpost, we covered how to use unidbg from scratch to emulate an Android native library. As some might have noticed, the Proof of Concept code is not production ready as it...
0
20
55