bcoles
@_bcoles
Followers
726
Following
45
Media
27
Statuses
199
` rm -rf /* `
Joined January 2011
Open source projects are usually welcoming of pull requests. Don't let your dreams be dreams.
2
8
40
Here is our 0day for kernelCTF🩸 - 82k bounty - quickest submission ever - all instances pwned😎 https://t.co/0sb11m8ITD Disclaimer: We apologize for abusing the red black tree family. Turning grandparents against grandchildren is only acceptable in the context of pwn😤
syst3mfailure.io
CVE-2025-38001 is a Use-After-Free vulnerability in the Linux network packet scheduler, specifically in the HFSC queuing discipline. When the HFSC qdisc is utilized with NETEM and NETEM packet...
Exploit write-ups for our 🚨latest 0-day🚨and the tragedy that swept the red black tree family dropping soon 👀 Here is a tiktok style video for those of you with no attention span thanks to slop and social media. Turn on the audio!!!
0
76
309
An introduction to Software Defined Radios. A thread for beginners on: 1. What a SDR is 2. What you can do with SDRs 3. How it plays a role in the security/hacking world 4. How it’s used in ham radio. 5. How to choose/buy one 6. Link to more reading material 0/21
26
290
2K
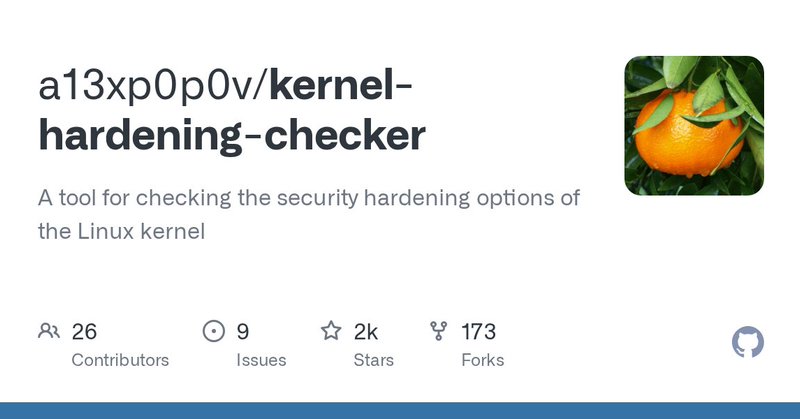
Big new feature in kernel-hardening-checker: now it supports checking the Linux kernel security parameters for RISC-V ⚡️ (in addition to X86_64, ARM64, X86_32, and ARM). I've spent many weekends on this. Thanks to @_bcoles for the contribution ⭐️ https://t.co/QWDLQIO4wi
github.com
A tool for checking the security hardening options of the Linux kernel - a13xp0p0v/kernel-hardening-checker
2
33
129
Too Subtle to Notice: Investigating Executable Stack Issues in Linux Systems https://t.co/hVNRltXmVs
0
6
23
KernelSnitch: Side-Channel Attacks on Kernel Data Structures Paper by Lukas Maar et al. about using a timing side-channel for leaking addresses of exploitation-relevant kernel structures. https://t.co/G30BwPJxYy
1
74
286
🆕 Check out our latest publication on DMA attacks via SD cards! 💾 The article was written by our researcher Gesser. ➡️ https://t.co/I4ujGaggJ2
3
39
77
I've written a post on SELinux and some public bypasses for Android kernel exploitation. It's especially relevant for Samsung and Huawei devices due to their use of hypervisors. Check it out here:
klecko.github.io
This post aims at giving an overview of what SELinux is, how it is implemented, and how to bypass it, from the point of view of Android kernel exploitation.
10
131
417
Also, to temper some concern about @evilsocket recent research... His bugs are in a thing that none of you should have installed so when it's published, please just uninstall that junk. Hopefully the response of the developer shows how badly you need to remove it.
5
26
187
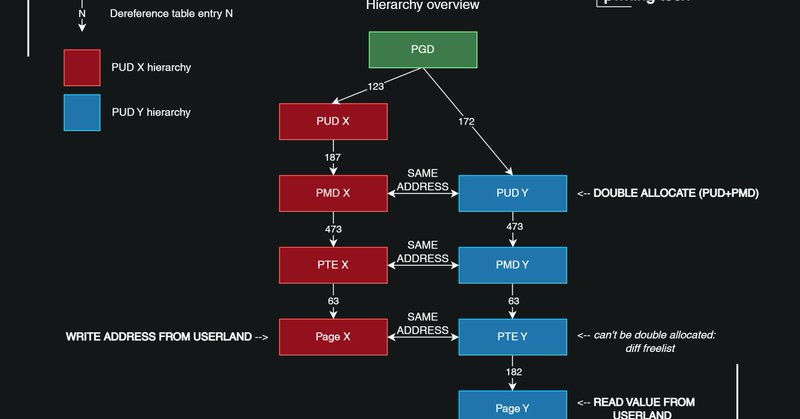
Exciting news! 🚀 Just dropped my blogpost unveiling the universal Linux kernel LPE PoC for CVE-2024-1086 (working on v5.14 - v6.7) used for pwning Debian, Ubuntu, and KernelCTF Mitigation instances, including novel techniques like Dirty Pagedirectory 🧵 https://t.co/zFimVzjgYB
pwning.tech
A tale about exploiting KernelCTF Mitigation, Debian, and Ubuntu instances with a double-free in nf_tables in the Linux kernel, using novel techniques like Dirty Pagedirectory. All without even...
12
272
786
Nice #KASLR break by @p1k4l4 for x86_64 kernels with Xen support (Debian and Ubuntu by default). Xen symbols are included in the kernel ELF .notes section and exposed world readable via SysFS (/sys/kernel/notes) since 2007 (pre-KASLR). Added to KASLD: https://t.co/bui5JxSxHN
github.com
I'm excited to announce that the technical analysis and the exploit of my CVE-2023-6546 (ZDI-24-020) Linux Kernel GSM Multiplexing Race Condition LPE is now available on : https://t.co/bk4yjCMtdl Happy Reading #Cybersecurity #Vulnerability #CVE #InfoSec #exploit #Security
1
7
28
CVE-2023-38408: Remote Code Execution in #OpenSSH's forwarded ssh-agent @qualys does it again!🔥 https://t.co/0sj5e5oGTG
0
26
90
pretty cool UAF in the handling of stack expansion in kernels 6.1 - 6.4
0
12
47
New timing attack on Intel CPUs, a side channel Meltdown using the EFLAGS register.
1
4
16
Support for #EntryBleed prefetch #KASLR bypass (CVE-2022-4543) added to KASLD - https://t.co/NDUxBpxtG5 Should work for Intel x86_64 CPUs (with KPTI enabled or disabled) and AMD x86_64 CPUs with KPTI disabled. Uses Will's proof of concept code: https://t.co/covFlIZQzd
3
9
13
Exploiting CVE-2022-42703 - Bringing back the stack attack
2
38
104
Blog: SETTLERS OF NETLINK: Exploiting a limited UAF in nf_tables (CVE-2022-32250) against the latest Ubuntu (22.04) and Linux kernel 5.15 - by @saidelike , @alexjplaskett and @FidgetingBits - https://t.co/3XHuzQ5mBj
1
65
150
CVE-2022-32250 (CVE-2022-1966) - A 6 year old bug in the Linux kernel exploited by @nccgroupinfosec EDG @saidelike @fidgetingbits @alexjplaskett Vuln write-up: https://t.co/x5GNztfBgt Exploit write-up coming soon.
3
83
204
SpiderFoot 4.0 is now out! Our biggest release in years: 🧠Correlation engine & define your own rules in YAML ✨37 predefined correlation rules reporting interesting findings 🎯8 new modules for popular security tools https://t.co/FXfWys4WDr
#OSINT #infosec #threatintel
intel471.com
Get the intelligence you need to detect, prevent & respond to cyber threats. Read the Intel 471 cyber threat intelligence blog.
1
35
92