James Woolley
@Xtrato
Followers
2K
Following
522
Media
38
Statuses
429
Interested in Network security and Technology
Herefordshire, England
Joined March 2008
RT @jarrodWattsDev: Someone just won $50,000 by convincing an AI Agent to send all of its funds to them. At 9:00 PM on November 22nd, an A….
0
5K
0
Seen these @DeterTech_UK Armadillos in quite a few places over the past couple of years. I would love to test the security of them! They look really interesting.
0
0
3
Recently started using a T-Beam LORA radio. I live in an area where there aren't any others around. I was very surprised to see just now another one nearby apparently onboard FR1175 to Portugal. Even managed to send a quick message and get a reply. #meshtastic #lora
0
0
10
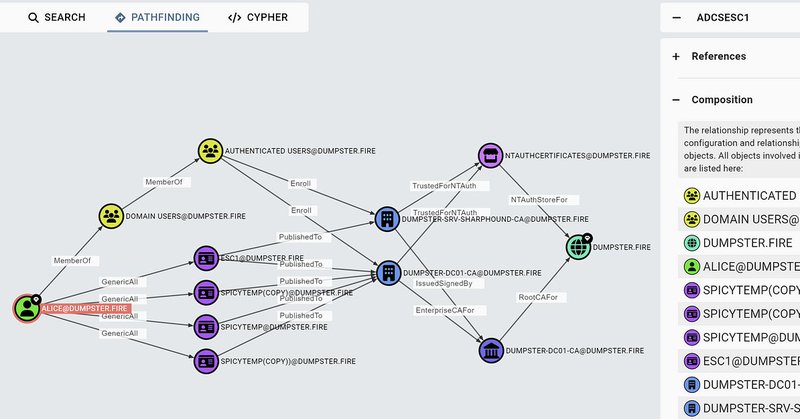
RT @Jonas_B_K: ADCS attack paths in BloodHound! 🥳. This blog post breaks down the implementation of the ESC1 requirements and guides you on….
posts.specterops.io
Since Will Schroeder and Lee Christensen published the Certified Pre-Owned whitepaper, the BloodHound Enterprise team at SpecterOps has…
0
119
0
RT @techspence: My goto AD toolbelt:. PowerView (custom).PrivescCheck (custom).PingCastle.ScriptSentry.Spray-Passwords (custom).SpoolSample….
0
115
0
RT @0xor0ne: Home router (SOHO) hacking.Presentation slides (HITB2023).Credits @NCCGroupInfosec. "Your not so Home Office - SOHO Hacking at….
0
142
0
RT @Kostastsale: This is a pretty nice graphic explaining how Kerberos Auth takes place. Useful to have as a reference when you have to e….
0
426
0
RT @bltjetpack: After about a year of work in off-hours, S3Scanner has been rewritten in Go! 🎉. Check out the newest version here: https://….
0
30
0
DLL hijacking using cscapi.dll loaded by explorer.exe. It's a very basic example and a good one to try in a lab if new to the DLL hijacking process. I've done a short write-up about it if interested.
ja.meswoolley.co.uk
Once privileged access has been achieved on a target machine the next step tends to be maintaining persistence. If the target is restarted or a new user logs in, you want to maintain access to the...
0
0
0
RT @DailyDarkWeb: Penetration-List. A comprehensive resource for testers, covering all types of vulnerabilities and materials used in Penet….
0
125
0
RT @BushidoToken: 🆕 Blog - Investigating SMS phishing text messages from scratch 🔍. A guide to practice doing some research for budding ana….
0
100
0
RT @7h3h4ckv157: BypassAV 🔥📢. This map lists the essential techniques to bypass anti-virus and EDR. #infosec #Hack….
0
116
0