Daniel
@VirtualAllocEx
Followers
7K
Following
14K
Media
93
Statuses
4K
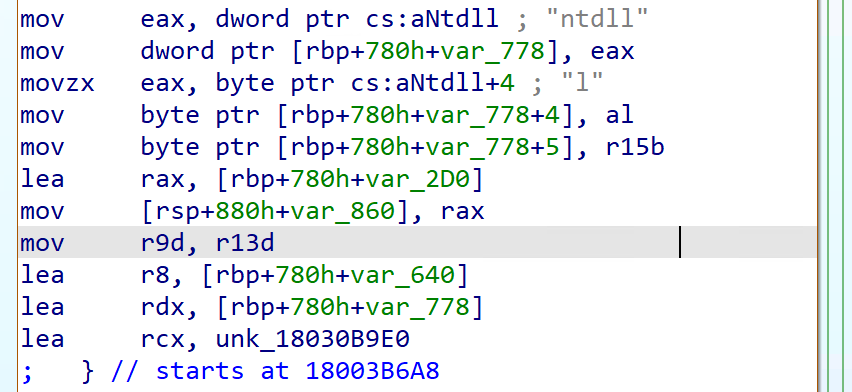
Finally, the first printed copy of the script for my 4-day in-person workshop "Endpoint Security Insights: Shellcode Loaders & Evasion Fundamentals". In about 1000 pages, students learn step-by-step and in a very practical way how to build and debug various types of evasive
11
28
220
RT @7etsuo: 🧵1/n Jerry Cain from Stanford University explains pointers and structs in C, showing a clever way to access struct fields. This….
0
376
0
RT @TJ_Null: Ever wanted to spin up a GOAD environment in VMware ESXi? . Well I decided to dig into it and I wrote a step-by-step guide to….
netsecfocus.com
Setting Up and Installing GOAD or GOAD-Light on VMware ESXi
0
58
0
RT @TrainSec: CrowdStrike and the Formidable BSOD – Pavel Yosifovich (.
scorpiosoftware.net
Adventures in Coding, Internals and Learning
0
28
0
RT @sh4dy_0011: Here’s the second part of my blog series on Compiler and LLVM internals, where I’ve explained the following concepts:. 1. B….
sh4dy.com
IntroductionIn the first part of my blog series on compilers and LLVM, I provided a brief introduction to compiler fundamentals and LLVM. We also wrote a simple LLVM analysis pass to print function na
0
207
0
RT @BalthasarMartin: Today at #Troopers24 we released Certiception – the ADCS honeypot we always wanted to have. Blog: .
github.com
An ADCS honeypot to catch attackers in your internal network. - srlabs/Certiception
0
163
0
Microsoft Defender's use of a specific Attack Surface Reduction (ASR) rule to block executables such as .exe, .dll or .scr based on prevalence or trusted list criteria is quite interesting. #redteam
5
20
63