Milos Constantin ♏(@Tinolle hachyderm.io )
@Tinolle
Followers
3K
Following
69K
Media
3K
Statuses
57K
#Cybersecurity, #Cisco, #Data, #Malware, #Privacy, #Hacking, #E2EE, #Cyberwar , #IoT..
Worldwide & Italy
Joined November 2009
ClickFix Gets Creative: Malware Buried in Images https://t.co/nJTSJ9XT8x
huntress.com
Stop cyberattacks with the Huntress Managed Platform. Get 24/7 SOC-backed EDR, ITDR, SIEM, & Security Awareness Training for enterprise-grade protection across all your environments
0
0
0
Native Secure Enclave backed ssh keys on MacOS https://t.co/IS7BuSgBdZ
gist.github.com
Native Secure Enclaved backed ssh keys on MacOS . GitHub Gist: instantly share code, notes, and snippets.
0
0
0
GitHub OSINT: The Ultimate Reconnaissance Methodology Guide | by D4rk_Intel | Nov, 2025 | Medium
preciousvincentct.medium.com
GitHub OSINT: The Ultimate Reconnaissance Methodology Guide Table of Contents Introduction: GitHub as an OSINT Goldmine Methodology Framework User & Organization Discovery Repository Intelligence …
1
35
158
Tor switches to new Counter Galois Onion relay encryption algorithm https://t.co/Uda37HnMIw
bleepingcomputer.com
Tor has announced improved encryption and security for the circuit traffic by replacing the old tor1 relay encryption algorithm with a new design called Counter Galois Onion (CGO).
0
0
0
The SHA1-Hulud npm mess keeps growing, so we added additional detections for it today - new YARA rules by my colleague @marius_benthin in our public signature-base - cover bun_environment.js / setup_bun.js and the malicious preinstall script variants from the Wiz / Aikido
github.com
YARA signature and IOC database for my scanners and tools - Neo23x0/signature-base
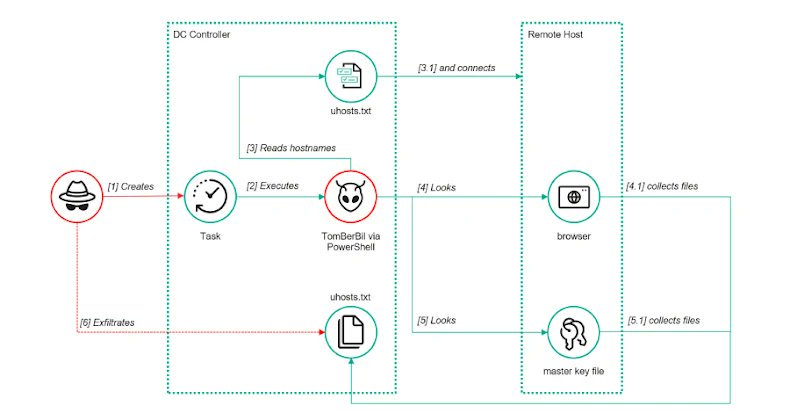
We used to fight worms on the OS level. Slammer, Blaster, Conficker.. all that stuff Now we get the same behaviour one layer up - inside the software ecosystems we trust every day NPM tokens, transitive deps, weak account hygiene, zero visibility… and suddenly a
2
64
226
We no longer have any active servers in France and are continuing the process of leaving OVH. We'll be rotating our TLS keys and Let's Encrypt account keys pinned via accounturi. DNSSEC keys may also be rotated. Our backups are encrypted and can remain on OVH for now. Our App
177
1K
6K
It's not possible for GrapheneOS to produce an update for French law enforcement to bypass brute force protection since it's implemented via the secure element (SE). SE also only accepts correctly signed firmware with a greater version AFTER the Owner user unlocks successfully.
2
34
652
Exploiting Deep Links for RCE in Mobile Applications https://t.co/sq3Ewq0iP4
medium.com
In this blog, we will see how we can exploit a deeplink to achieve an RCE
0
0
0
Researchers claim 'largest leak ever' after uncovering #WhatsApp enumeration flaw Two-day #exploit opened up 3.5 billion users to myriad potential harms..#privavy , #security .!? https://t.co/kcMOJiomHP
theregister.com
: Two-day exploit opened up 3.5 billion users to myriad potential harms
0
0
0
If you must use WhatsApp, remove your profile photo, strip extra text, and lock down your privacy settings. Read the full story: https://t.co/oB5A0Z0KXN 5/5
theregister.com
: Two-day exploit opened up 3.5 billion users to myriad potential harms
1
13
62
Security researchers say a design flaw in WhatsApp’s contact-lookup feature has enabled what they call the “largest data leak in history”, exposing billions of phone numbers without breaking encryption. Normally the lookup process would incur rate limits, normally... 1/5
20
93
368
IACR Nullifies Election Because of Lost Decryption Key https://t.co/i1egFbpG0E
schneier.com
The International Association of Cryptologic Research—the academic cryptography association that’s been putting conferences like Crypto (back when “crypto” meant “cryptography”) and Eurocrypt since...
0
0
0
Messaging Interoperability: #WhatsApp enables third-party chats for users in #Europen #UE #privacy
https://t.co/RiD36U0qNz
about.fb.com
The DMA requires Meta to give people using WhatsApp in Europe the option to connect with people using third-party messaging services that have chosen to
0
0
0
We used to fight worms on the OS level. Slammer, Blaster, Conficker.. all that stuff Now we get the same behaviour one layer up - inside the software ecosystems we trust every day NPM tokens, transitive deps, weak account hygiene, zero visibility… and suddenly a
11
84
317