Edo Maland
@screetsec
Followers
806
Following
298
Media
10
Statuses
89
ꜱᴇɴɪᴏʀ ꜱᴇᴄᴜʀɪᴛʏ ᴄᴏɴꜱᴜʟᴛᴀɴᴛ / ᴘᴇɴᴇᴛʀᴀᴛɪᴏɴ ᴛᴇꜱᴛᴇʀ | ᴏꜱᴇᴘ | ᴏꜱᴄᴘ | ᴏꜱwᴘ | ᴏꜱwᴇ | ᴄʀᴛ | ᴄʀᴛᴘ | ᴄʀᴛᴇ | ᴄʀᴛᴏ | ᴇᴡᴘᴛxᴠ2 | ᴇᴄᴛᴘxᴠ2 - ᴡᴀɴɴᴀʙᴇ ʀᴇᴅ ᴛᴇᴀᴍᴇʀ
Joined January 2020
RT @_EthicalChaos_: Working on a new tool that will be ready soon. One thing I can say from the research. if your environment leverages….
0
97
0
Gotcha, 𝗦𝗲𝗰𝗿𝗲𝘁.𝘁𝘅𝘁 in My Hands! ✊. I'm happy to share that I've achieved the OSEP certification from @offsectraining !.
7
3
65
RT @_xpn_: Quick POC this evening looking at how LAPS (v2) passwords are stored and decrypted on Active Directory (tl;dr, msLAPS-EncryptedP….
0
186
0
RT @cyb3rops: If you're a read teamer and want your work to have a higher impact, I recommend the following: . 1. put yourself in the persp….
0
48
0
I earned a badge from Zero-Point Security! Thanks @zeropointsecltd, the lab exams are well-designed, enjoyable, and challenging. If you want to explore and use Command and Control (C&C) like Cobalt Strike, I absolutely recommend it!😜.
0
2
17
RT @_vivami: Bypassing CrowdStrike, Microsoft Defender for Endpoint etc. for fun. not profit .
0
569
0
RT @Yanir_: (10/10) Read about the full discovery here >
orca.security
AutoWarp is a critical vulnerability in Microsoft Azure Automation Service that allows unauthorized access to other customer accounts using the service.
0
142
0
RT @_nullbind: Great blog on Azure SAS Token privilege abuse:
netspi.com
Extract credentials and identify opportunities for deeper access into an application's cloud storage during a web application penetration test in Azure.
0
20
0
RT @ManasH4rsh: This repo contains almost everything about appsec. Refer this and you should have enough idea about appsec:). https://t.co/….
github.com
A curated list of resources for learning about application security - paragonie/awesome-appsec
0
67
0
RT @Kostastsale: I created a #CyberChef recipe to ease the extraction of URLs from the word document (.doc & .docm) which download #Emotet.….
0
257
0
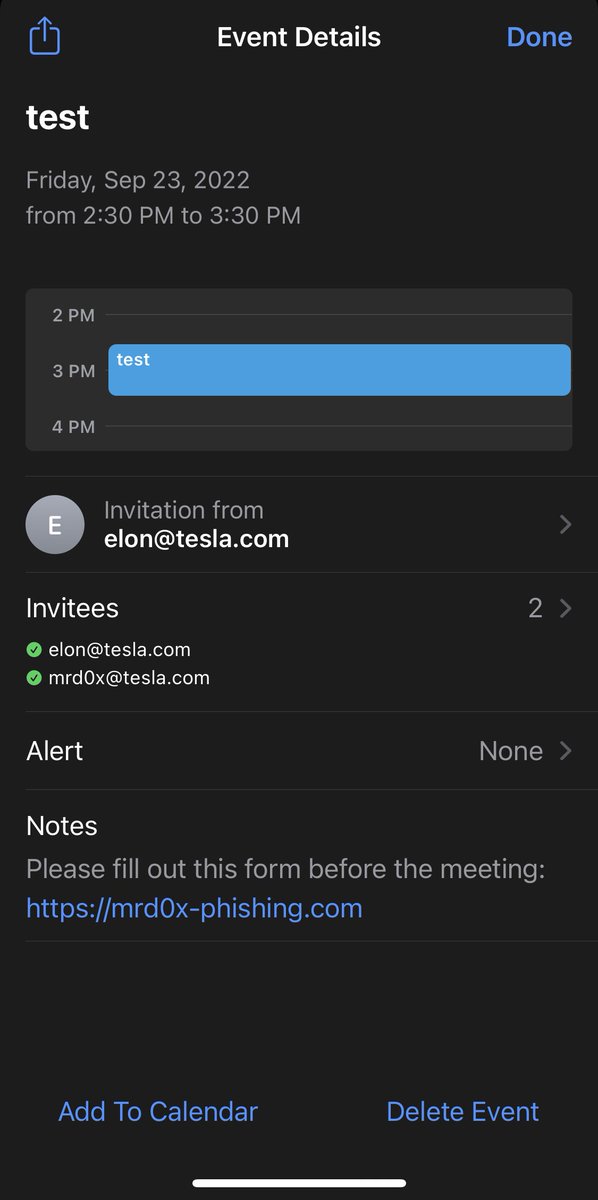
RT @mrd0x: Here I bypassed Defender AV by making:. eyb files as .exe . faq files as .dll. I'm sure this can work on other security solution….
0
503
0
RT @VbScrub: Rubeus is a great command line tool for performing various Kerberos attacks: But I don't use it often….
0
90
0
RT @mcbazza: Red-Teamers:. [lazy]People like me use Notepad++ as a note-taking thing. We create a 'new', then never get around to saving th….
0
439
0
Hi folks, I would like to share a free ebook about my recon workflow, tools, POV, & some idea. Leastwise, this might work & help to increase the effectiveness when doing pentest, red team & bug hunting. Thank & hope you like it, download on #bugbountytips
1
15
24
RT @Six2dez1: I'm proud to release my recon suites review. Again, thanks to all the developers who make it easy for all hackers and researc….
pentestbook.six2dez.com
0
97
0
RT @_wald0: (1/5) Here's my last #FF and "best of" list for 2020:. Best defense-oriented blog post: Restricting SMB-based lateral movement….
blog.palantir.com
Palantir’s recommendations for defending your network
0
78
0