Sathwik Ram Prakki
@PrakkiSathwik
Followers
976
Following
362
Media
99
Statuses
167
Sr. Security Researcher @Seqrite/@quickheal | APT Hunting | Malware | Darkweb | Threat Intelligence | Opinions are my own
Joined December 2011
New Research Blog: "Goodbye HTA, Hello MSI: New TTPs and Clusters of an #APT driven by Multi-Platform Attacks". #SideCopy expands targeting from Government, Defense, Maritime sectors to Railways, Oil & Gas, and External Affairs. #XenoRAT #SparkRAT #CurlBackRAT. #IOC in link below
#DISGOMOJI #APT36 #TransparentTribe.vmcoreinfo.txt.4c52bb770d7b8639e1f305f908dbc800. Password (Golang Downloader).4eaa6a69c9835c29ce8d39734e5d3d5f. #Opendir #APT.campusportals[.]in. Hidden URLs hosting #SideCopy payloads on same domain. IOCs in new blog:.
1
57
143
#APT36 #TransparentTribe #APT #Phishing. GRANT OF INTERVIEWS MEETINGS ETC TO THE STAFF SIDE BY OFFICERS IN MOD HQ ORGANIZATIONS.desktop.3447e49d4644079498d843e09151fdb0. #Poseidon.1c831f3fd2ec0aa5cc201666139ac992.b24a0a48162559eb5b1d820656883a9f. #C2.64.227.189.57.178.128.204.138
#APT36 #TransparentTribe #APT. [1/2]. Agenda Points of Joint Meeting On Counter Terrorism.ppam.7fa5095bfa9ba6e6718ade6fae4332bb. Do Letter by Chief of Naval Staff(CNS) Dated 17 Jun 25.desktop.db9044c6f93df2b9bccd89ed2ea5ed96. govin.sorlastore[.com. "C:/Users/BEAST/". @500mk500
1
6
22
#APT36 #TransparentTribe #APT #Phishing. 2eb008aad8675060c20268d13ff05816.indianarmy[.]nic[.]in[.]nominationdrdo[.]report/index. Uploaded from PK. @500mk500
#APT36 #TransparentTribe #APT #Phishing. MoS Defence Letter to DRDO Secy and Scientist.pdf.4ba06a36414616803339a3d4810542d2. drdo[.gov.in.nominationdrdo.report. Created: 2025-07-02. @500mk500
0
6
19
#APT36 #TransparentTribe #APT #Phishing. MoS Defence Letter to DRDO Secy and Scientist.pdf.4ba06a36414616803339a3d4810542d2. drdo[.gov.in.nominationdrdo.report. Created: 2025-07-02. @500mk500
#APT36 #TransparentTribe #APT #Phishing. Strategic Operational Directives For Armed Forces and DSPUs During ongoing War Escalation.pdf.18dc83cd8b64ccecbcc6b5c20a8d4306. CN=ksm
1
8
19
We presented our research at #FIRSTCON25 in Copenhagen this week on UNG0002 operations (CobaltWhisper & AmberMist) targeting South and East Asia. Met awesome folks, got good questions/feedback. Thanks to the organizers for such a community driven event!
We ( @PrakkiSathwik & me) presented our research on Cobalt Whisper & UNG0002( campaigns related to it) at @FIRSTdotOrg at Copenhagen! Met some cool folks such as @Gi7w0rm , collected some conference swags from @TeamT5_Official , research & presentation to be released soon!
1
0
4
#APT36 #TransparentTribe #APT. [1/2]. Agenda Points of Joint Meeting On Counter Terrorism.ppam.7fa5095bfa9ba6e6718ade6fae4332bb. Do Letter by Chief of Naval Staff(CNS) Dated 17 Jun 25.desktop.db9044c6f93df2b9bccd89ed2ea5ed96. govin.sorlastore[.com. "C:/Users/BEAST/". @500mk500
#APT36 / #TransparentTribe Go-based malware . File: myprogram.exe.33e1da22fb1068c73c033e3bc6bd3f1e.C2: modgovin.onthewifi[.]com:11520. File: output.exe.12c7e30db0c3eb636d11702baf254c0a.C2: 101.99.92[.]182:9080. defence-nic.3utilities[.]com.drdo-mss.serveirc[.]com. #Malware #ioc
1
7
23
#APT36 #TransparentTribe #APT. List of Active OGW,s.xlam.5018fab207ba76bcfd2abed1ac46c60e. #CrimsonRAT.nivnrgvs rnigam.948571781f0a6edfd6d9357441fbfbb8.33ac03a2a13d5870261233349fc9aef0.6c3dcb8f513f46eabed0d1564c065ec6. 185.174.101.86.arvnd.duckdns[.org.7523,8927,15868,22528,26567.
#APT36 #TransparentTribe #APT. [1/2]. Opportunities for cources at DRDO.ppam.b4150532e8de73eb52e541ce986a4e73.28cbbb4d10ec990512d476c8f51ce09a. malf[.zip #ELF #SideCopy.91431e672343594d4bfd4affe28111a4.- contains #CDUSBModule #AresRAT. #CrimsonRAT #C2 ref:.
0
10
28
#APT36 #TransparentTribe #APT #Phishing. Strategic Operational Directives For Armed Forces and DSPUs During ongoing War Escalation.pdf.18dc83cd8b64ccecbcc6b5c20a8d4306. CN=ksm
@500mk500 @solostalking @Cyberteam008 + zahcomputers[.]pk[.]modpersonnel[.]support. Spoofing "ZAH Computers".
1
6
21
#PhishingKit #APT.*.onlinenic.in.net. 25+ subdomains impersonating Indian government entities (both central & states like Maharashtra, Bihar, UP). IOCs: Similar to *.egovservice.in from blog below. #APT36 #TransparentTribe #SideCopy #Phishing. @500mk500
New Research Blog: "Goodbye HTA, Hello MSI: New TTPs and Clusters of an #APT driven by Multi-Platform Attacks". #SideCopy expands targeting from Government, Defense, Maritime sectors to Railways, Oil & Gas, and External Affairs. #XenoRAT #SparkRAT #CurlBackRAT. #IOC in link below
1
7
29
#APT36 #TransparentTribe #APT. Seeking Project complettion report of Industry 4.0.desktop.9d9e782952ea203952b95f88a207759d. hxxps://drive.google.com/file/d/1QeMiiM_CdwVpIzZhcu88XqRbMWM1Uy03/view?usp=sharing. id=1xJa6v7mBw5gDbCds6khSWOTq3J4nvFkf.(Same URL for "muffin.txt" below)
#ToRat used by #APT36 #TransparentTribe. [1/2]. Prev by Chinese #BackdoorDiplomacy #APT. #ELF #Golang #TOR #RPC #UPX.143.110.184.169/bhjk/client_linux.d65265c6dee357ede3df7167747a2d2b.b8f29c15966b3a27264a162068db4451. muffin.txt.00ab003ec55b559fa44d4b74d2e4d876. 16 #C2 commands
0
5
21
#SideCopy #APT. 2.hta.d81608fffc905efa19ddff046c689cca. file.hta #GetaRAT.97bc9f61855c32b84154cfea23063379. useH.hta #ReverseRAT.4cd25b06c42536a4bfe32b7676601c3e. #C2.dns.educationportals[.]biz/dailyworkout.37.1.198.72:5863. AS28753 (Leaseweb Deutschland GmbH) 🇩🇪. @500mk500
#SideCopy #APT #Opendir. Windows version based HTA.-7/10/11.php. useT.hta / startT.hta.#GetaRAT.C2: 72.11.156.132:5863.CN=WIN-P9NRMH5G6M8 #APT36. useH.hta.#ReverseRAT.C2: checkdailytips.servehttp[.com/dailyworkout. Lures.-Climate Change.docx.-Professional.docx.-Research Work.docx
1
10
21
#APT36 #TransparentTribe #APT. [2/2]. #Poseidon #Mythic #ELF #Golang.142.93.38.174/visual-bin.143.110.184.169/binary-key.b6a0e627d1da72143cda79879aa471ea.a555e05d2d9a26bf0371471cfdde7e3f. #C2 AS14061 (DIGITALOCEAN).138.197.163.42.64.227.134.175. @500mk500.
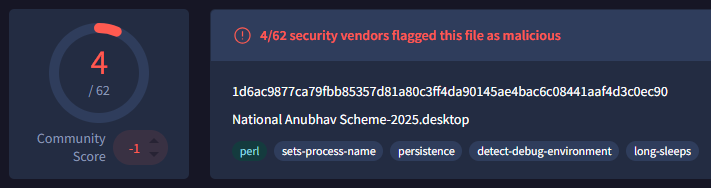
#APT36 #TransparentTribe #APT. National Anubhav Scheme-2025.desktop.7f66e223c91d5440a21bf42c7f82f007. National Anubhav Scheme-2025.pdf.hxxps://drive.google.com/file/d/174qkH9F5yo7BCCEa-5pGnYnf0293E92n/view?usp=sharing. Downloads same #ELF payloads
0
3
7
#ToRat used by #APT36 #TransparentTribe. [1/2]. Prev by Chinese #BackdoorDiplomacy #APT. #ELF #Golang #TOR #RPC #UPX.143.110.184.169/bhjk/client_linux.d65265c6dee357ede3df7167747a2d2b.b8f29c15966b3a27264a162068db4451. muffin.txt.00ab003ec55b559fa44d4b74d2e4d876. 16 #C2 commands
"Collegiate on Make Projects Scheduled 2025-26.desktop" seen from India: 3c012b14ad76bc2bd3a6e7c99c8f50a8c28c025750e32aea007978e8a1db703d
1
17
70
RT @ElementalX2: New Research!. We have found an interesting campaign targeting an entity of Chinese telecom with….
0
66
0
2/24 outlook -> phishing, remaining👀. 05 03 25 in AM - P71.rar.ad1656fce572f42cbcf9fe618d82f15f. #APT36 #TransparentTribe #SideCopy.Continues to target Maritime sector #APT
#APT36 #TransparentTribe #APT. CDSDirectionsfortheTri-ServicesandCivilDept03June2025.pdf.18d9407cacf8483b7d4500ea5df426c8. CN=ksm
0
5
16
#APT36 #TransparentTribe #APT #ELF. [2/2]. #CDUSBModule .zip.bd5d57ee71bafd313096043948c092a6.myusb.8a2d2d01041b917b5110f5ad15320621.mycd.8190f71c32c9391b671e6c3e8b544391. #AresRAT #C2 #SideCopy in refs:.(pam-auth, letter). (1)(2)
The #TransparentTribe group used the Ares Python-based remote access trojan (#RAT), disguised as files related to the Linux PAM authentication system. #IOC: .185.123.102.180:41452 .
0
0
1
#APT36 #TransparentTribe #APT. [1/2]. Opportunities for cources at DRDO.ppam.b4150532e8de73eb52e541ce986a4e73.28cbbb4d10ec990512d476c8f51ce09a. malf[.zip #ELF #SideCopy.91431e672343594d4bfd4affe28111a4.- contains #CDUSBModule #AresRAT. #CrimsonRAT #C2 ref:.
#APT36 #TransparentTribe #APT. 29 May 2025.ppam.f27fac4c67f8ebf2f85f25252d90cb84. #CrimsonRAT.rmgevatc jvxhm.exe.7ab6bb1763b6faf61d29757070c730c0.50a35a2a139fefb11fcfe0153b996e76.4fe71eba46781f1d51f71809884edf19. C2.69.197.178.193.asatvm.duckdns[.org.15642,16853,23867,26261,29426
1
2
18
#APT36 #TransparentTribe #APT. National Anubhav Scheme-2025.desktop.7f66e223c91d5440a21bf42c7f82f007. National Anubhav Scheme-2025.pdf.hxxps://drive.google.com/file/d/174qkH9F5yo7BCCEa-5pGnYnf0293E92n/view?usp=sharing. Downloads same #ELF payloads
@500mk500 @IdaNotPro @IndianCERT @suyog41 + IPs #APT36 #SideCopy #APT.188.166.78.195.164.92.190.176.209.38.33.123.134.209.250.88.161.35.24.231. Hashes & IPs were posted by @malwrhunterteam & @Shad0w2311 threads. Drops #Poseidon and #AresRAT.
0
6
21
#APT36 #TransparentTribe #APT. CDSDirectionsfortheTri-ServicesandCivilDept03June2025.pdf.18d9407cacf8483b7d4500ea5df426c8. CN=ksm
Using the hunting techniques identified in our blog yesterday, we identified this new domain today:. mod[.]gov[.]in[.]defencepersonnel[.]support.
0
12
31