Cyber Team
@Cyberteam008
Followers
3K
Following
994
Media
140
Statuses
265
Threat Hunting | APT Tracking | Malware Analysis | Darkweb Monitoring "Unity is Strength"
Joined December 2022
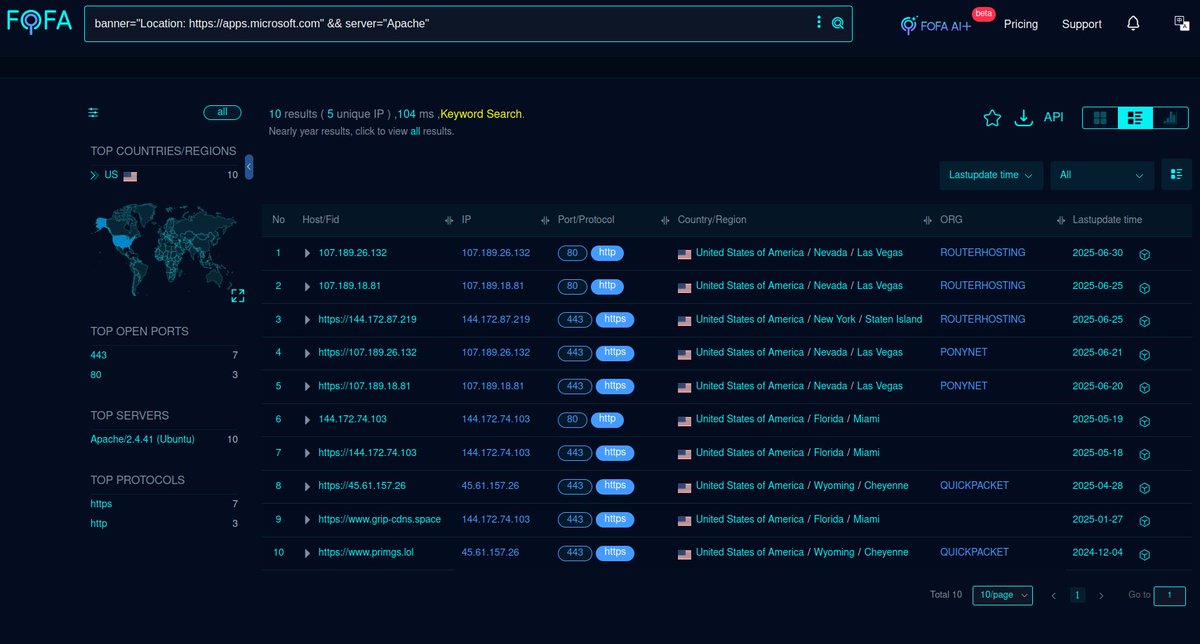
#Fofa Query for #APT37 / #RicochetChollima / #ScarCruft #APT. Query: banner="Location: && server="Apache". Link: Infra: #Malware #ioc #APT
1
8
39
#APT36 / #TransparentTribe Go-based malware . File: myprogram.exe.33e1da22fb1068c73c033e3bc6bd3f1e.C2: modgovin.onthewifi[.]com:11520. File: output.exe.12c7e30db0c3eb636d11702baf254c0a.C2: 101.99.92[.]182:9080. defence-nic.3utilities[.]com.drdo-mss.serveirc[.]com. #Malware #ioc
0
9
32
RT @fofabot: Exciting news!🥳🥳.We've launched FOFA AI beta ver, an automatical attack surface discovery platform powered by AI Agents. If i….
0
15
0
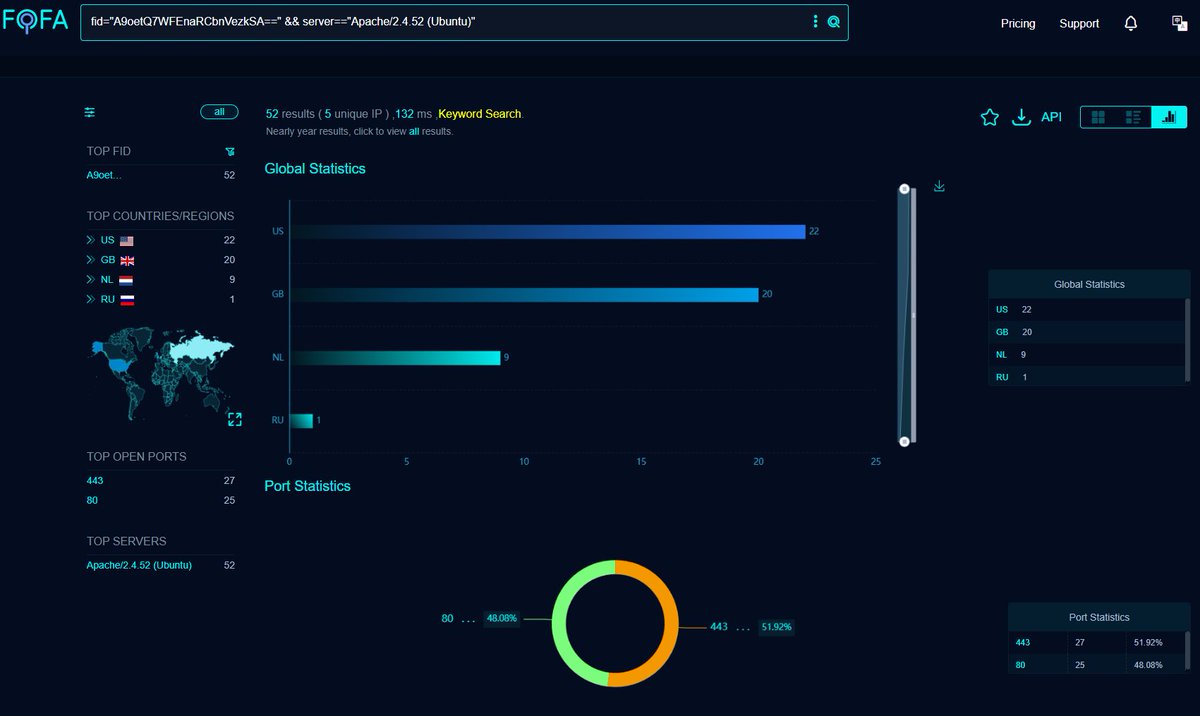
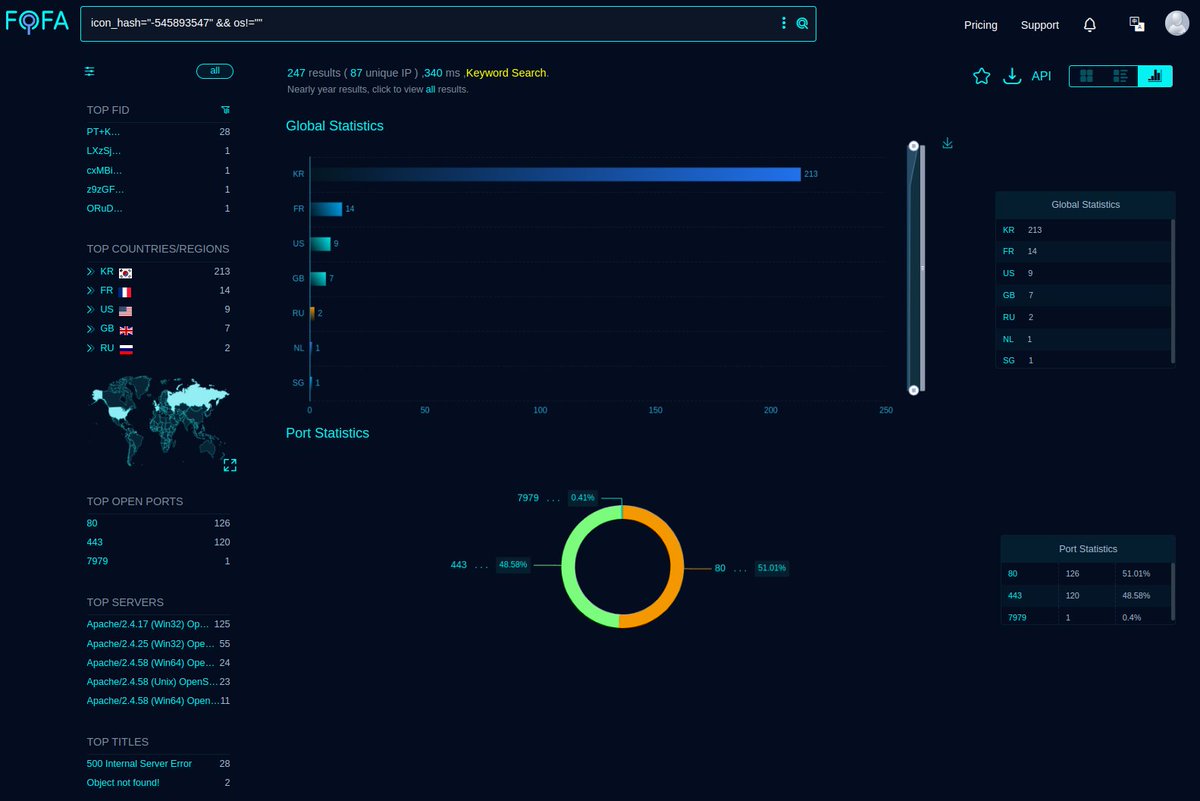
#Fofa Query for #APT42 / #GreenCharlie / #CharmingKitten Infra. Query: fid="A9oetQ7WFEnaRCbnVezkSA==" && server=="Apache/2.4.52 (Ubuntu)". Link: Infra: @500mk500 @MichalKoczwara #Malware #ioc
0
10
40
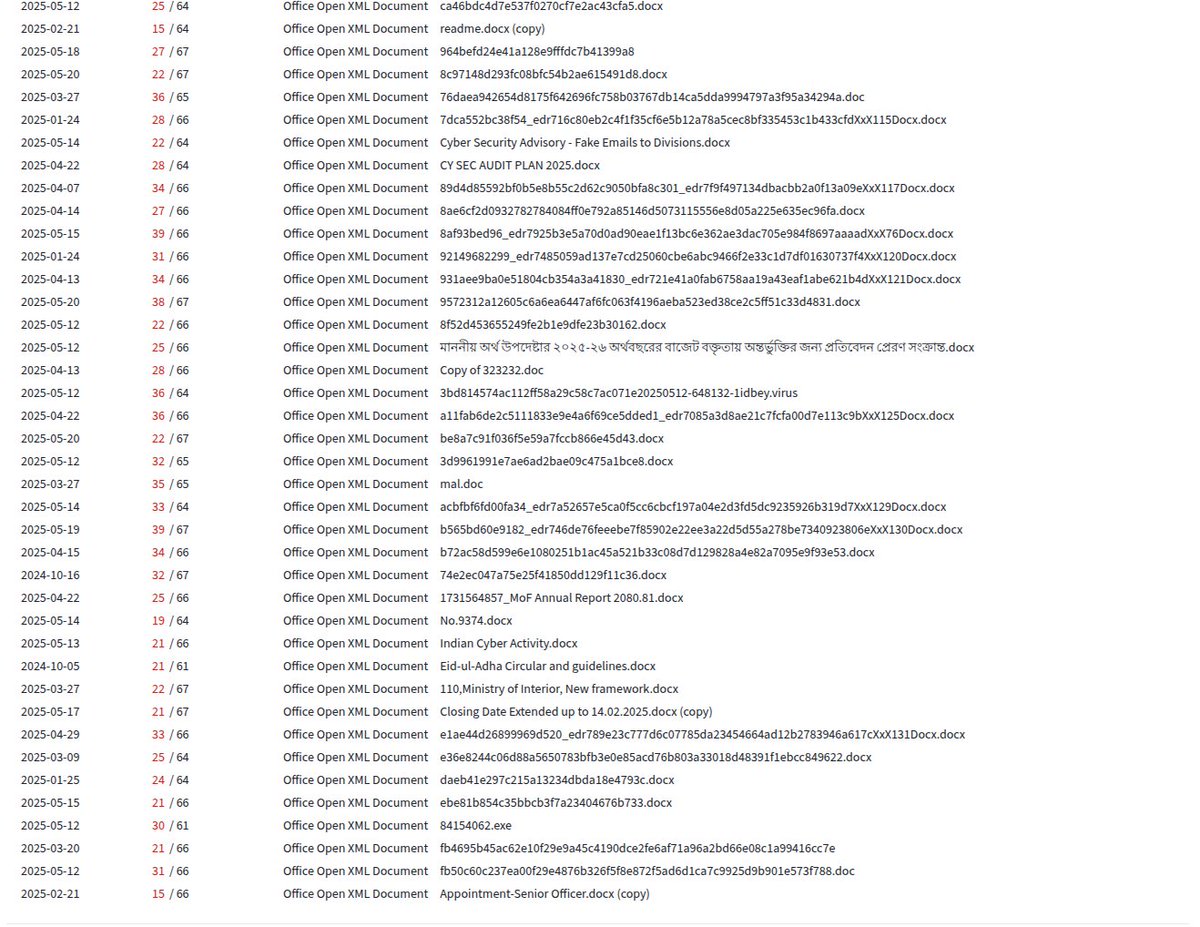
#Sidewinder #APT is dropping its favorite RTF file while launching multiple phishing campaigns. Target countries: 🇱🇰 🇧🇩 🇵🇰 🇳🇵 🇲🇲 🇲🇻 🇮🇩. We have consolidated all infra and are available at: . @500mk500 (for update if any new infra) #Malware #ioc
2
14
32
#CrimsonRAT Payloads of #APT36 / #TransparentTribe. imrthirs irndga.exe (02).25c0eb541818b569c0448b32ce5f911e.91ed5b3797fef26a8d0ad35277b10686. jimasvrn imthv.exe.fec10dbb7d3afa0a4714345b3f96c08d. C2: 212.56.45[.]254: {9525, 24224 & 28822}. signature: { infrwodao=command }. #RAT
0
15
47
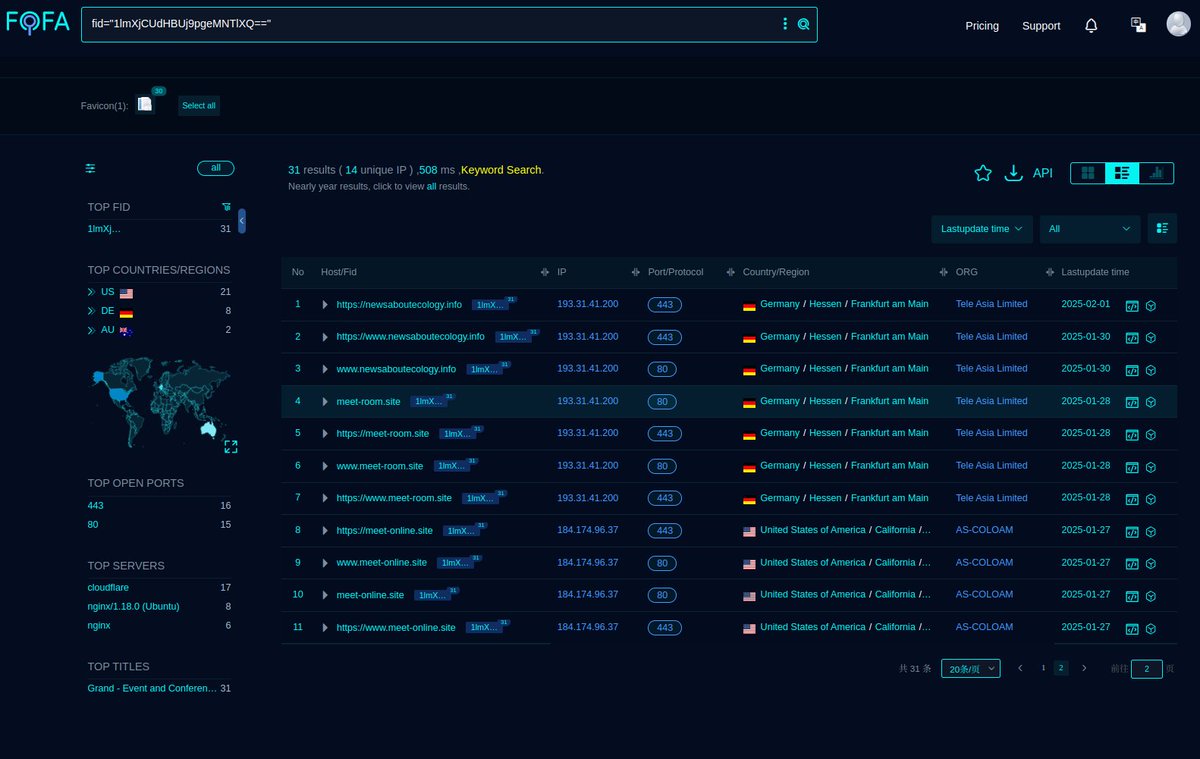
#Fofa Query for #APT35 / #CharmingKitten Latest Infra. #Query: fid="1lmXjCUdHBUj9pgeMNTlXQ==". Link: Infra (Latest): @MichalKoczwara @500mk500 #APT #Malware #IOC. Note: Most of the domains theme related to "meeting".
1
16
51
[2/2]. Infra:.185.235.137[.]195:3311.185.235.137[.]195:3309.server1.securenesst[.]com.securenesst[.]com.hxxps://expressholidays.co[.]in/ups/r.php. @500mk500 #APT36 #TransparentTribe #CrimsonRAT #Malware #ioc.
1
1
5
[1/2]. #APT36 / #TransparentTribe 's #CrimsonRAT Campaign through HTML Frame attack. File: presentation.accdb (it executes a VBA script).30908d3c69dc8aaa0368b3a3593eb66c. File: Syssm.exe (dropped by VBA script from "expressholidays[.]co[.]in").e948aa916d1f9f9b5bba72ad7de7e27f
1
10
32
#APT36 / #TransparentTribe dropping #ElizaRAT using CPL (Control Panel) file. File: Audit Objection's Document.rar (Pass-protected hosted on G-Drive).MD5: e7152c45fb4c2df442ef069d30daca40. File: Audit Objection's Document.cpl.MD5: 0f527665709f76a34b5612829293c849. #Malware #ioc
0
14
52
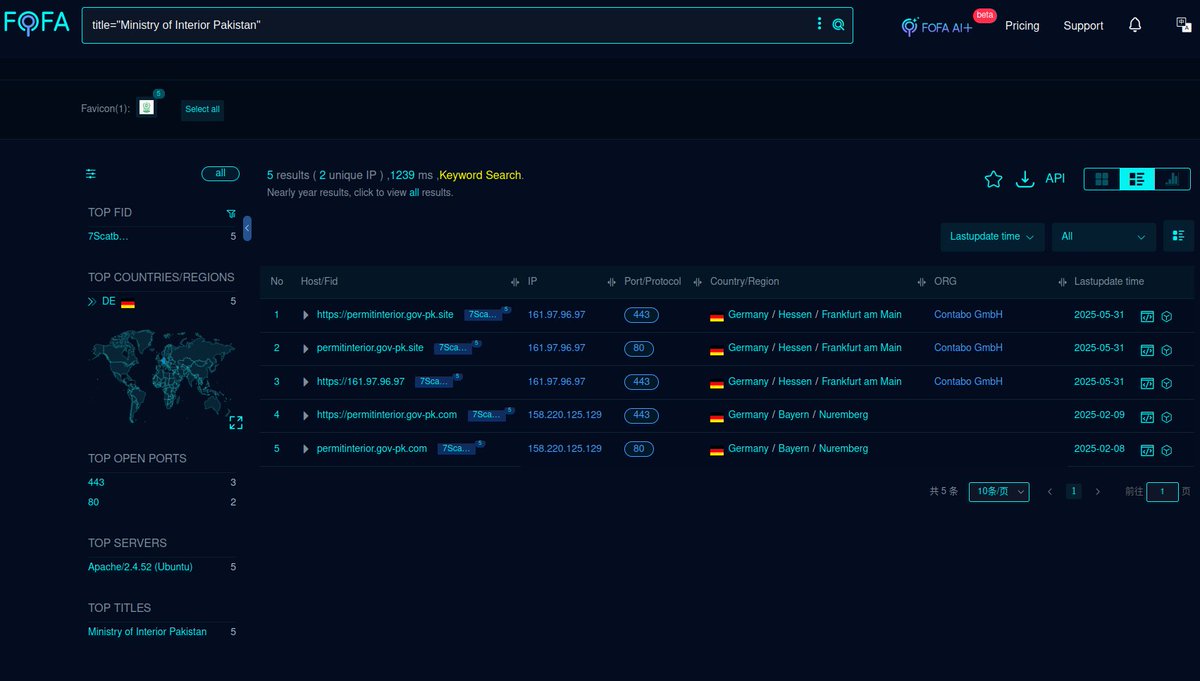
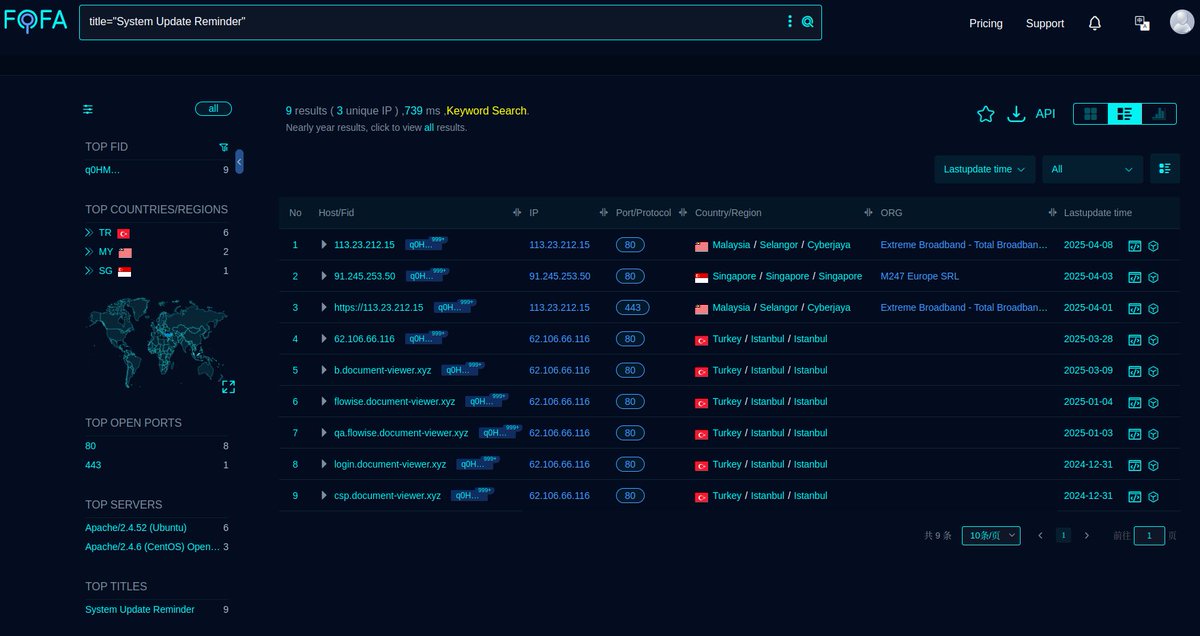
#Fofa Query for #MustangPanda #APT / #StatelyTaurus. Query: title="System Update Reminder". Link: Infra: Note: Some Infra enriched from VT. @500mk500 #Malware #ioc
1
20
75
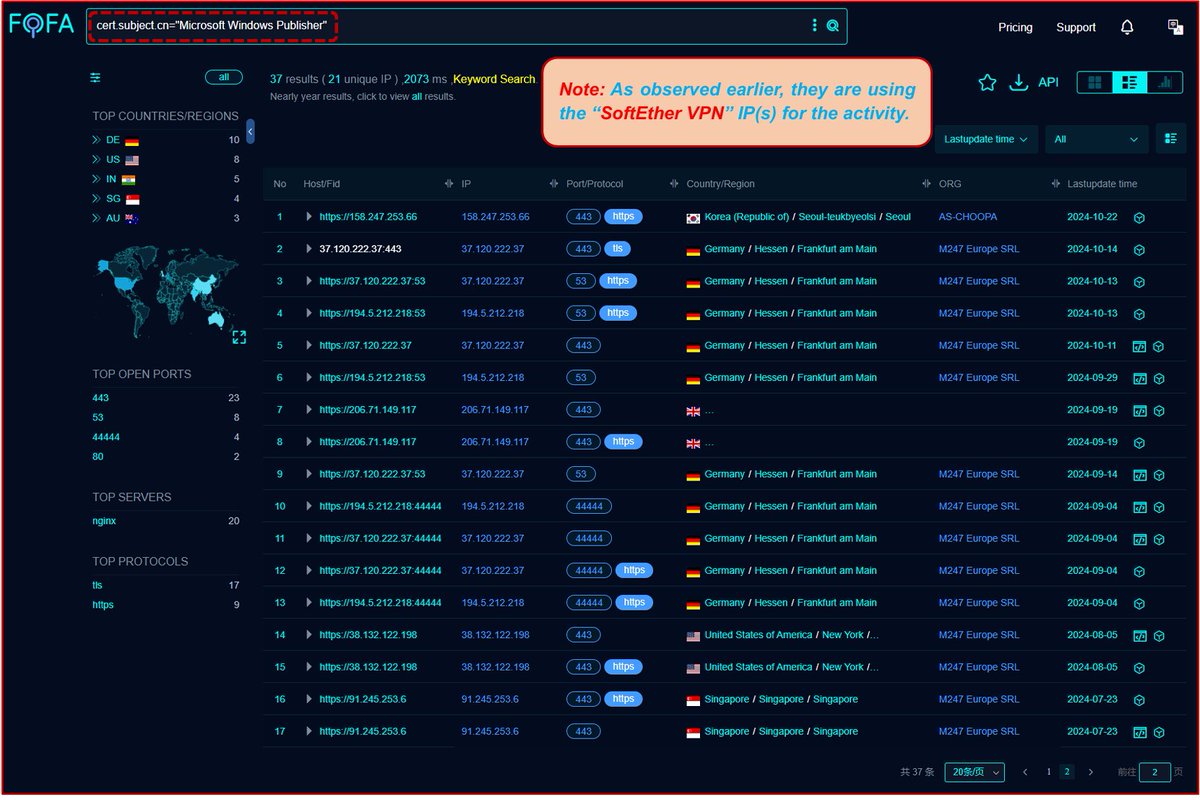
#Fofa Query for #NomadPanda / #RedFoxtrot #APT 's campaign using #ShadowPad Cluster. #Query: "Microsoft Windows Publisher". Link: Infra (as on 5th Apr): @500mk500 (for update pls) #Backdoor #Malware #ioc
2
14
46