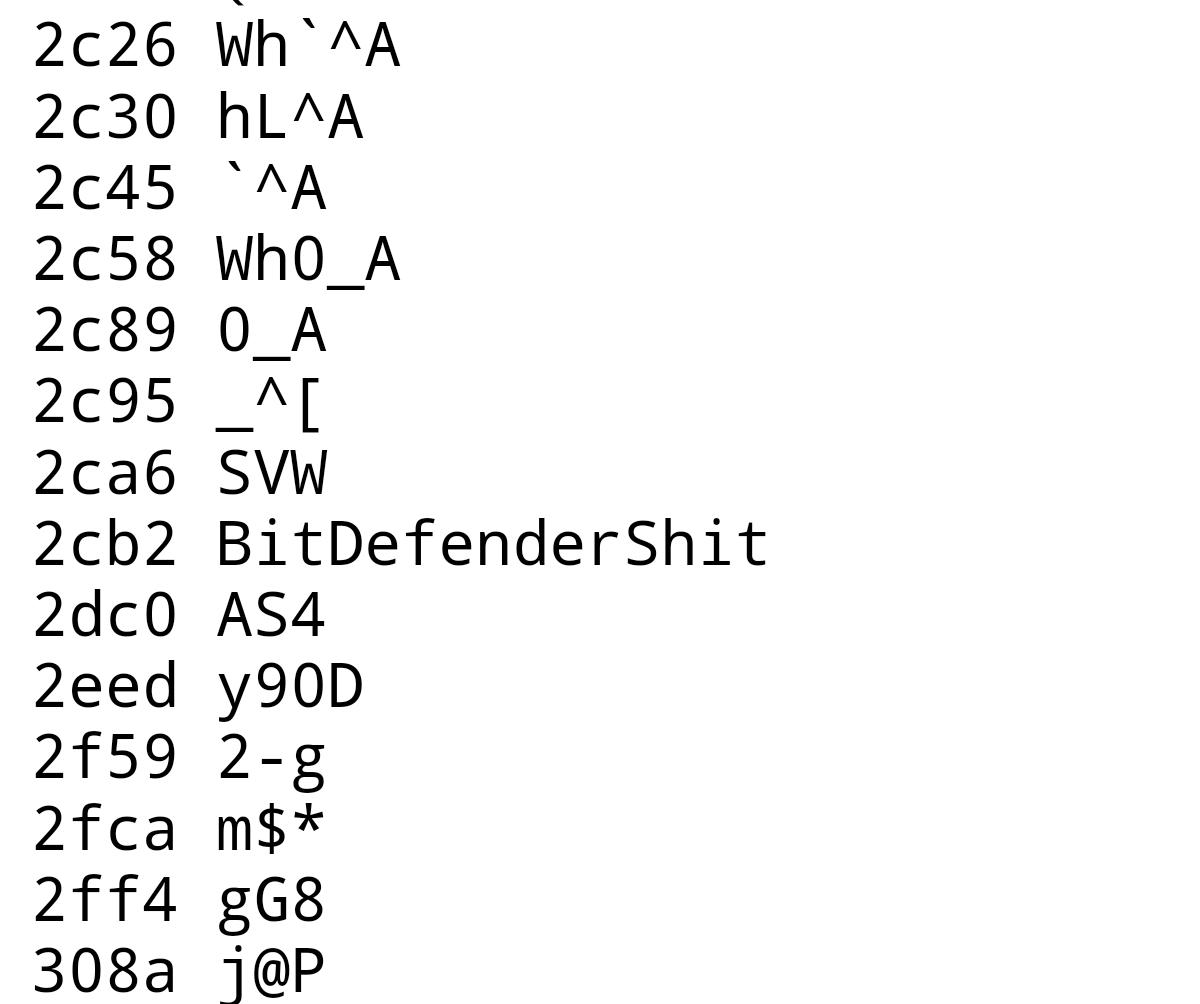
PhysicalDrive0
@PhysicalDrive0
Followers
16K
Following
0
Media
423
Statuses
23K
Malware Hunter / I've already taken the red pill!
Down The Wrong Rabbit Hole
Joined November 2010
RT @commial: Now, Sibyl can be called from @GHIDRA_RE ( or use it headless for function address discovering (https:….
0
58
0
RT @Dark_Puzzle: Circumventing Windows Defender ATP's user-mode APC Injection sensor from Kernel-mode : https://t.c….
0
93
0
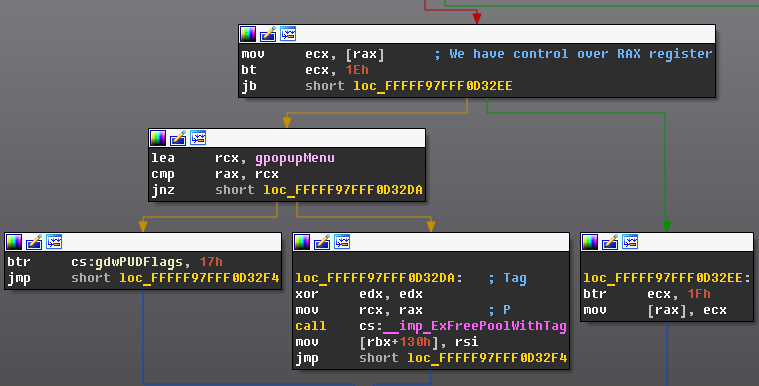
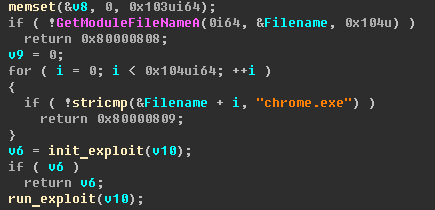
CVE-2019-5786 Chrome 72.0.3626.119 stable FileReader UaF exploit for Windows 7 x86.
github.com
FileReader Exploit. Contribute to exodusintel/CVE-2019-5786 development by creating an account on GitHub.
0
2
7
RT @360CoreSec: Microsoft fixed a Windows 0day (CVE-2019-0808) in Patch Tuesday. Our team constructed the POC and reproduced the vulnerabil….
0
180
0
RT @cBekrar: Google discovered a Chrome RCE #0day in the wild (CVE-2019-5786). Reportedly, a full chain with a sandbox escape: https://t.co….
chromereleases.googleblog.com
The stable channel has been updated to 72.0.3626.121 for Windows, Mac, and Linux, which will roll out over the coming days/weeks. Secur...
0
139
0
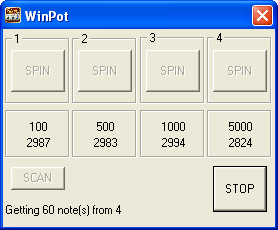
Meet #ATMPot - the ATM malware designed to automate the dispensing of cash from a popular range of ATM machines. The designers even went to the trouble of making the interface look like that of a slot-machine. Learn more:
2
12
13
A curated list of IDA x64DBG and OllyDBG plugins.
github.com
A curated list of IDA x64DBG, Ghidra and OllyDBG plugins. - GitHub - fr0gger/awesome-ida-x64-olly-plugin: A curated list of IDA x64DBG, Ghidra and OllyDBG plugins.
1
20
46
#KerrDown Sample SHA256 e56ffcf5df2afd6b151c24ddfe7cd450f9208f59b5731991b926af0dce24285a #APT32 #OceanLotus.
1
5
11
RT @insertScript: CVE-2018-16858 - My writeup about a RCE vulnerability via macro execution in Libreoffice:
0
143
0
#Zebrocy MD5 c9e1b0628ac62e5cb01bf1fa30ac8317
0
2
5
RT @AirbusSecLab: Version 1.1 of BinCAT, our static binary code analyzer for reversers, was just released, with long awaited AMD64 support….
0
149
0