Phantom Security
@PhantomOpSec
Followers
86
Following
2K
Media
6
Statuses
608
Web3 is under attack. We teach you how to defend OpSec audits•Threat modeling•Real-world attack breakdowns $70,000,000 in Secured Funds | DM for consulting
Joined October 2024
Elevating Web3 security. At Phantom Opsec, we're not just advisors we are your security partners. From tailored phishing simulations to comprehensive security awareness, we're elevating how protocols and individuals approach operational security in the web3 space.
1
1
1
RT @pcaversaccio: ok so there is another fake one from Hardhat; please always triple check the extensions you install:.- https://open-vsx[.….
0
36
0
These aren't some random attacks, stay vigilant and don't install anything you haven't verified.
🚨SlowMist TI Alert🚨. A community member recently reached out after interviewing with a Web3 team claiming to be from Ukraine. In the first round, he was asked to clone a GitHub repo locally — he wisely refused.🧑💻. 🔍Our analysis revealed the repo contains a backdoor:
0
0
2
RT @officer_cia: Someone fell victim to a phishing attack, signed a malicious transfer, and lost 3.05M USDT!. 1. Use tools like @RevokeCash….
0
29
0
All it takes is one powerful key, one lapse in control. Six days to set the trap, minutes to drain millions. Access is always the real vulnerability. If you're not securing your admin roles like crown jewels, you're already compromised.
Six days of setup, minutes of execution. A compromised @CrediX_fi admin account minted worthless acUSDC tokens, borrowed $4.5 million against phantom collateral, then shipped everything to Ethereum. Someone with the right access decided payday had arrived. Story below.
0
0
2
RT @PhantomOpSec: Zero-click, web-based exploit live in the wild. Just visiting the wrong site can compromise your iPhone. If you're on i….
0
1
0
RT @PhantomOpSec: AI-enabled phishing is entering a whole new phase:.✅ Deepfake voices.✅ Realistic pitch.✅ Legit-looking files. If your fun….
0
1
0
AI-enabled phishing is entering a whole new phase:.✅ Deepfake voices.✅ Realistic pitch.✅ Legit-looking files. If your funds touch your daily-use devices, you’re already exposed. Cold storage or get compromised.
🚨 A friend just suffered a $2m+ hack due to sophisticated social engineering . They impersonated @pauliepunt of Plasma using apparently AI generated audio which perfectly matched his profile offering an advisory role at Plasma. During the pitch which perfectly described the.
0
1
2
Zero-click, web-based exploit live in the wild. Just visiting the wrong site can compromise your iPhone. If you're on iOS, update immediately.
Urgent: Update iOS Now — A Dangerous Vulnerability Found in Safari and Chrome Browsers. Apple has released an emergency update for iOS 18.6 to address a serious security vulnerability. Hackers are already exploiting it — simply visiting a website can trigger the malicious code.
0
1
2
RT @PhantomOpSec: @IAMERICAbooted The quiet ones are the most dangerous. no ransom notes, no loud TTPs, just silent exfiltration over month….
0
1
0
Justice catches up, even in the wild world of crypto. You can phish, run, hide behind aliases…. But if someone keeps receipts, it will come back around. Props to those who stayed on it 💯.
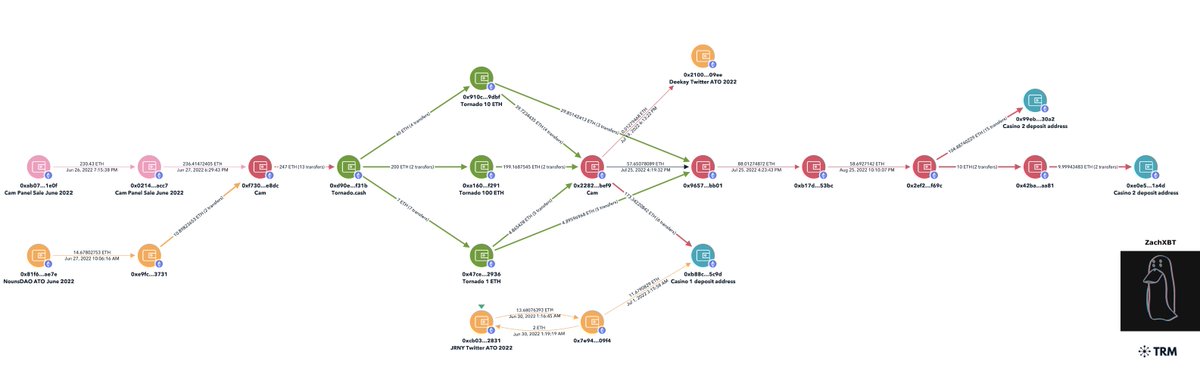
1/2 I am pleased to share that Cameron Redman was convicted today and ordered to pay restitution as a result of my investigation. In June 2022 X panel access was sold for 250 ETH which resulted in 10+ account compromises (JRNY, Beeple, Nouns, Zeneca, DeeKay, etc) and millions
0
0
1
RT @PhantomOpSec: The scariest attackers don’t lock your files, they silently live in your network, exfiltrating your IP for years. No dram….
0
2
0
The scariest attackers don’t lock your files, they silently live in your network, exfiltrating your IP for years. No drama. No noise. Just damage. If your IR team can’t read the subtle signals, you're in for a long painful ride.
Something about espionage groups most people fail to realize: they will be in your org, and you're highly unlikely to discover them. They don't do all the stupid things that ransomare groups, extortion groups, BEC actors, and other groups do. They just hang out and steal your.
0
2
4
RT @PhantomOpSec: @RektHQ @_WOO_X Hard truth:. If phishing keeps working, something's broken in team security culture. No tool or audit re….
0
1
0
RT @PhantomOpSec: Phishing is still the most reliable way in. No matter how strong your infra is, all it takes is one compromised device.….
0
1
0
Next @EthCC should be in Poland City.
Next time you visit Europe, be sure to check out Poland City, Poland - "Top Digital Nomad Destination" as recommended by DPRK IT Worker, Damian Mularz 💯
0
0
0