SlowMist
@SlowMist_Team
Followers
90K
Following
3K
Media
998
Statuses
4K
SlowMist is a Blockchain security firm established in 2018, providing services such as security audits, security consultants, red teaming, and more.
Joined April 2018
We previously warned about a Web3 interview scam involving a GitHub repo disguised as a legitimate open-source project (EvaCodes-Community/UltraX). A community member wisely refused to run the code during their interview. ✍️In our latest article, we dive deeper into the.
🚨SlowMist TI Alert🚨. A community member recently reached out after interviewing with a Web3 team claiming to be from Ukraine. In the first round, he was asked to clone a GitHub repo locally — he wisely refused.🧑💻. 🔍Our analysis revealed the repo contains a backdoor:
3
7
19
We’re thrilled to be an official partner of BUIDL_QUESTS 2025! 🤝. Let’s BUIDL safely — and shape the future of decentralized intelligence. 🚀. #Blockchain #AgentFi.
We’re excited to introduce SlowMist @SlowMist_Team as an official partner for BUIDL_QUESTS 2025!. SlowMist is a blockchain security firm established in January 2018. It was founded by a team with over ten years of experience in network security and has since become a renowned
0
1
11
🚨SlowMist TI Alert🚨. MistEye detected that @CrediX_fi has been exploited. The CrediX Multisig Wallet, 6 days ago, added an attacker as both Admin and Bridge via ACLManager. This enabled the attacker, acting in the Bridge role, to directly mint
🚨 SlowMist TI Alert 🚨. @CrediX_fi seems to have had a security breach. Their website has been disabled to prevent users from depositing. We are following up on this incident — stay alert!.
5
7
32
🚨 SlowMist TI Alert 🚨. @CrediX_fi seems to have had a security breach. Their website has been disabled to prevent users from depositing. We are following up on this incident — stay alert!.
1
1
11
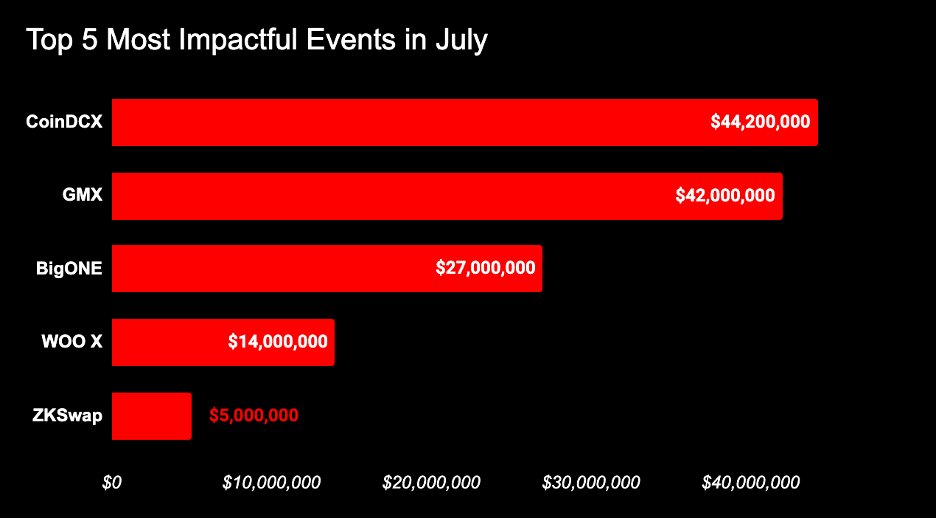
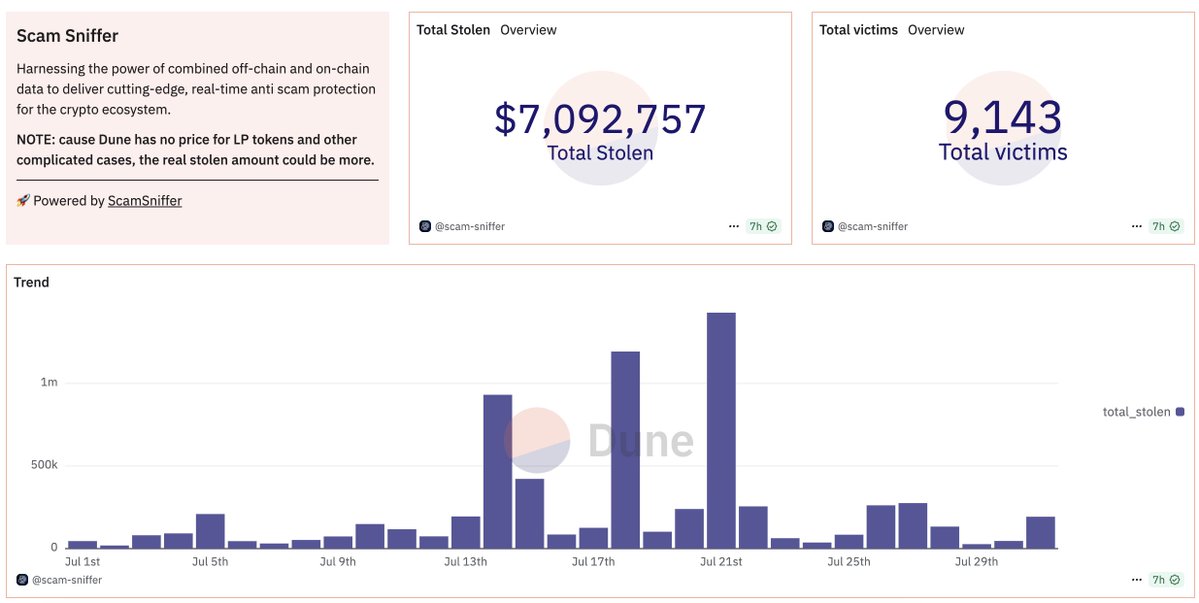
🚨July 2025 Web3 Security Recap🚨. 📊According to SlowMist’s Hacked (:.⚠️13 hacks ➡️ $140M lost.❄️$42.48M recovered/frozen. 🎣Phishing losses via @realScamSniffer:.9,143 victims ➡️ ~$7.09M stolen. Major incidents:.• CoinDCX lost $44.2M after malware was
1
6
20
👏 MistTrack now supports tracking and analyzing funds on @HSKChain!. Try it out 👉
misttrack.io
A crypto tracking and compliance platform for everyone. Core features include wallet risk scoring, transaction analysis, fund traceability, and address monitoring.
🚀We’re excited to announce that MistTrack now supports 18 blockchain networks, with the latest addition being @HSKChain!. 🔍Effortlessly track and analyze funds on HashKey Chain, including its thriving #stablecoin and #RWA ecosystem — all with MistTrack. 🕵️We’ll continue
1
1
5
We’re excited to support the Web3 Internship Program🚀🌐. This event brings together people from diverse backgrounds🌍, all heading toward #Web3. It’s a strong signal that this matters — we’re building a real bridge🌉 to the future of Web3. Proud to contribute to the internship.
7 月 25 日,我们正式发布了由 @ETHPanda_Org 与 @LXDAO_Official 联合发起的完全免费的「Web3 实习计划」。. 短短 72 小时内,我们已收到来自全球高校学生与职场转型者的近 190 份申请表!其中一半以上是在校学生!报名链接在下面,还在继续,即将关闭!.
5
3
23
🚨 Yet again, another case of stolen funds due to purchasing a hardware wallet through unofficial channels. The victim used a wallet pre-initialized by the scammer — meaning the attacker had full access to the seed phrase from the start. As a result, 4.35 $BTC was stolen. 🛑.
3
8
28
🚨SlowMist TI Alert🚨. MistEye detected that @SuperRare has been exploited. The root cause for this exploit was an incorrect permission check in the updateMerkleRoot function, allowing anyone to modify the Merkle Root and claim tokens. As always, stay vigilant!
9
9
67
🇭🇰SlowMist in Hong Kong!. Recently, our Hong Kong community lead @coding_toLex was invited to speak at the Web3 Literacy Program, hosted by 「Hang Seng Bank & SideBySide: Project Forward」. He introduced blockchain, crypto, online scams, and Web3 security in a clear and engaging.
1
0
16
Thanks to @TrustaLabs for trusting us and for their swift, responsible response. Security is always our top priority — stay vigilant.
Recently, there was an external scam involving an unverified third-party contract.(0x16d7c6f43df19778e382b7a84bcb8c763971a551) on the blockchain. Trusta and the official $TA token remain secure and intact, with no vulnerabilities or issues identified. Appreciate the help from.
1
0
10
🔥New challenge live on #Unphishable!. Fake job interviews remain one of the most effective lures in phishing campaigns — especially against devs and researchers.📁. Stay sharp, question every unsolicited “opportunity,” and remember: legit recruiters won’t send you .exe files.
🔥New Unphishable challenge just dropped: Fake Zoom Meeting Phishing. Job offers turned into attack vectors — a common tactic targeting developers. Challenge contributor: @SlowMist_Team . If you've been through a similar “recruitment” flow, check your laptop now. #Unphishable
3
1
11
🚨Attackers often distribute malicious files through #LinkedIn, #Discord, and #Telegram. To stay safe, here are key tips 🛡️:. 🔹 Beware of fake jobs asking you to run code from GitHub. Verify identities via official sites. 🔹 Always review unknown code & authors. Use.
🚨I fell victim to a job scam, my first encounter with a social engineering attack🚨 . I hope everyone can help spread this post so there are no more victims. I’ll explain the entire incident from my perspective and how I discovered it. 🚨 It all started on July 11 when I.
3
3
14