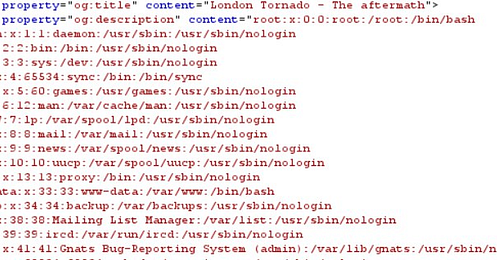
NULLKrypt3rs
@NULLKrypt3rs
Followers
94
Following
117
Media
5
Statuses
34
CTF Team || IIIT-Allahabad
Allahabad, India
Joined November 2018
Added a new technique in Patriot to identify suspicious CONTEXT structures used in the rop/callback chains of foliage, #nighthawk, #brc4, gargoyle, etc. https://t.co/QsYoHFlrgu
3
26
81
Thread - Confluence Blind OGNL Injection analysis from our limited java knowledge. From vulnerable sink to becoming admin of the confluence instance. #CVE-2022-26134. Tested on latest vulnerable version 7.18.0.
3
151
449
Open redirect vulnerability and how to use it "correctly" in bug bounty 🙃 https://t.co/O0uuj2msct
link.medium.com
I will tell you a story of how I chained multiple security issues to achieve RCE on several hosts of the Mail.Ru Group (or VK now).
32
402
1K
This PowerShell one-liner will open a visible IE browser in Windows 11: $(new-object -com internetexplorer.application).Visible=$true
as M$ said, IE should be totally removed from Win11 & redirect to M$ Edge. Fun Fact: attackers still can launch IE on Win11 by COM interface {0002DF01-0000-0000-C000-000000000046}
1
43
152
Interesting account takeover of the day. The site was hosting their https://t.co/i5o2oc49ez on amazonaws While resetting my password I have noticed that the host was getting passed in json body
12
71
289
No PKINIT? No problem! Thanks to team members Yannick and @lowercase_drm, you now have a way to (ab)use your ill-earned ADCS certificates even when domain controllers do not support PKINIT https://t.co/bE70PblkYq
2
98
183
Here are the slides for my talk « Delegating Kerberos to bypass Kerberos delegation limitation » 😈 at @1ns0mn1h4ck #INS22
https://t.co/fI76XQQmk0
16
233
596
Trying to learn security research and getting overwhelmed by all the details? I just published a guide showing my process for step-by-step analysis of a security feature: https://t.co/7k87w8DhFh
21
574
2K
New Interruptor 0.1 release 🔥 add Follow Thread 🥳, Kernel API constants usable by their names into hooks🥰, configurable output, smart modules/interrupts filtering https://t.co/eulUNxq9kR
0
13
45
[#thread 🧵] Last week in #Microsoft #PatchTuesday, a critical vulnerability was patched that theoretically allows attackers to achieve Remote Code Execution on a target #IIS server (CVE-2022-21907). I'll explain how it works in this thread ⬇️
3
38
126
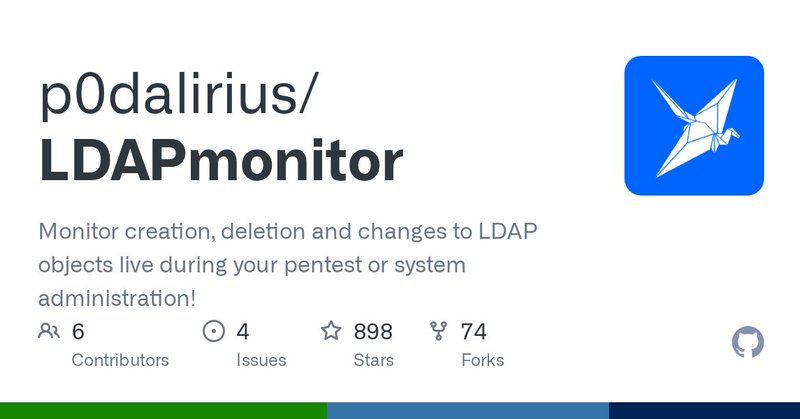
I'm proud to present a new tool, #LDAPmonitor! With this you can monitor creation, deletion and changes to LDAP objects live during your pentest or system administration! Lots of authentication types are supported, and output can be saved to a file. https://t.co/XJf5QKTLQy
github.com
Monitor creation, deletion and changes to LDAP objects live during your pentest or system administration! - GitHub - p0dalirius/LDAPmonitor: Monitor creation, deletion and changes to LDAP objects ...
12
191
478
Takeover an entire domain by resetting passwords! We detailed how to exploit CVE-2021-40539 on ManageEngine ADSelfService Plus in this blogpost https://t.co/craR84dtvv
@acervoise - @tiyeuse
synacktiv.com
How to exploit CVE-2021-40539 on ManageEngine ADSelfService Plus
0
56
141
Revisiting an old bug which paid off really well during a previous Red Team op. The good old Microsoft Exchange unauthenticated email relay. This was particularly impactful. Here's why: 🌶️Unauthenticated 🌶️No phishing infra needed 🌶️Emails land directly in user's inbox (1/4)
2
9
37
New Write-up on InfoSec Write-ups publication : "Finding My First Bug: HTTP Request Smuggling" #bugbounty #bugbountywriteup #bugbountytips
1
45
166
Containerd breakout PoC (@ChaosDatumz), the "glue" principle (@theluemmel), lockscreen bypass (@jonasLyk), VBox escape 0day (@Sauercl0ud), beacon shellcode generator (@ryanstvnson), browser backdoor (@_batsec_), nim obfuscation (@LittleJoeTables), + more!
blog.badsectorlabs.com
Containerd breakout PoC (@ChaosDatumz), the "glue" principle (@theluemmel), lockscreen bypass (@jonasLyk), VBox escape 0day (@Sauercl0ud), beacon shellcode generator (@ryanstvnson), browser backdoor...
0
9
17
b00t2root CTF ended! Hearty congratulations to team @ByteForc3, @Zh3r00 and @0x90r00t for bagging the top three positions! We would also like to thank our esteemed sponsors @offsectraining @vector35 for sponsoring the prizes. Adieu guys! See you all next year :)
0
3
16
15+ hrs into the CTF and we are seeing some intense competition here :P If you havent registered yet shoot here: https://t.co/91rNoi2tIt
#boot2r00tctf2020
0
5
12
Hola folks, With Hacka-demic in close sight, we are glad to announce the prizes and goodies awaiting the winners. Hoping the poll has added flavors to your curiosity on the possible themes, we are more than excited to witness your take on our themes. (1/2)
1
15
30