Uriel Kosayev
@MalFuzzer
Followers
6K
Following
8K
Media
524
Statuses
5K
Author of MAoS - Malware Analysis on Steroids & Antivirus Bypass Techniques | Cybersecurity Researcher | Keynote Speaker | Co-Founder @TrainSec Academy
Walking this world with God
Joined December 2017
🚀 It’s official — my new book is live on Amazon: MAoS – Malware Analysis on Steroids This book is not like the others. It’s built on years of raw, hands-on research, reverse engineering sessions at 3 AM, and real-world incident response cases. Inside, you’ll find full A–Z
53
206
1K
🚀 EDR Internals – Research & Development is LIVE Stop guessing how EDRs work. Learn how they actually operate — telemetry, detection logic, kernel internals & real-world bypasses. Built for malware analysts, detection engineers, red & blue teamers. 👉 Enroll here:
trainsec.net
EDR Internals hands-on workshop is designed to give cybersecurity professionals, malware researchers, and detection engineers a rare opportunity to explore how modern Endpoint Detection and Response...
3
24
160
It’s the season of giving… 🎁 Get FREE access to ANY model from the Dedalus API. Available until January 12th, 2026.
9
7
32
🎙️ New Podcast Episode – I was hosted by @HoffmanYaniv How does malware really work behind the scenes? I recently had the pleasure of being hosted by Yaniv Hoffman on his podcast, where we went deep into how modern malware operates in real-world attacks — not theory, not
0
3
8
🚀 It’s official — my new book is live on Amazon: MAoS – Malware Analysis on Steroids This book is not like the others. It’s built on years of raw, hands-on research, reverse engineering sessions at 3 AM, and real-world incident response cases. Inside, you’ll find full A–Z
53
206
1K
Did you know that the shortcut keys of CTRL-Win key-F brings up this? 🤔
0
0
1
See The Patriot Party’s bipartisan proposed legislation to fix our Healthcare system, fix Gun Violence Constitutionally and fix Immigration. All produced at the click of a button with our new Federal Policy Producing AI Coming Soon to EVERY American FREE of charge.
thepatriotparty.us
The Patriot Party Podcast: TRUTH & CONSTITUTION above all.
0
2
11
Final days of the TrainSec Black Friday event. Through 1 December, every individual course is 40 percent off using BF2025. If you want to sharpen your malware analysis, reversing or detection engineering skills but prefer starting with a single course instead of a full path, this
trainsec.net
Cybersecurity courses that are on Black friday sale.
0
0
8
🚀 MAoS just hit 1,000 reads on ResearchGate! Grateful to see researchers and security professionals diving into the book and using it in real-world work. More research and deep-dive content coming soon. 📖 https://t.co/wNDmG8Ypny
#CyberSecurity #MalwareAnalysis
0
0
5
It just warms my heart ❤️ #CyberSecurity #MalwareAnalysis #ReverseEngineering #Infosec #MAoS #TrainSec #OffensiveSecurity #Malware
0
1
4
New course drop! UART Hacking - Level II, Module 01. 15 classes. 15+ hours. Hands-on labs from pin ID to OT MITM, fault injection, and firmware extraction. Instructor: @The_H1tchH1ker Enroll: https://t.co/sELByf40ud
0
2
5
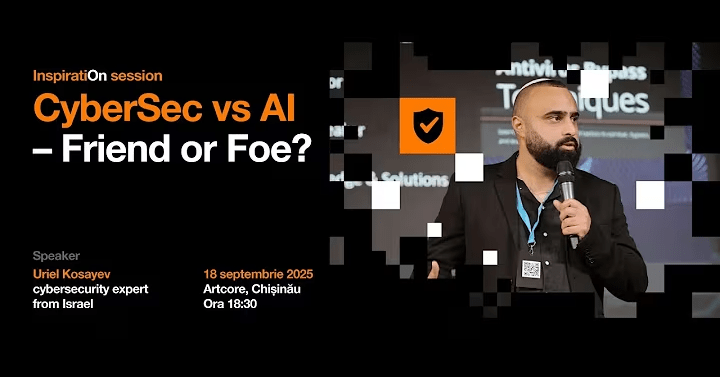
AI can defend or attack. In my latest talk at Orange Systems, I explored how AI is reshaping cybersecurity from both sides of the battlefield. 📖 Read more: https://t.co/fqbZGC939w
#AI #Cybersecurity #EthicalHacking #TrainSec #Awareness
trainsec.net
AI is not good or bad, it's a mirror. It reflects how we use it. During my talk at Orange Systems, I showed how AI can both defend and attack: from generating ransomware to helping build 200 detect...
0
1
5
This book isn’t for everyone. MAoS – Malware Analysis on Steroids is for those ready to go beyond theory — into the raw, unfiltered world of real malware dissection, evasion, and reverse engineering. In this video, I introduce what makes MAoS different — a book for serious
trainsec.net
The MAoS Bundle is your fast track to mastering malware analysis. From core concepts to hands-on reverse engineering, this bundle gives you the real-world skills needed to dissect malware with...
2
36
232
Lockmounts keep your rifles out of the hands of the unauthorized.
0
1
11
Diving into ‘MAOS - Malware Analysis on Steroids’ by Uriel Kosayev! @MalFuzzer
#CyberSecurity #MalwareAnalysis #ThreatIntel #DFIR
1
2
5
It’s finally here! 📦 Just received my own printed copies of MAoS – Malware Analysis on Steroids 🔥 There’s nothing like holding your work after months of writing, research, and late-night debugging. Get your copy here👉 https://t.co/wNDmG8Ypny
#CyberSecurity #MalwareAnalysis
12
57
626
Excited to announce our fourth sponsor — @TrainSec TrainSec is the Cybersecurity academy where pros train pros in Malware analysis, SOC, Windows Internals and Hardware Hacking. Trained by Pavel Yosifovich, the Windows internals guru, Uriel Kosayev, a world known security
0
2
4
🙏 Thank You for the Incredible Support! To everyone who bought, shared, messaged, or just cheered from the sidelines — thank you. The launch of MAoS – Malware Analysis on Steroids has been overwhelming in the best way possible. If you’ve read even a part of the book and found
1
1
3
Most “detox” saunas never show you what’s in the walls. I do, because what you sweat in matters. Our saunas use low-tox materials for people who take detox seriously. Tap through to learn more.
0
1
2
🙏 Thank You for the Incredible Support! To everyone who bought, shared, messaged, or just cheered from the sidelines — thank you. The launch of MAoS – Malware Analysis on Steroids has been overwhelming in the best way possible. If you’ve read even a part of the book and found
0
4
69
Be prepared 🔥 My inspiratiON session at Orange Systems will begin at 19:15 CET+1 (GMT+2) Visit the following link to watch it live: https://t.co/VGUEFm4gli
#cybersecurity #infosec #ai
0
0
2