Netlas.io
@Netlas_io
Followers
7K
Following
148
Media
315
Statuses
529
Stay ahead with updates on high-profile vulnerabilities, expert tutorials, essential safety tips, and the latest Netlas developments.
Joined November 2020
Dear Netlas Community Members,.We are seeking passionate authors to contribute to our cybersecurity blog. If you’re interested in sharing your expertise and insights, we welcome you to join us 🤝. ✍️ What’s in it for you?.• Competitive compensation in USDT — from $200 up to.
0
3
4
Pyramid of Pain: Measuring Adversary Disruption 🔺. In our new article, explore the Pyramid of Pain framework to understand which indicators cause the most disruption to attackers. 👉 Read now:
netlas.io
Despite its simplicity, the Pyramid of Pain is a powerful concept that shifts your mindset toward proactive defense. Let’s explore how it works in practice.
0
0
0
SOCMINT: Intelligence in the Social Media Era 🔍. Social media is more than just likes and shares — it’s a goldmine of public data. In our latest article we'll discover SOCMINT — how it differs from OSINT and what it can (and can’t) reveal. 👉 Read now:
netlas.io
How does Social Media Intelligence differ from OSINT? A review of the most popular SOCMINT tools, their true capabilities, and a few real-world cases.
0
1
0
CVE-2025-7624, -7382 and other: Multiple vulns in Sophos Firewall, 6.8 - 9.8 rating 🔥. Vulns allow an attacker to perform SQLi, which could lead to remote code execution. Search at .👉 Link: #cybersecurity #vulnerability_map
0
3
5
CVE-2025-53770: RCE in Microsoft SharePoint, 9.8 rating 🔥. The most high-profile recent vulnerability allows an attacker to perform RCE on a Microsoft SharePoint server. Search at .👉 Link: #cybersecurity #vulnerability_map
0
2
13
Hannibal Stealer vs. Browser Security 🔓. In our latest article we discover how Hannibal Stealer cracks Cookie v20, slips past sandboxes, grabs Chromium and Firefox credentials — and how to defend against it. 👉 Read now:
netlas.io
How Hannibal Stealer bypasses modern browser protections to steal cookies and credentials, with deep insights into Chrome v20 encryption and evasion techniques.
0
3
5
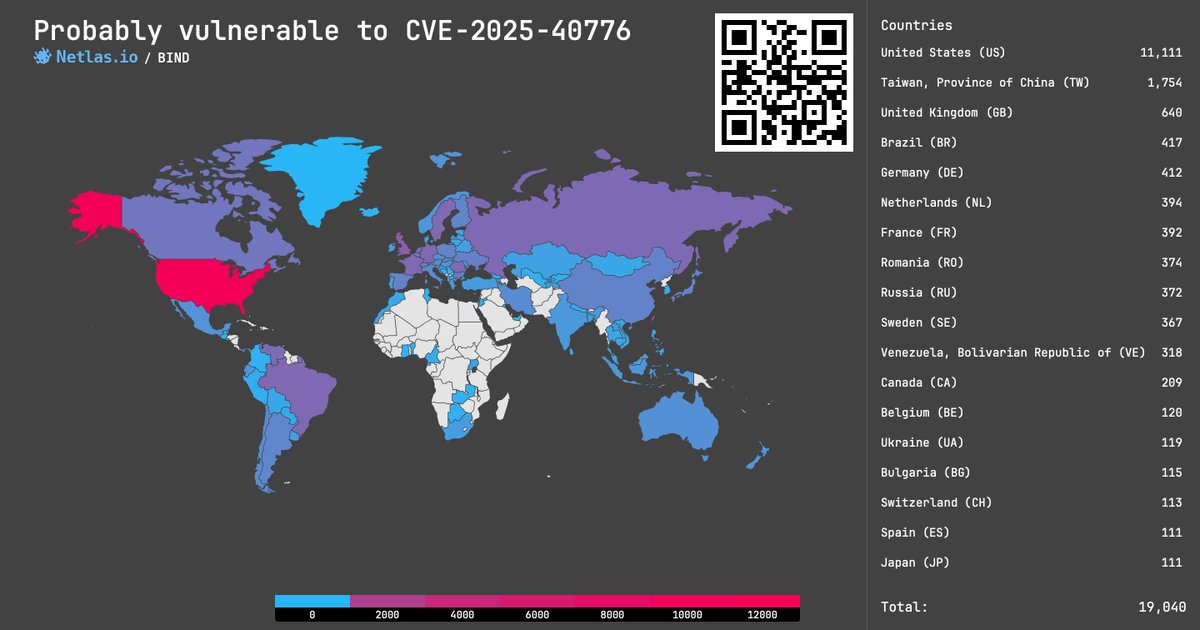
CVE-2025-40776, -40777: Cache Poisoning and DoS in BIND, 7.5 - 8.6 rating❗️. Birthday attacks and zero timeout vuln allow attackers to take down a server or poison its cache. Search at .👉 Link: #cybersecurity #vulnerability_map
0
4
11
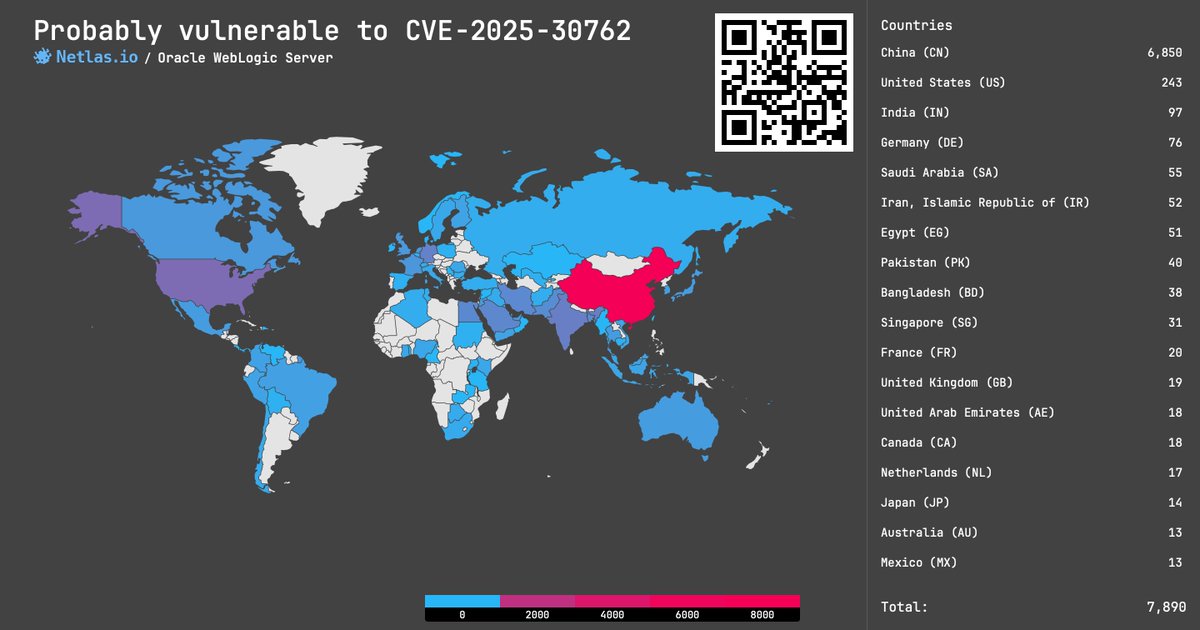
CVE-2025-30762: Missing Authentication in Oracle WebLogic Server, 7.5 rating❗️. Vuln in the Core component allows attackers to gain unauthorized access to critical data. Search at .👉 Link: #cybersecurity #vulnerability_map
0
2
10
CVE-2025-53506: Uncontrolled Resource Consumption in Apache Tomcat, 7.5 rating❗️. A vulnerability in some versions of Apache Tomcat could allow an attacker to cause a DoS. Search at .👉 Link: #cybersecurity #vulnerability_map
0
0
1
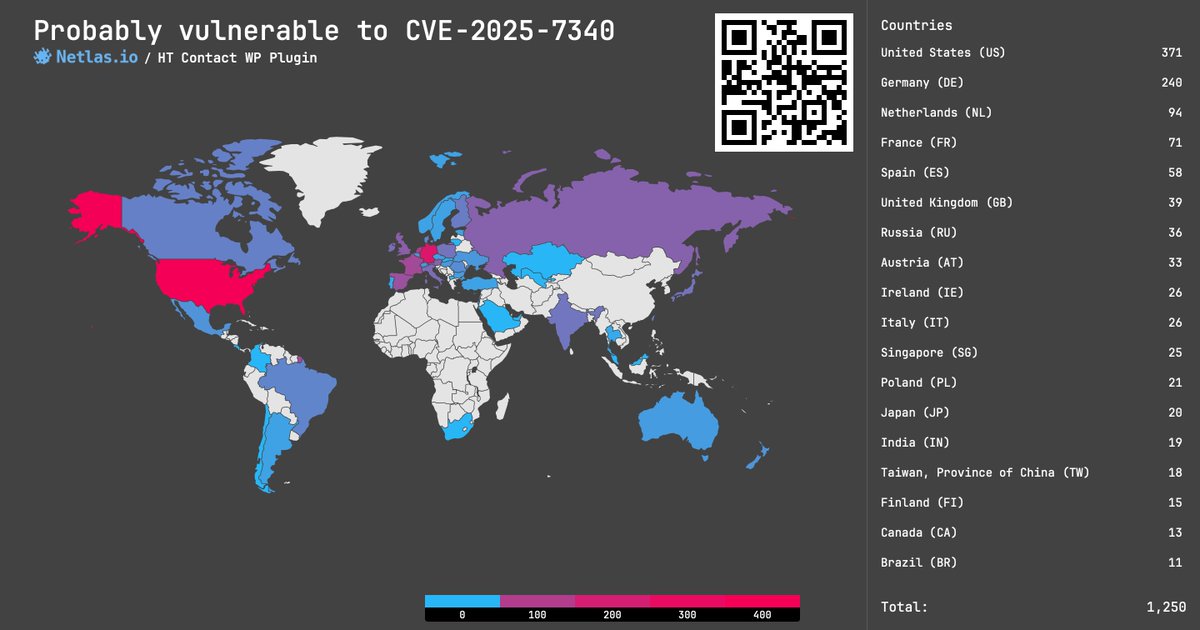
CVE-2025-7340, -7341, 7360: Multiple vulnerabilities in HT Contact WordPress plugin, 9.1 - 9.8 rating 🔥. Three vulns allow attackers to upload and execute arbitrary files. Search at .👉 Link: #cybersecurity #vulnerability_map
0
3
6
CVE-2025-30023: Deserialization of Untrusted Data in Axis Video Management, 9.0 rating 🔥. Vuln in the Axis client-server protocol allows an attacker to perform RCE. Search at .👉 Link: #cybersecurity #vulnerablity_map
0
6
13
CVE-2025-25257: SQL Injection in FortiWeb, 9.6 rating 🔥. A vulnerability in the FortiWeb firewall could allow attackers to inject code or commands and then execute them. Search at .👉 Link: #cybersecurity #vulnerability_map
0
3
7
CVE-2025-49535, -49551, and other: Multiple vulns in ColdFusion, 2.7 - 9.3 rating 🔥. 13 vulns, including XXE, Hard-coded Credentials, Incorrect Authorization, XSS and others. Search at .👉 Link: #cybersecurity #vulnerability_map
0
3
9
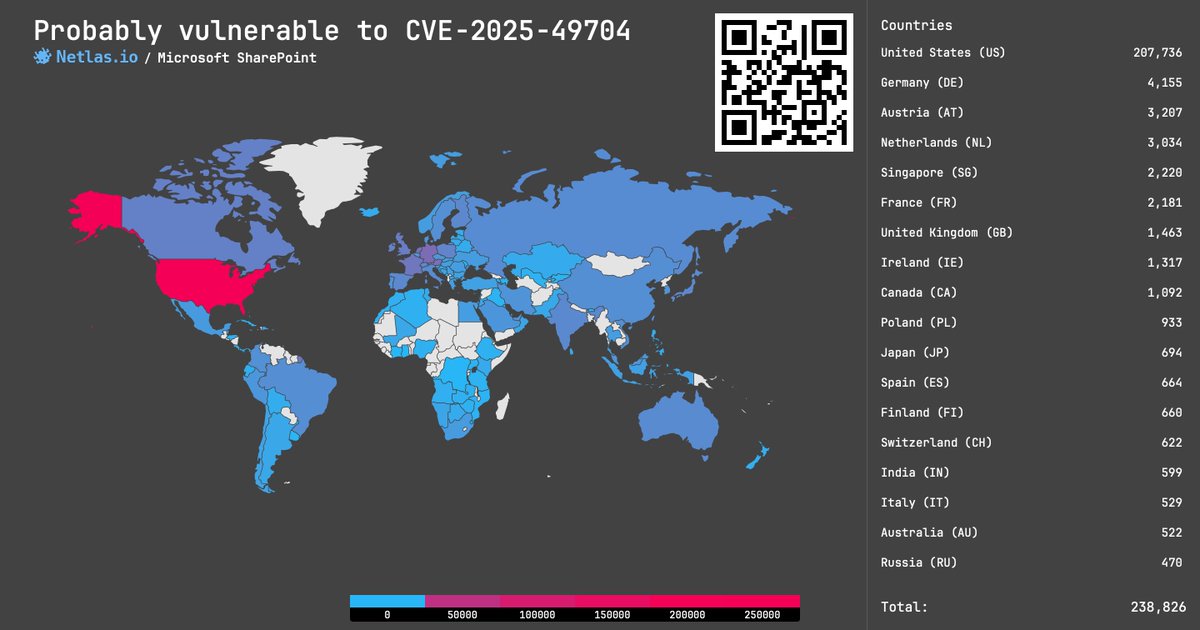
CVE-2025-49704: Code Injection in Microsoft SharePoint, 8.8 rating❗️. The vulnerability allows an authenticated attacker to execute code over the network. Search at .👉 Link: #cybersecurity #vulnerability_map
0
5
16
CVE-2025-42963: Deserialization of Untrusted Data in NetWeaver Application server, 9.1 rating 🔥. Vuln in the LogViewer allows an attacker to get full control over the system. Search at .👉 Link: #cybersecurity #vulnerability_map
0
1
0
CVE-2025-48367: DoS in Redis, 7.0 rating❗️. One of two recent vulnerabilities discovered in Redis. Allows an attacker to perform a DoS. Search at .👉 Link: #cybersecurity #vulnerability_map
0
2
8
CVE-2025-49826: DoS in Next.js, 7.5 rating❗️. A vulnerability in some versions of the Next.js framework allows attackers to perform cache poisoning, leading to a DoS. Search at .👉 Link: #cybersecurity #vulnerability_map
0
4
14
CVE-2025-47812: RCE in Wing FTP Server, 10.0 rating 🔥🔥🔥. NULL byte injection vulnerability allows attacker to take full control of Wing server. PoC is now available!. Search at .👉 Link: #cybersecurity #vulnerability_map
0
7
12