GreyNoise
@GreyNoiseIO
Followers
28K
Following
2K
Media
280
Statuses
2K
GreyNoise analyzes Internet background noise. Use GreyNoise to remove pointless security alerts, find compromised devices, or identify emerging threats.
Lots of different datacenters
Joined September 2017
GreyNoise has linked three concurrent campaigns targeting remote-access technologies — Palo Alto login attempts, Fortinet SSL VPN brute-forcing, and Cisco ASA scanning — all partially driven by the same threat actor(s) [High Confidence]. Full analysis 👇 https://t.co/gd89IAtk3u
greynoise.io
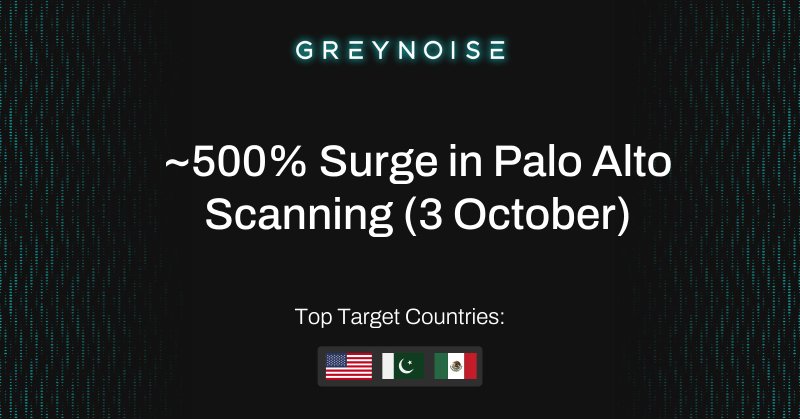
On October 3, 2025, GreyNoise observed a ~500% increase in IPs scanning Palo Alto Networks login portals, the highest level recorded in the past 90 days. The activity was highly targeted and involved...
1
6
27
Amid the security incident involving F5 BIG-IP announced today, GreyNoise is sharing recent insights into activity targeting BIG-IP to aid in defensive posturing. The anomalies reported in our blog may not necessarily relate to the 15 Oct incident. ⬇️ https://t.co/7lGQqC4PVc
greynoise.io
Amid the security incident involving F5 BIG-IP announced on 15 October 2025, GreyNoise is sharing recent insights into activity targeting BIG-IP to aid in defensive posturing.
1
7
25
Use GreyNoise Block to dynamically block all IPs associated with this botnet: https://t.co/OcPa1ZTZu8
#RDP #Botnet #Cybersecurity
0
0
1
Nothing bonds players faster than disliking the same umpire.
31
33
661
A global botnet has tripled in size in the past five days, so GreyNoise is sharing an executive situation report (SITREP) to streamline decision making. Full SITREP: https://t.co/2ug1VLp82V
1
2
6
Attacker infrastructure evolves in real time. Your defenses should too. Introducing GreyNoise Block, ensuring your blocklists update automatically. 🦾 https://t.co/kygl0XzwKl
greynoise.io
Discover why traditional blocklists fail and how GreyNoise Block offers real-time, configurable, low-noise IP blocking powered by primary-sourced intelligence.
0
10
38
A 100,000-IP botnet is actively targeting U.S. RDP infrastructure. 🔗Read the analysis: https://t.co/DzjMziUI1P
#ThreatIntel
#Cybersecurity #RDP #Botnet #GreyNoise
greynoise.io
Since October 8, 2025, GreyNoise has tracked a coordinated botnet operation involving over 100,000 unique IP addresses from more than 100 countries targeting Remote Desktop Protocol (RDP) services in...
3
12
19
The GreyNoise team will be at #CriblCon next week and we would love to see you there! If you are headed to Maryland for the event, check out our booth and talk to the team. 👻🤝🐐 🔗 https://t.co/OTLv16DBFU
0
2
4
GreyNoise Feeds are here: real-time webhook alerts for CVE status changes, exploitation spikes, and IP classification changes. No more polling. Respond the moment threats emerge. 🦾 https://t.co/Rknoe2Txd7
greynoise.io
Learn how GreyNoise Feeds enable real-time, event-driven threat intelligence that eliminates polling delays—helping defenders react instantly to new exploits, IP threats, and zero-day activity.
0
7
28
Palo login attempts are escalating, potentially driven by iteration through a large credential dataset. GreyNoise is sharing observed usernames/passwords for defender review. 🔗 Latest: https://t.co/gd89IAtk3u
#PaloAltoNetworks #ThreatIntel
1
18
58
NoiseLetter, but make it fashionably late... 💅 We were at our company offsite, but we're back with our new GreyNoise MCP Server launch, Cisco ASA zero-day and VPN brute force insights, plus upcoming events, let's get into it!
greynoise.io
Get GreyNoise updates! Read the September 2025 NoiseLetter for product news, key resources, the latest tags and vulnerabilities, and more.
0
4
12
GreyNoise observed a ~500% surge in IPs scanning Palo Alto Networks login portals on October 3, 2025 — the highest level we’ve seen in 90 days. Read our full analysis here 👉 https://t.co/gd89IAsMdW
#PaloAltoNetworks #PaloAlto #GreyNoise #ThreatIntel #PANOS
greynoise.io
On October 3, 2025, GreyNoise observed a ~500% increase in IPs scanning Palo Alto Networks login portals, the highest level recorded in the past 90 days. The activity was highly targeted and involved...
1
14
33
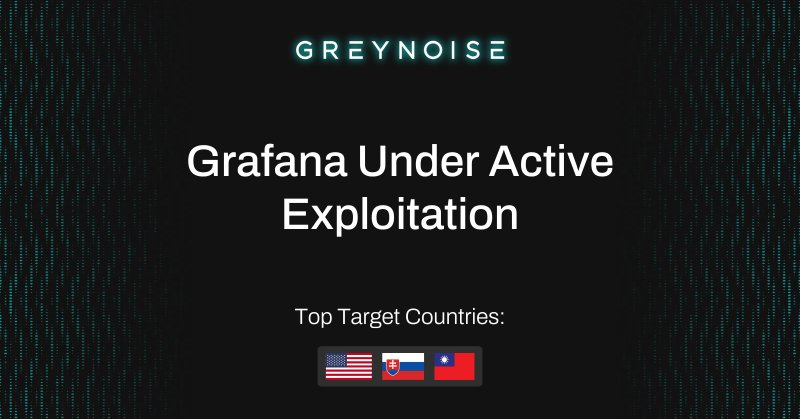
On 28 September, GreyNoise observed a sharp one-day surge in attempts to exploit Grafana CVE-2021-43798. Full analysis & malicious IPs ⬇️ https://t.co/kMvTCa7zkW
#Grafana #GreyNoise #ThreatIntel
greynoise.io
GreyNoise observed a sharp one-day surge of exploitation attempts targeting CVE-2021-43798 — a Grafana path traversal vulnerability that enables arbitrary file reads. All observed IPs are classified...
0
6
12
We got (most of) the team together last week and it was magical, so grateful for each + every one of these GreyNoids ✨
0
2
12
GreyNoise now has coverage for Cisco zero-days CVE-2025-20333 and CVE-2025-20362. Watch for exploit attempts in real-time: CVE-2025-20333 (Net new): https://t.co/V0CueAEKAp CVE-2025-20362 (Updated tag): https://t.co/o159T4UUES
#CiscoASA #Cisco #ZeroDay #CiscoZeroDays
0
23
61
O Canada, see you tomorrow! 🍁
🍻 At SecTor 2025? Unwind with runZero + @GreyNoiseIO at our happy hour! 📅 Wed, Oct 1 | 6–8pm 📍 The Pint Public House, Toronto 🍺 Free pints + light apps 👉 RSVP: https://t.co/du3O950GZV
0
1
3
GreyNoise: Reconnaissance surge on Cisco ASA preceded zero-days
0
7
17
🍁 runZero is at SecTor! 🎤 Rob King — spotting counterfeit devices (Wed 4:15pm, Rm 716B) 🎤 @hdmoore — rules of cybersecurity (Thu 9am, Hall F) 🍻 HH w/@GreyNoiseIO (Wed 6–8pm, The Pint) 👉RSVP: https://t.co/hvkWlPgWC5 ✅ Register: https://t.co/EUN5UycWB4
1
3
4
🚨GreyNoise has published a new Situation Report on Cisco ASA reconnaissance activity we observed before the new zero-days were disclosed. Read the full report: https://t.co/VbUlVBEWha
#Cisco #ASA #CiscoASA #GreyNoise #ThreatIntel #CVE202520333 #CVE202520362
3
25
70