Elliot
@ElliotKillick
Followers
3K
Following
79
Media
6
Statuses
66
Security engineer and researcher | Elliot on Security
Toronto, Canada
Joined February 2021
Calling all experts in Windows internals and low-level systems architecture! 'The Root of DllMain Problems' (or 'DllMain Rules Rewritten') is now in preparation for its final publication! Feedback and sign-offs from the community are greatly appreciated.
github.com
Operating System Design Review: A systemic analysis of modern systems architecture - ElliotKillick/operating-system-design-review
2
58
191
To all my infosec friends, if your blog doesn't yet have an email newsletter for your subscribers. well now you can have one set up in no time at virtually no cost - all open source. You're welcome.
github.com
Convert RSS/Atom feed to email newsletters. Contribute to ElliotKillick/rss2newsletter development by creating an account on GitHub.
0
6
17
Today, I'm releasing a new project that automates sending email newsletter notifications for new content on your blog: rss2newsletter! In 300 lines of code, it easily replaces any overpriced and bloated proprietary solution that charges you per-contact.
github.com
Convert RSS/Atom feed to email newsletters. Contribute to ElliotKillick/rss2newsletter development by creating an account on GitHub.
0
0
3
I just released a new tool for searching Microsoft Developer Blogs in bulk and fully local. Really helpful for finding information on that one Windows internals component.
github.com
Microsoft Developer Blogs Search Tool. Contribute to ElliotKillick/ms-devblogs-search development by creating an account on GitHub.
0
4
9
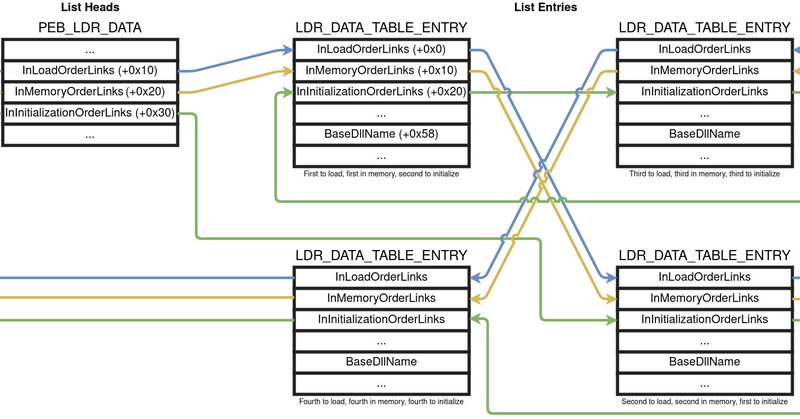
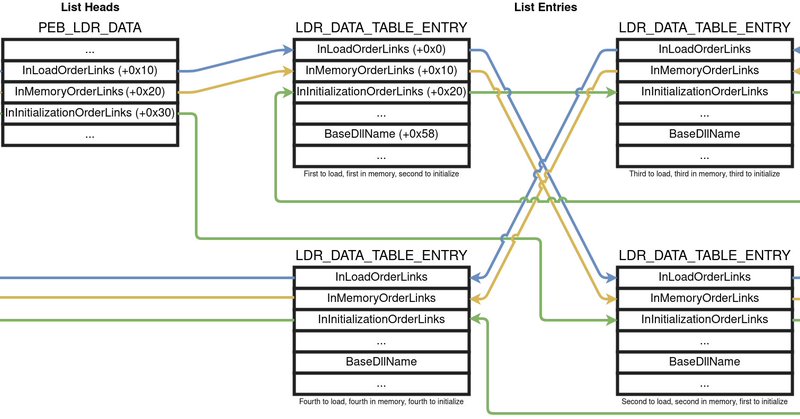
A comprehensive analysis of all the internal Windows 10 loader states? Done - Have a look at that and a high-level analysis of how a library load works under the parallel loader.
github.com
Operating System Design Review: A systemic analysis of modern systems architecture - ElliotKillick/operating-system-design-review
0
7
30
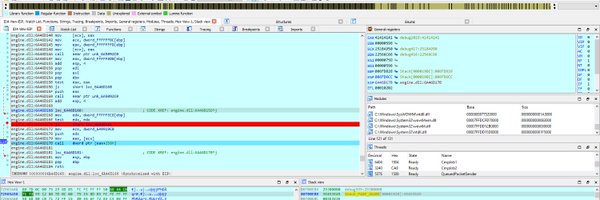
Reverse engineering the Windows 10 parallel loader is challenging but interesting work. I recently fully reversed the pivotal LdrpDrainWorkQueue function and I'm just now working on LdrpLoadDllInternal plus others.
github.com
Operating System Design Review: A systemic analysis of modern systems architecture - ElliotKillick/operating-system-design-review
0
14
52
DllMain Rules Rewritten are Microsoft's infamous DllMain Rules - rewritten. After countless spent hours researching and reverse engineering the new and old Windows loaders, they are now complete.
github.com
Operating System Design Review: A systemic analysis of modern systems architecture - ElliotKillick/operating-system-design-review
0
45
110
I just spent the last few months of my life reverse engineering the Windows 10 parallel loader and figuring out how it does concurrency. Updates have now been published!.
github.com
Operating System Design Review: A systemic analysis of modern systems architecture - ElliotKillick/operating-system-design-review
3
47
163
Thrilled to unveil the "Windows vs Linux Loader Architecture" project! The FIRST side-by-side comparison ever done unraveling the similarities and differences of this core component between operating systems. Check out the new repo!.
github.com
Operating System Design Review: A systemic analysis of modern systems architecture - ElliotKillick/operating-system-design-review
2
37
96
What is Loader Lock? 🤔 Going BEYOND undocumented, we delve into the heart of the modern Windows loader investigating some internals for the first time and demystifying Loader Lock. 🔒 Check out the research article.
elliotonsecurity.com
A modern investigation of the Windows loader architecture and loader lock
2
26
54
The full and open source code used in "Perfect DLL Hijacking" has now been released on GitHub: LdrLockLiberator.
github.com
For when DLLMain is the only way. Contribute to ElliotKillick/LdrLockLiberator development by creating an account on GitHub.
4
130
338
Perfect DLL Hijacking: It's now possible with the latest in security research. Building on previous insights from @NetSPI, we reverse engineer the Windows library loader to disable the infamous Loader Lock and achieve ShellExecute straight from DllMain. 🔍 Link in bio 🔗
14
295
813
Creating Windows hacking labs has gotten a lot easier with this new tool I've developed: It's a reverse engineering of Microsoft's hidden downloading API - fully automated to always grab the most up-to-date Windows ISO so you never have to do it again! 🚀
github.com
The Secure Microsoft Windows Downloader . Contribute to ElliotKillick/Mido development by creating an account on GitHub.
3
75
244
🚀 Want to level up your Windows reverse engineering skills fast? Check out this newly published #lolbin RE methodology post! Uncover undiscovered lolbins in Windows right now! Link in bio 🔗
3
74
370
Hey I'm back but now with a new #informationsecurity blog (, never before seen zero day exploits, and lots of new offensive security techniques & tools for you (also more new lolbins)! Expect all this and more in what's to come next.
0
2
10
RT @Oddvarmoe: Update to LOLBAS today. Merged a lot of PRs. Thanks! New:.Aspnet_Compiler.exe,Certoc.exe,Cmdl32.exe….
0
111
0
I found out "C:\Windows\System32\WorkFolders.exe" (signed by MS) can be used to run arbitrary executables in the current working directory with the name control.exe. It's like a new rundll32.exe #lolbin but for EXEs!
9
637
2K