Ashish Kunwar
@D0rkerDevil
Followers
13K
Following
102K
Media
597
Statuses
23K
ex @Microsoft Security Researcher| Vulnerability Research | Threat Intel | EASM | DE | Penetration Tester | Opinions here are solely mine not my employer
somewhere in your network
Joined February 2017
RT @hackprove_: 💣 Google Drive Auth Bypass: How View-Only Folder Sharing Leaked Google Form Responses ($5000 Bug).more information: https:….
infosecwriteups.com
Author: Aditya Sunny | Category: Bug Bounty | Google VRP | Auth Bypass
0
8
0
RT @assetnote: Our Security Research team at @SLCyberSec found four vulnerabilities in the quality management platform ETQ Reliance, includ….
slcyber.io
Note: In correspondence with Hexagon while disclosing the bugs below, they informed us that any sharing of source code would be considered a violation of their terms and license. The Java code has...
0
16
0
RT @geeknik: China's "NightEagle" reveal is performative victimhood—mirroring their own espionage empire while slapping an eagle label to t….
news.risky.biz
In other news: SEC and SolarWinds seek settlement; C&M hack linked to malicious insider; Luis Vuitton discloses breach.
0
1
0
RT @garethheyes: Manual testing doesn't have to be repetitive. Meet Repeater Strike - an AI-powered Burp Suite extension that turns your Re….
0
9
0
RT @kaganisildak: bitchat-python.written in python & compatible with ios/android. out now. @jack ➟ original / ios.@callebtc ➟ android.@sh….
0
171
0
RT @androidmalware2: Shizuku unlocks advanced functionality on any Android. Using #Shizuku your Android gains ADB privileges to remove bloa….
0
137
0
RT @zoomeye_team: CVE-2025-25257: FortiWeb Pre-Auth RCE.🔥PoC: ZoomEye Dork👉app="FortiWeb WAF".ZoomEye Link: https:….
0
28
0
RT @_xploiterr: Website allows to add your own link, I have visited that page many times tried different variations but not able to exploit….
aszx87410.github.io
In the previous post, various XSS scenarios and ways to execute code were mentioned, including something called the javascript: pseudo protocol. Even from a modern frontend perspective, this is...
0
26
0
RT @pdiscoveryio: Missing the latest CVEs puts you behind. Manually tracking new vulnerabilities takes time and effort. Say Hello to the….
0
5
0
RT @ganaseclabs: FYI : A pentest is NOT the same as a vulnerability scan. One finds known issues. The other thinks like an attacker. A pen….
0
2
0
RT @exploitsclub: Another Week, Another EXPLOITS CLUB 📰. ---.🎉 Binja giveaway: sign up to support the newsletter 🎉.---. Tesla wall charger….
blog.exploits.club
Pacers in 7. Annnnyways 👇 Don't Forget! We are doing a Binary Ninja personal License Giveaway! All you have to do is: 1. Subscribe to the newsletter. C'mon - that should be easy enough. Winner will...
0
12
0
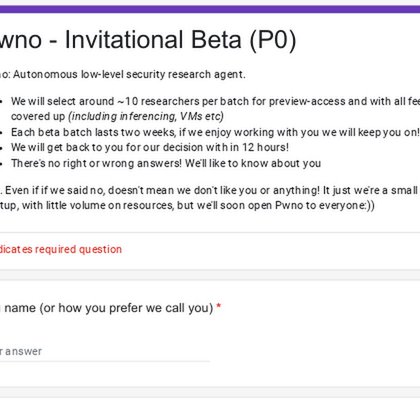
RT @retr0reg: Signup for the invitational beta of @pwnoio.(we cover all the fees, you provide feedbacks):.
docs.google.com
Pwno: Autonomous low-level security research agent. We will select around ~10 researchers per batch for preview-access and with all fees covered up (including inferencing, VMs etc) Each beta batch...
0
2
0
RT @retr0reg: working with binaryninja on an single ASAN output, of a sophisticated framework. .
0
36
0
RT @retr0reg: My handwritten notes on how Attention in Transformers works, based on @3blue1brown's wonderful DL5, DL6!. .
0
5
0
RT @olivier_boschko: New blog just dropped 🤠 I've spent hours boiling down why adversarial examples fundamentally exist, distilled down to….
boschko.ca
Explore why adversarial examples fundamentally exist & why models are often wrong almost everywhere.
0
30
0
RT @Elektor: The I2C bus is highly vulnerable due to its design — both SCL and SDA “float” at high potential and are pulled low by the indi….
0
15
0
RT @pashovkrum: Too many hacks in web3 have come not from vulnerable smart contracts, but from bad OpSec of humans. Anybody who wants to….
updraft.cyfrin.io
Learn advanced web3 wallet transaction verification techniques, signature validation, real-world exploit case studies, how to implement advanced protection strategies.
0
19
0
RT @UnslothAI: Finetune DeepSeek-R1-0528-Qwen3 with GRPO using our free notebook!. Our new reward function increases multilingual (or custo….
colab.research.google.com
Run, share, and edit Python notebooks
0
171
0