Alexandre Becholey
@0xabe_io
Followers
439
Following
2K
Media
10
Statuses
1K
RT @OutflankNL: Black Hat Bonus: Learn more about @kyleavery_ 's research on training self-hosted LLMs to generate evasive malware and crea….
0
46
0
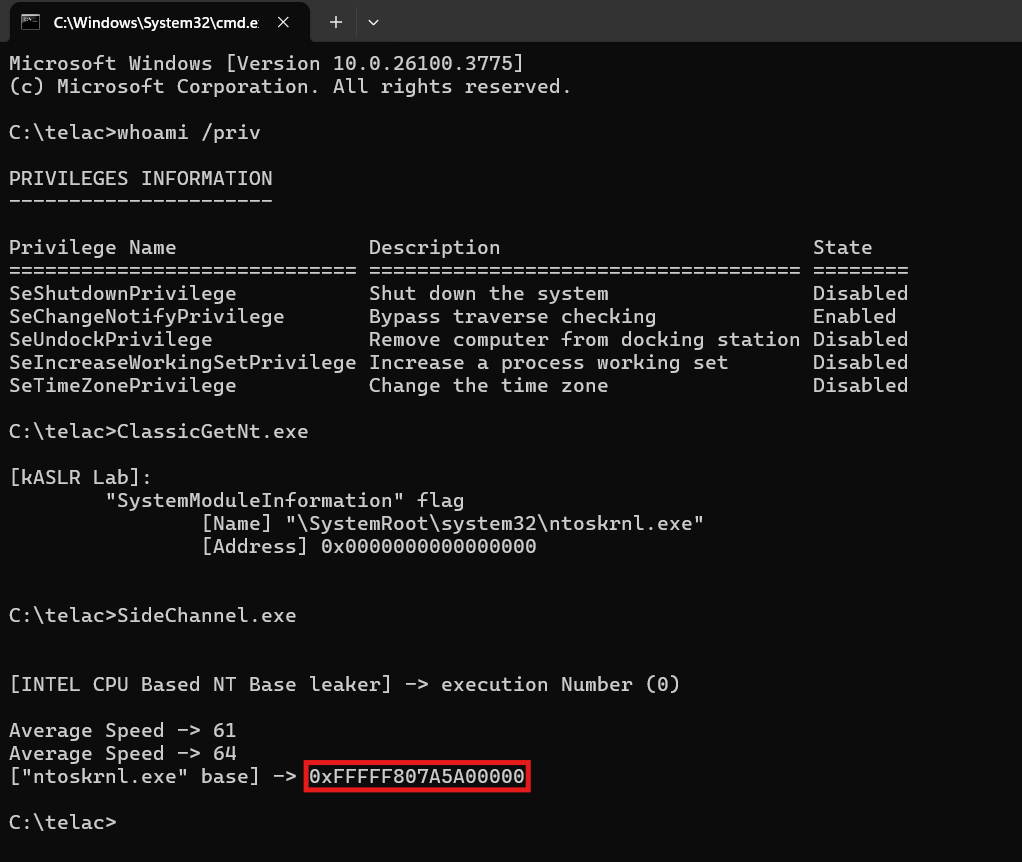
RT @R00tkitSMM: 𝗖𝗩𝗘-𝟮𝟬𝟮𝟱-𝟮𝟳𝟬𝟲𝟮 is one of my favorite Linux kernel vulnerabilities that we have discovered/exploited together with my brilli….
0
17
0
RT @5aelo: We released our Fuzzilli-based V8 Sandbox fuzzer: It explores the heap to find interesting objects and c….
github.com
This is a basic fuzzer for the V8 Sandbox. It uses the memory corruption API to implement a random-but-deterministic (given a seed) traversal through the V8 heap object graph and corrupts some obje...
0
72
0
RT @mathias_fuchs: Attackers love RDP for sneaky lateral moves—but every pixel leaves a clue! 🕵️♂️ Check out my latest blog on tracking at….
medium.com
Introduction
0
87
0
RT @r0keb: Good morning! Just published a blog post diving into Windows Kernel Pool internals: basics, memory allocation functions, interna….
r0keb.github.io
Good morning! In today’s blog post we’re going to dive into a topic that has interested me for quite some time, the Windows kernel pool. It’s a topic that tends to have “scarce” documentation online...
0
135
0
RT @hexacon_fr: We've already received many high-quality submissions to our CFP, thank you! 🚀. Don't miss your chance to submit before July….
hexacon.fr
CFP is open for business!
0
11
0
RT @pedrib1337: We are looking for a junior security researcher 🤠 .No university degree or previous work experience required, but MUST be….
0
92
0
There is a lot of new content and we are pretty sure you will enjoy it. You can have a sneak peak on the V8 type confusion module I added to section 2 on the Off by One Security stream:
We *JUST* finished the SANS SEC760: Advanced Exploit Development course updates. Myself, along with @0xabe_io! We are recording this version in a couple of weeks and it will start running in late July. I'll tweet when we get the new syllabus updated. Bedtime. .
0
1
8
RT @BackEngineerLab: Given the recent events with VMPSoft DMCA'ing educational YouTube videos demonstrating how to unpack malware protected….
0
135
0
RT @dillon_franke: Thrilled to announce my new Project Zero blog post is LIVE! 🎉 I detail my knowledge-driven fuzzing process to find sandb….
0
105
0
RT @silviocesare: We’re hiring Vulnerability Researchers at @infosectcbr that specialise in Linux, OS kernels, Android, and embedded/IoT. W….
0
41
0
RT @call_eax: Just watched the Introduction to JavaScript and V8 for Browser Exploitation with @Steph3nSims and @0xabe_io . Honestly thi….
0
3
0
RT @zodiacon: In case you missed it, check out my Youtube channel with videos mostly related to Windows Internals:.
youtube.com
Pavel Yosifovich's YouTube channel offers concise videos primarily focused on Windows Internals and software development. With over 3,000 subscribers and 51 videos, the channel serves as a valuable...
0
57
0