0x2A Security
@0x2asec
Followers
45
Following
934
Media
1
Statuses
692
Security: the answer to the ultimate question of life, the universe, and everything.
Joined July 2025
New episode is out! - https://t.co/7oBG6nyeTk In this episode we’re joined by Sasi Levi from Noma Security to talk about AI and Agentic Security. We also talk about ForcedLeak, a Google Vertex bug, and debate if Prompt Injection is really a vuln.
0
4
32
An RbTree Family Drama Talk by William Liu and Savino Dicanosa @cor_ctf about exploiting CVE-2025-38001 — a use-after-free in the network packet scheduler. Slides: https://t.co/9uzwjmQilt Video:
2
20
65
now that the reac2shell forced CTFers to look into flight protocol and RSC, there is a high chance of few more bugs coming out of it with similar impact. its a pretty complex protocol for developers to implement, and complexity is a perfect breeding ground for weird state
3
5
140
‼️🇰🇵 Meet North Korean recruiter 'Aaron,' who infiltrates Western companies by using AI and posing as a remote IT worker using stolen or rented identities. He was lured into a sandbox by researchers, who observed the wild APT in a controlled setting to see what he would do.
32
481
3K
"Within hours of the public disclosure of CVE-2025-55182 (React2Shell) on December 3, 2025, Amazon threat intelligence teams observed active exploitation attempts by multiple China state-nexus threat groups, including Earth Lamia and Jackpot Panda." https://t.co/hhkwi084XA
aws.amazon.com
Within hours of the public disclosure of CVE-2025-55182 (React2Shell) on December 3, 2025, Amazon threat intelligence teams observed active exploitation attempts by multiple China state-nexus threat...
1
1
7
Problem I see is people are confusing code reasoning with hacker intuition. To understand where LLMs fit in AppSec vuln research, firstly we need to categorize the cognitive load of vulnerabilities: 1. Pattern Matching Tracing user input for XSS, IDORs, Injections etc. If your
When the POC comes out, it’ll be a humbling moment for LLMs and how we use them. What’s circulating is extremely naive and incorrect. Experienced engineers are sharing plausible-sounding hallucinations from frontier models. Reminder to bump React, Next & frameworks.
3
17
113
2025 showed clearly — the myth of a “safe Mac” is dead. According to Moonlock’s annual threat report: • macOS backdoor variants 📈 up by 67% • Stealer malware families 📈 up by 17% • Over 80 countries hit by major stealer campaigns In short: Macs are no longer “safe by
1
8
12
One of the most consistent trends I’ve observed in cyber security in my career - is the inability for companies/vendors to objectively differentiate themselves from their competition (outside of cost). I’ve seen this across multiple domains including: Red teaming Incident
3
3
25
In regards to "cyber influencers", here is a list of people I think are actually great. However, I am extremely biased toward malware related content and/or low-level programming stuff. Unfortunately, some of the really technical people I like also do not post too often. They
65
149
1K
🎁 GenAI x Sec Advent 1 - Visual Threat Intelligence If you follow my work you know I am a big fan of visualization to explain complex or technical content. I used to spend days building the perfect infographic, but now I can generate one in a single shot thanks to LLM
4
23
111
On November 25, 2025, an engineer’s machine was affected by the Shai-Hulud npm supply chain malware. The malware accessed GitHub credentials and made unauthorized changes to some of our repositories. Once we detected the activity, we immediately revoked exposed credentials,
trigger.dev
On November 25th, one of our engineers was compromised by the Shai-Hulud npm supply chain worm. Here's what happened, how we responded, and what we've changed.
7
7
53
From one "unnamed" RAT: Malware dev task: "Be innovative and make sure the file is deleted." Malware dev: "Got it, boss. Let’s delete it 10× just to be sure!" 🤡🗑️💥
1
6
59
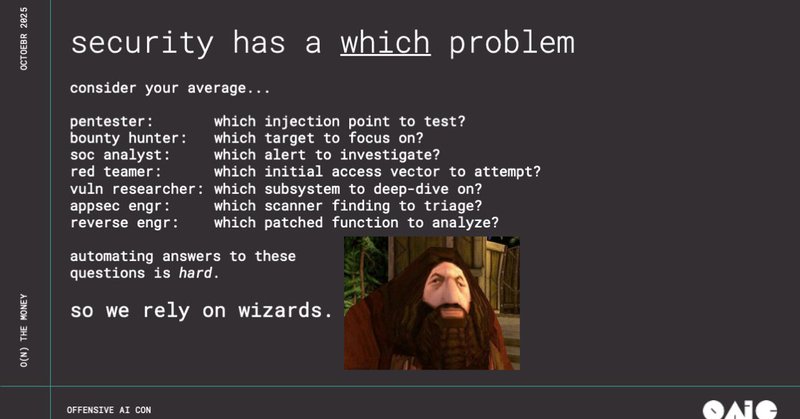
''O(N) the Money: Scaling Vulnerability Research with LLMs'' #infosec #pentest #redteam #blueteam
https://t.co/WiJ8a9l1wP
noperator.dev
Let’s go back to the basics and consider a very simple goal: What if we could find and fix all the vulnerabilities in open source software? This is a pretty ambitious goal, admittedly, but…
0
25
117
This. Alert & CVE fatigue are real. Perpetually growing backlogs of bugs means no one gives a shit anymore. We need clear writeups that consider exploitability, and include a patch. If you can automate finding bugs, you can automate submitting fixes.
@FFmpeg @usgraphics Denial of Attention is a real security threat in the AI era and I am surprised we don't hear about this more
13
28
336
Google recently announced their new AI Vulnerability Research Program: Rewards are medium in comparison to Chrome VRP, but overall solid, considering an easier entry and non-binary focus. This is a good security bounty option for beginners. https://t.co/1HF3h68FqL
2
27
160
This blogpost is interesting - has Windows internals, my own novel solution to a problem red teamers have had for a while, EDR bypasses, debugging and much more. Spoofing command lines on Windows and solving the problem of length limitations: https://t.co/4R5FCfNvsV
2
47
163
If you want to learn more about malware the easiest method is learning malware TTPs (Threats Tactics and Procedures). Basically, understand some of the techniques employed by malware authors to do stuff Some malware techniques are simple and old Some malware techniques are
22
100
1K
People act like threat actors have a corporate strategy retreat every Q4. The imaginary meeting: "Okay team, Ransomware had a great run in 2025, but let's pivot to something totally new and untested for 2026 just for the vibe. The reality: "Does it still work? Yes? Okay, keep
6
8
34
Silver lining of the npm worm situation - the chaos probably caused SLSH to lose access to victim cloud infra due to companies rolling credentials.
1
3
10