xanhacks
@xanhacks
Followers
1K
Following
14K
Media
30
Statuses
4K
infosec @HeroCTF @flag4jobs
🇫🇷
Joined August 2016
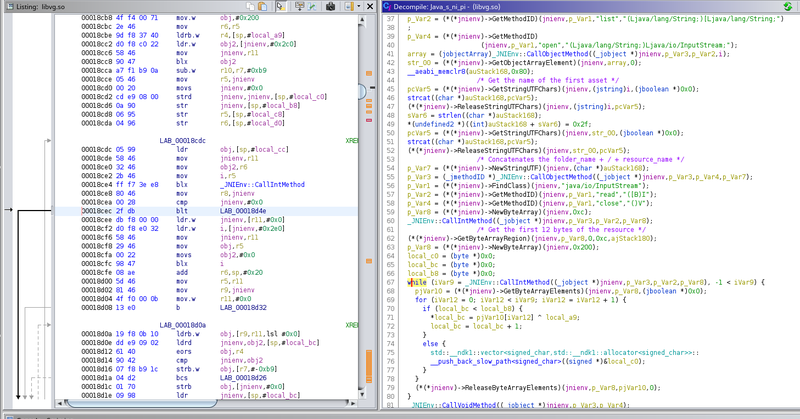
#MoqHao is a malicious Android application that has been spreading in France 🇫🇷 for 1-2 months via SMS phishing. Here is a technical analysis of the malware with Python scripts to unpack encrypted/compressed resource and extract C2 IP address and port. https://t.co/EJr2yzU3N9
xanhacks.xyz
Technical analysis of the MoqHao (a.k.a RoamingMantis) Android malware and phishing campaign
8
76
170
🎉 HeroCTF v7 is over — GG! 4,200 players • 0 ms downtime 🚀 Thanks to our sponsors (@dfsec_com , @Synacktiv , @DGA, @epieos , @AKAILABS_FR) and to all challenge creators 🙌 Write-ups are available here : https://t.co/REtRMhsUDV See you next time!
github.com
Challenges of the HeroCTF v7 edition. . Contribute to HeroCTF/HeroCTF_v7 development by creating an account on GitHub.
2
8
22
It’s official: HeroCTF 2025 is coming. From 28/11 – 9pm (UTC+2) to 30/11 – 11pm (UTC+2). No excuses, 48+ hours to hack 💪 #HeroCTF #CTF #cybersecurity
2
7
20
🚀 Kicking off our #HeroCTF v7 sponsor reveal! Over the coming weeks, we’ll highlight the partners who make this event possible. 🔥 Follow this thread 👇 Registration : https://t.co/hSjy0HMLhm
#CTF #cybersecurity #infosec
0
5
10
🔥🔥🔥🔥🔥🔥🔥🔥🔥
It’s official: HeroCTF 2025 is coming. From 28/11 – 9pm (UTC+2) to 30/11 – 11pm (UTC+2). No excuses, 48+ hours to hack 💪 #HeroCTF #CTF #cybersecurity
0
0
0
For the @ASIS_CTF, I created a challenge based on an interesting (novel?) DOM Clobbering technique! 🚩 In short, in non-strict mode, HTMLCollection items are not writable. This blocks property assignment, allowing unexpected values to be created 😄 👉 https://t.co/XiZX43MKY3
1
29
132
I made a new challenge where you need to steal the admin password by: 🪲Chaining multiple design flaws in a Java RMI app 🔒Exploiting a crypto misconfiguration
0
0
9
🔥HeroCTF v7 is back at the end of November! 🚩You can now register your team on CTFtime 🔗 https://t.co/tDGiA6Y0fV More information to come soon.
1
12
26
The part about the 0day I used on the TrackDb web challenge for the FCSC2025 has just been disclosed in the writeup, you can read it here: https://t.co/NWkMxRM7NO Please note that this vulnerability is not patched (see the end of the writeup for explanations).
During last week, I've played FCSC2025 and managed to reach first place in the web category ! I've written two writeups this year: one about pwning a Chrome extension, and another about a PostgREST service. https://t.co/lvLUODVvkA
https://t.co/NWkMxRLzYg Enjoy the read !
0
24
88
There we go, after 3 years of work, endless nights of dev and a truckload of coffee. We are finally releasing the biggest project we've done in our entire life. I hope you will like it !
https://t.co/eTUHUDIfRJ is live! Quickly uncover DNS records, subdomains, hosts, and their historical data directly via your browser. No noise, just the data you need for asset discovery and security research. Explore now:
9
9
68
Checker from @hackthebox_eu has some really complex exploitation steps. There's SQLI in Teampass, SSRF to file read in BookStack using a blind PHP filter oracle, and shared memory abuse. https://t.co/7IBQ496dCN
0xdf.gitlab.io
Checker starts with instances of BookStack and Teampass. Without creds to either, I’ll find an SQL injection vulnerability in Teampass and leak user hashes. One cracks, and let’s me in, revealing...
0
20
92
I've released my CTF bot template! :D It's not a big deal, but it comes with a heavily hardened Docker setup. The bot also sends a lot of debugging information over the TCP socket (console logs, navigation), which makes remote debugging much easier! 🔎 👉 https://t.co/PGoeSZuqkh
0
19
121
The #FCSC2025 ended yesterday, and my write-ups are now available here 👇 https://t.co/PsK90vMcup Btw, like every year, all the challenges have also been added to https://t.co/QmvWOmrKfG! 🚩 1/2
This year again, with @BitK_, we've made the Web challenges 🚩 The CTF is solo and lasts 10 days, if you have some time, please give it a look 😁 Btw, even if you're not doing Web challenges, there are 100+ challenges in various categories, you should find something you like!
2
20
90
🔥 Understanding Alcatraz ~ Obfuscator Analysis by @rhotav - Analysis of Alcatraz Passes with IDA - OEP Finder with @qiling_io - Scripting with IDAPython https://t.co/LK1fWopYDa
0xreverse.com
Introduction Binary-to-binary (bin2bin) obfuscators, which are frequently preferred by both malware developers and users seeking to protect their source code, are making the work of malware analysts...
0
46
109
I almost can't believe it, but I am finally releasing my Gitbook about CTF and Hacking, which is a year in the making. It contains many tricks, explanations, and resources from my experience and research. I hope it becomes a valuable resource for everyone! https://t.co/ZWwi9SfOva
2
29
143
I'm releasing fontleak: a new CSS injection technique to quickly exfiltrate text nodes (and yes, that includes inline scripts). Works on Chrome/Firefox and Safari*. You can use it to escalate the impact of your HTML injection payloads and to solve CTF challenges.
3
49
265
Quelques semaines après la vaste campagne de manipulation autour de la rencontre Trump-Zelensky, nous revenons en détail sur nos découvertes et notre méthodologie d'enquête. À retrouver sur le blog Agoratlas :
agoratlas.com
Analyse d’une campagne de manipulation sur twitter/x pour la rencontre Trump/Zelensky. Spam et bots, cartographie de l'influence
THREAD - Dans les dernières 24 heures, près de 35 000 comptes francophones ont parlé de la rencontre Trump/Zelensky sur X. Nos analyses ont permis de mettre en évidence de nombreux comportements coordonnés visant à manipuler l'opinion publique en faveur de la Russie ⤵️
0
4
19
Docs : une alternative Open Source à Notion ou Outline. (P) Ce projet est le fruit d'une collaboration entre les gouvernements français (la DINUM) et allemand (ZenDiS). 👉 Le projet : https://t.co/3glDiORe7B 👉 En savoir plus : https://t.co/8flNQovAvg
4
54
183
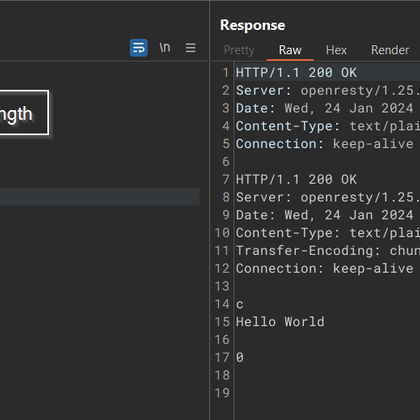
🚨HTTP Request Smuggling in lua-nginx-module!🚨 This affects major proxies like Kong GW, OpenResty, Apache APISIX and many more👀 Check it out: https://t.co/G9juMax7zk Big thanks to @albinowax for his awesome research and for answering all my questions! #bugbounty #bugbountytips
benasin.space
Discovery & MotivationI first came across this HTTP Request Smuggling vulnerability while conducting an internal pentest for a client at work. Realizing its potential impact, I decided to dig deep
8
70
267