Vidoc Security Lab
@vidocsecurity
Followers
2,039
Following
25
Media
90
Statuses
258
Building an AI Security Engineer to keep up with emerging threat of AI generated code. 🔧
San Francisco Bay Area
Joined December 2021
Don't wanna be here?
Send us removal request.
Explore trending content on Musk Viewer
DAVI NO DOMINGAO
• 331657 Tweets
Corinthians
• 146632 Tweets
Knicks
• 101555 Tweets
Wesley
• 94809 Tweets
Lite
• 90188 Tweets
Brunson
• 85957 Tweets
Kyrie
• 85242 Tweets
Díaz
• 73776 Tweets
Luka
• 62242 Tweets
Harden
• 61392 Tweets
Clippers
• 58924 Tweets
LOBOS COM AMSTEL
• 50833 Tweets
De Santis
• 49995 Tweets
Bucks
• 49928 Tweets
Sixers
• 49777 Tweets
昭和の日
• 42790 Tweets
Mavs
• 41445 Tweets
#ラヴィット
• 29964 Tweets
Felipe Melo
• 29031 Tweets
Pacers
• 27177 Tweets
Paul George
• 26757 Tweets
Diniz
• 23227 Tweets
Maurício
• 18209 Tweets
ATAQUE FURIOSO
• 14187 Tweets
#Canucks
• 12577 Tweets
Giannis
• 11703 Tweets
Emelec
• 10191 Tweets
Last Seen Profiles
Pinned Tweet
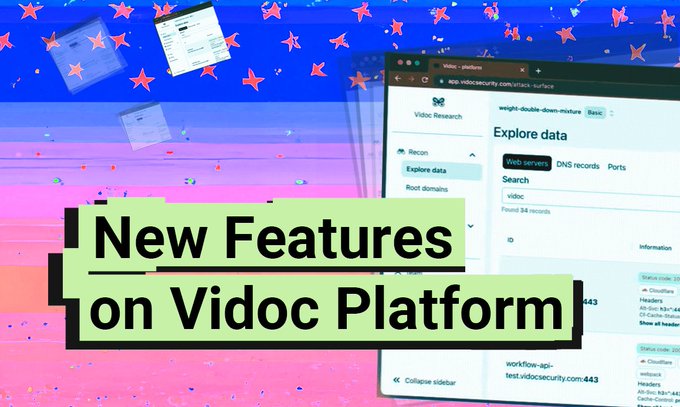
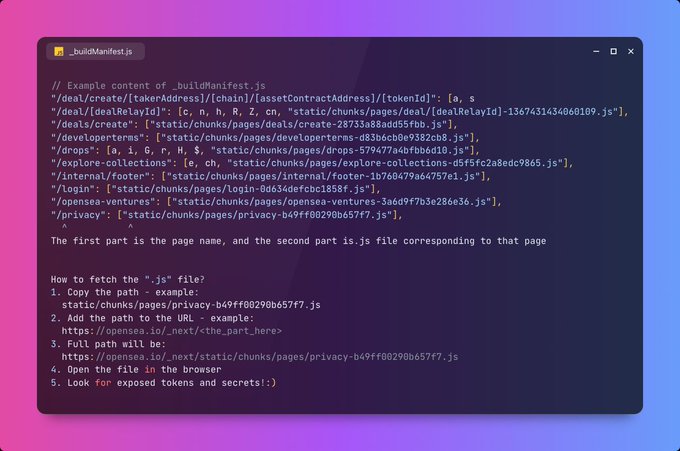
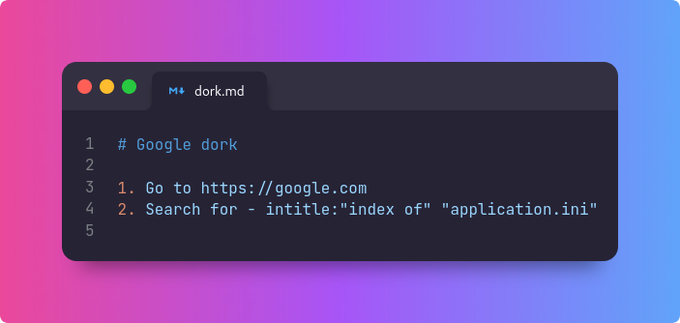
Update alert - check out what's new for you on the Vidoc platform. We released some cool new features that might be super useful for your bounty hunting or research!
#bugbountytips
1
3
13
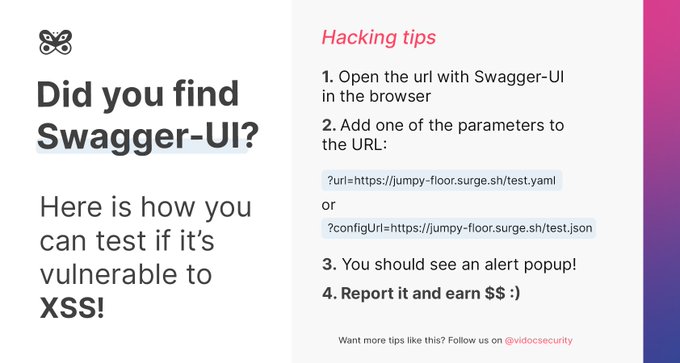
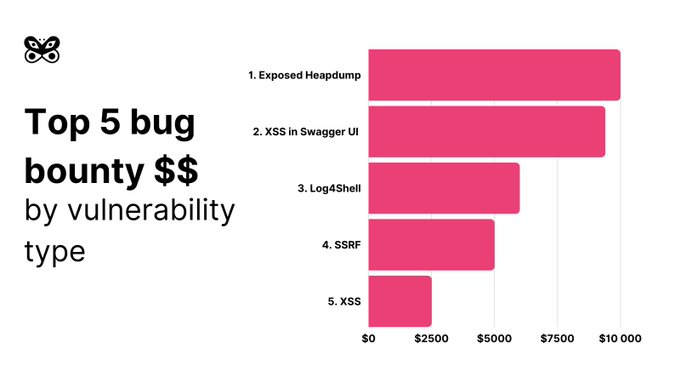
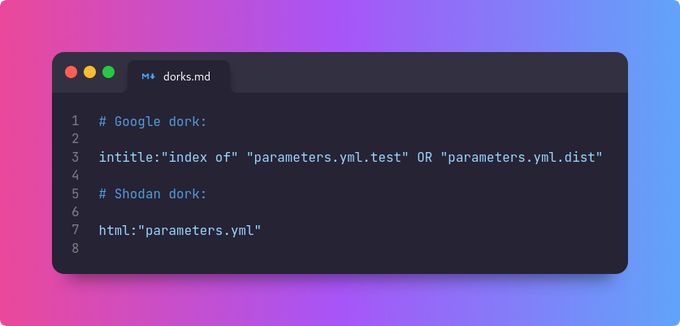
Vulnerability that made us 30 000$ richer (and we still submit reports) - XSS in Swagger-UI related to a bug in DOMPurify - many people waited for this writeup so here you are. Article by
@kannthu1
- happy hacking!
10
225
604
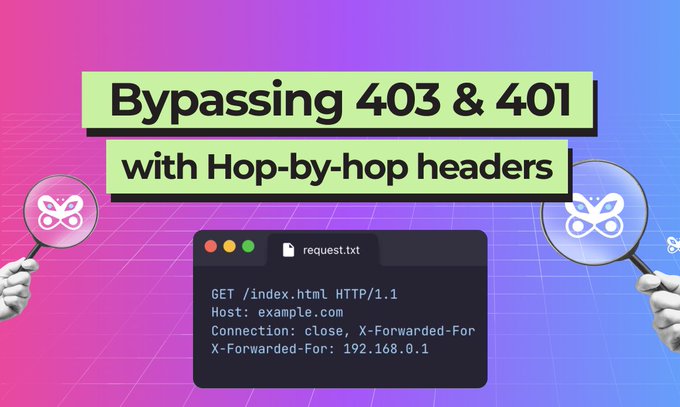
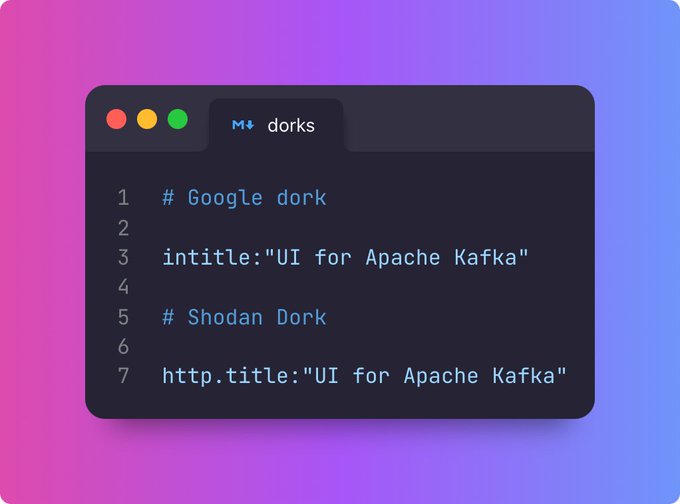
Know any 403 and 404 bypass hacks? We did research on common auth bypass techniques and created new templates in Vidoc Research. Article by
@KlaKlo_
, check it out:
4
83
259
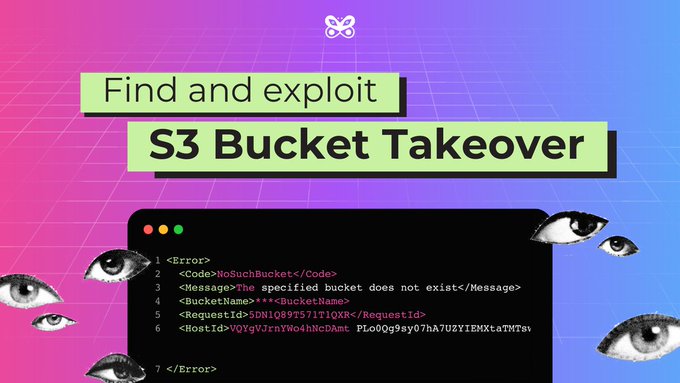
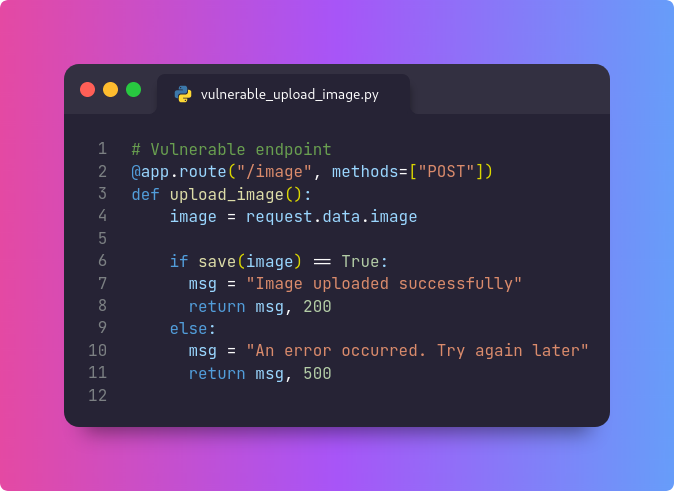
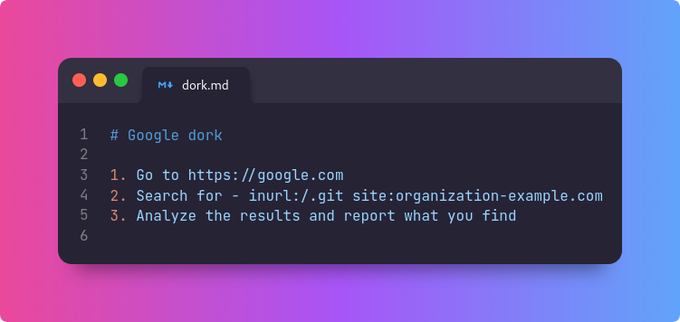
AWS S3 Bucket Takeover - How to Find and Maximize Impact by
@gregxsunday
In this article Greg will tell you how to:
- detect
- escalate
- show impact
AWS S3 Bucket Takeovers 😃
#BugBounty
#bugbountytip
#blog
#CyberSec
#Cybersecurity
2
68
169
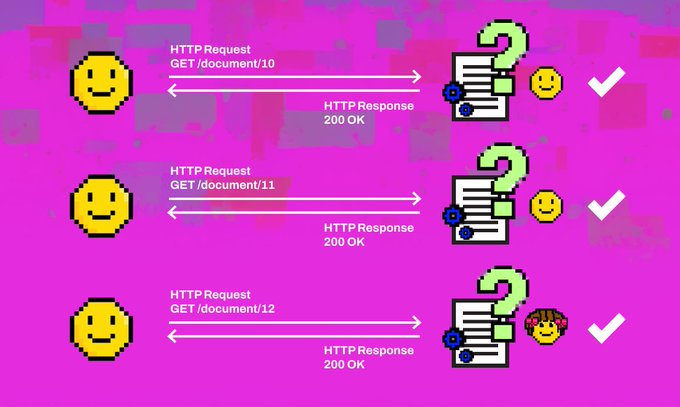
🧵 AWS S3 Bucket Takeover Vulnerabilities 🧵
In this thread, we will dive into what AWS S3 takeovers
are, how to maximize the impact and thus bounty for
them.
Don’t skip it because you might be missing out
on easy bounties.
1/11
#bugbounty
#bugbountytip
1
28
106
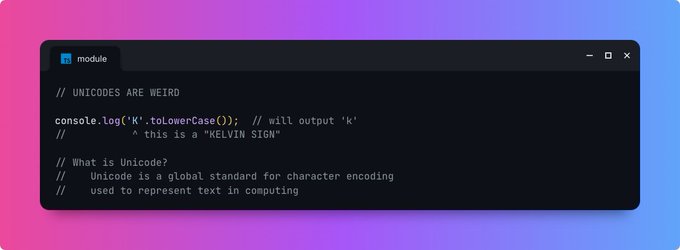
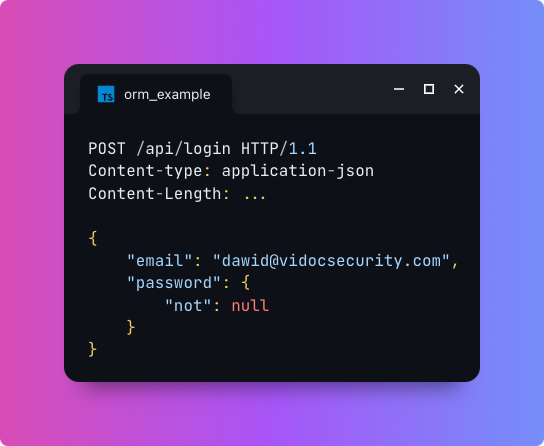
How Unicodes can be used to takeover accounts and bypass block lists 👇
1/6
#bugbountytips
#bugbountytip
#LearningWithVidoc
1
14
56
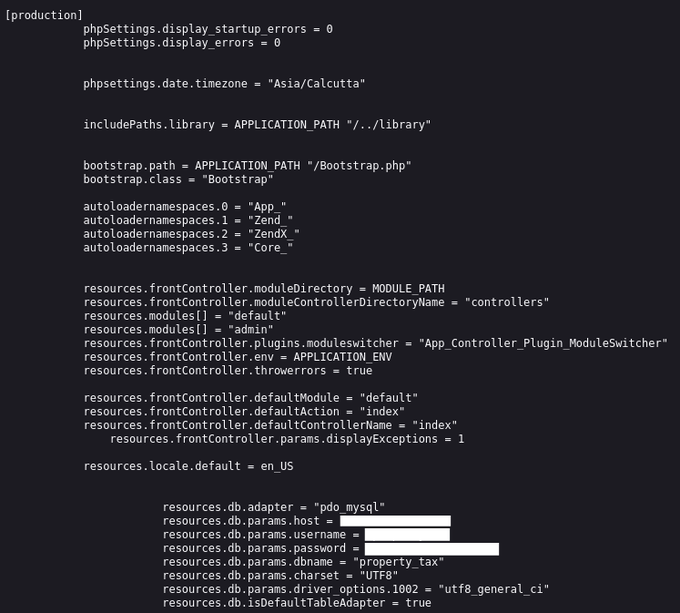
You found a Django app with debug mode enabled, now what?
Here are some learnings of how to escalate it to higher severity 👇 (from low/medium to high/critical)
#bugbountytips
#bugbountytip
#vidoc
1
11
50
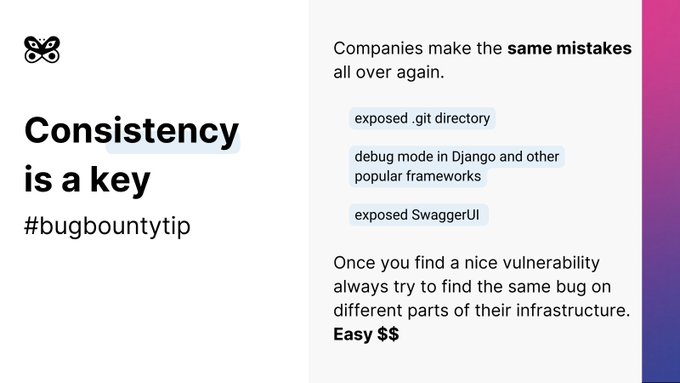
Last year we made $120k in bounties, most of it was easy and repeatable vulnerabilities. Once we detect it on one endpoint we usually scan whole infrastructure of the company for the same bug. Often we find it in several places
#bugbountytips
0
3
33
If you want to know why collab is important and how we made 120k in 2022 check out our first video, we share lots of
#bugbountytips
.
Many thanks for
@gregxsunday
,
@haqpl
and
@OlivettiOriana
- it wouldn't be possible without you, it was a great year!
1
5
30
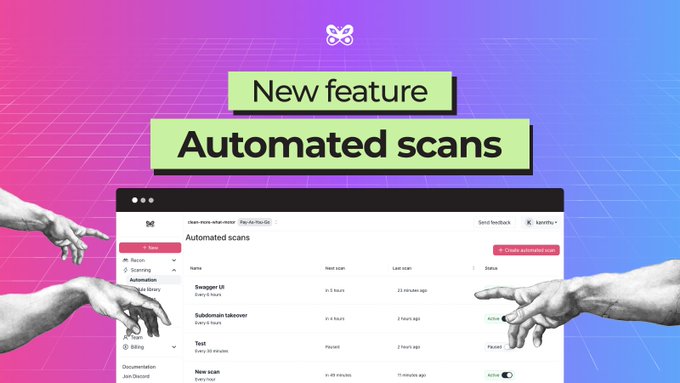
New feature alert 🚨
After we made a $120k bug bounty in the year we kept getting questions about how we did it.
So we are releasing Automated Scans - now you can now schedule modules to run every hour, day, week..
And automate your
#bugbounty
hunting like we did :)
2
4
17
We love hacking too, so to show our appreciation for all the hard-working bug bounty hunters, we're giving away 3 MONTHLY SUBSCRIPTIONS of Vidoc Research.
Share in comments who motivates you the most in security community and why, we will reward most inspiring answers
#bugbounty
6
3
16
@kannthu1
If you are interested in our newest research subscribe to our newsletter. Writeup on SSRF found in Facebook is coming soon.
0
5
15
API Best Security Practice for Developers
We know you are busy, so here you have a quick
#tip
to
better secure your API endpoints. 👇
1/3
1
3
15
API Best Security Practice for Developers
Here there is a quick
#tip
to better secure your API endpoints over night. 👇
1/3
1
0
10
#jobopportunity
👩💻👨💻
We are currently seeking a skilled Content Creator to
develop engaging articles for our blog and other
platforms. 🧐
If you have experience in this field and a passion for
creating compelling tech content, reach out to us!
Please send us an email at…
1
3
10
We had an incredible time at Poland's biggest cybersecurity event
@TheHackSummit
👾 Surrounded by amazing people and great talks. A truly unforgettable experience!
#HackSummit
#CyberSecurity
#Conference
0
0
9
@gregxsunday
We were always most annoyed with garbage recon data, but we solved this problem. You inspired us to write an article actually, thanks Greg and everybody for comments
0
0
9
API security
#tip
- don't share more information than is absolutely necessary!
(unless you want to be a good target for hackers, and not only ethical ones)
Why? Just keep reading 👇
1
2
8
#HappyHolidays
🎄🎄🎄
May your holidays be filled with well-deserved time
with loved ones, and may the New Year bring you the
joy of uncovering elusive vulnerabilities and the thrill of
solving complex security puzzles.
By the way, just a reminder, until the end of December…
0
1
7
Another interesting insight for you:
Do you want to know the most searched query in the recon tab?
Yes, we had thousands of those.
It looks like many hackers think alike 😀
Also, yes, it's that easy to do recon with
@vidocsecurity
Check it out if you are planning to do…
0
4
7
Cybersecurity October event in Barcelona went well! Thanks to everyone for attending. Stay tuned for more, because we are planning some events dedicated to tech security people as well. Special thanks to
@georgianabirdan
from
@egldwomen
for being amazing guests.
#ECSM2023
0
0
6
We were really surprise to see this one 😃
The most frequently targeted domains for
reconnaissance using Vidoc in 2023 was Dell, Google
and Fisglobal in the top 3!
Did you do security research on them? 🧐
Are you surprised by this summary? 😲
Let us know ✨
#Vidoc2023
…
2
2
6
Protect your data with VIDOC during Data Privacy Week!
Explore VIDOC:
✔️ Automation platform for your security team
✔️ 30% off for your business during Data Privacy Week
✔️ Book a demo and elevate your web application security
#DataPrivacyWeek
#Cybersecurity
#VIDOC
#BookDemo
1
3
6
Wow, you guys are awesome!
6,000,000,000 HTTP scanner requests were sent on Vidoc in 2023!
We're super happy to see you using the platform and being a part of our journey :)
Would anyone like to share their
#bugbounty
story?
Or maybe you have some special requests or ideas…
1
0
6