Veza
@vezainc
Followers
368
Following
438
Media
740
Statuses
1K
Secure your identity access everywhere with Veza, the identity security company. #cloudsecurity #cybersecurity #identitysecurity
California, USA
Joined April 2022
🎙️ Just dropped: the latest episode of the Identity at the Center Podcast featuring @thakurtarun, Co-founder & CEO of Veza, and @philvenables, Strategic Security Advisor at Google. Watch the full episode:
0
0
1
Veza Chief Security & Trust Officer Mike Towers breaks down a hidden threat most security teams overlook—the financial impact of over-provisioned access. Check it out:
veza.com
Over-provisioned access drives cloud and SaaS waste. Learn how least privilege access control can cut costs and make security a business enabler.
0
0
0
New #IdentityRadicals episode! Tune in to hear Matt Hart (CSO, PTC) and Mike Towers (Chief Security & Trust Officer, Veza) discuss identity as the new perimeter.
veza.com
Explore why identity—not the network—is now the first line of defense. PTC CSO Matt Hart joins Identity Radicals to unpack zero trust, AI, and identity hygiene in today’s evolving threat landscape.
0
0
0
In this executive brief, Veza CISO Mike Towers makes the case that trust architecture is the real unlock for modern security programs. 📖 Read how today’s CISOs are shifting from defenders to enablers:
veza.com
Discover how building digital trust architectures empowers CISOs to drive business value and secure transformation in the era of identity-based risk.
0
0
1
Gartner has introduced the Identity Visibility and Intelligence Platform (IVIP) category. IVIP closes the gap between your identity stack and your security stack. It’s not about ripping out tools. It’s about giving you answers:.
veza.com
Discover what an Identity Visibility and Intelligence Platform (IVIP) is, why it matters now, and how it complements IAM tools like IGA, PAM, and IDPs.
0
0
0
Nathan Casey, who leads security at Veza and brings two decades of hands-on cybersecurity experience, breaks down how to perform an identity perimeter analysis — a practical, step-by-step framework. Check it out!
veza.com
Explore how identity has become the new cybersecurity perimeter. Learn practical steps for identity perimeter analysis to reduce risk, detect privilege escalation, and enforce controls like MFA in...
0
1
1
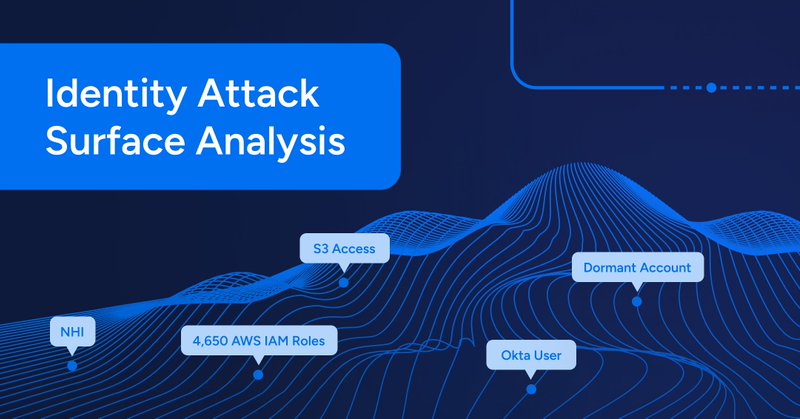
Humans are no longer the majority. Autonomous systems—bots, agents, workflows—are taking over. We call them non-human identities (NHI), and they’re redefining the identity attack surface. Veza’s Mike Towers breaks it down in this podcast episode:.
podcasts.apple.com
Podcast Episode · Crucial Tech · 07/09/2025 · 23m
0
0
0
Who’s Really Watching Your Vendors? In our latest blog, we unpack what effective third-party risk management (TPRM) looks like today. Check it out!.
veza.com
Discover how third-party risk management (TPRM) is critical for securing your enterprise. Learn best practices, challenges, and how to effectively govern vendor access to reduce risk and meet...
0
1
3
Your IGA isn’t broken—it’s just stuck. If your current identity governance system still does what it was scoped to do years ago, that’s not a win - that’s technical debt on autopilot.
veza.com
Legacy IGA tools weren’t built for today’s access risks. Learn why modernizing identity governance is essential for managing both human and non-human identities—and how platforms like Veza are...
0
0
0
In our latest post, we unpack why disconnected apps are a growing compliance and security concern - and how Veza brings them under governance using Open Authorization Access. Check it out -->
veza.com
Disconnected apps often live outside traditional IAM and IGA controls—creating governance blind spots and compliance risks. Learn how Veza helps extend access visibility and enforcement to every...
0
0
0
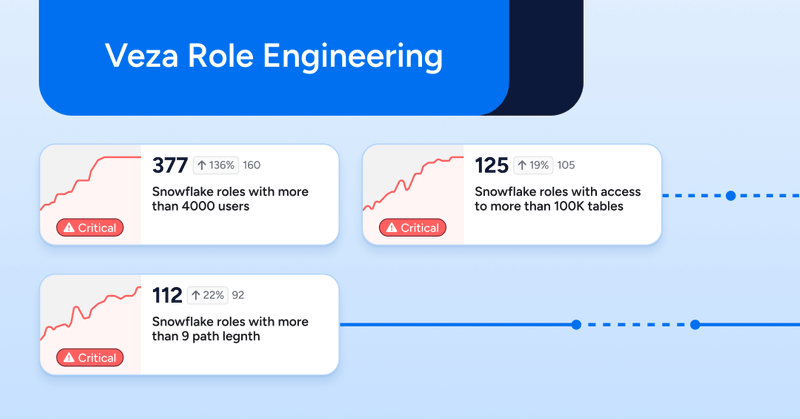
RBAC was supposed to bring order to access control. But in the real world? .Static roles decay, and fast. Least privilege turns into over-permissioned chaos. We’re bringing automation, analytics, and intelligence to the broken state of RBAC.
veza.com
Struggling with RBAC sprawl? Discover how Veza’s Role Engineering brings automation and intelligence to modern identity governance.
0
0
0
Learn how to turn detection into action - pairing Microsoft Defender for Identity with Veza’s access intelligence to operationalize identity risk.
veza.com
Learn how to reduce identity risk by combining Microsoft Defender for Identity’s behavioural analytics with Veza’s access governance. A practical guide to securing non-human identities and service...
0
0
0
Least privilege is achievable with Veza's Access AI. By combining Generative AI with Veza’s Access Graph, we’ve replaced rigid rule-based methods, allowing teams to ask access questions in natural language.
veza.com
Veza is the identity security company that enables organizations to understand, manage and control who can and should take what action on what data.
0
1
1
In the latest episode of Identity Radicals, Roland Cloutier joins Veza’s Mike Towers to explore the rising risks of non-human identities, the impact of AI, and what security leaders must do next. Watch now ➡️
veza.com
Roland Cloutier, former CSO of TikTok and ADP, joins Identity Radicals to break down the growing threat—and urgency—of machine identity management in a cloud and AI-first world.
0
0
0
We read the Verizon DBIR so you didn't have to. 🧠 The 2025 Verizon DBIR didn’t just confirm what we suspected—it put identity squarely in the crosshairs. Credential abuse is now the #1 way attackers get in. Learn more:
veza.com
Verizon’s 2025 DBIR reveals identity is now the #1 attack surface. Learn what CISOs and security pros must do to counter credential abuse, BYOD threats, and infostealers.
0
0
0
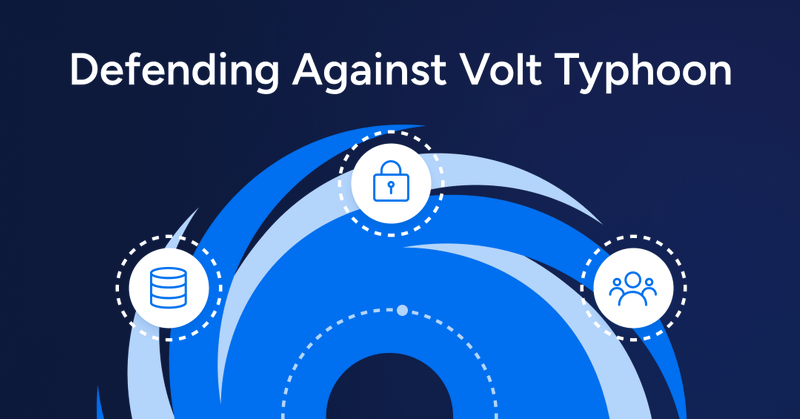
Volt Typhoon is redefining cyber warfare—targeting identities, not just systems. In our latest blog, we unpack the identity-centric tactics behind Volt Typhoon—and provide a blueprint for CISOs and security teams to fight back.
veza.com
Volt Typhoon is exploiting identity as the new attack surface. Learn how CISOs and security teams can detect and disrupt identity-centric APTs with Veza’s access intelligence platform.
0
1
1