Robert Tomkowski
@trodbert
Followers
175
Following
137
Media
3
Statuses
62
Software and security engineer. Currently working on his world domination plan as CEO of @hacking_dept and Head of R&D at @stm_cyber. Member of @p4_team.
Joined May 2020
RT @TheHackersNews: Popular PAX PoS systems used in countless stores worldwide are vulnerable to crippling attacks. Hackers could hijack t….
thehackernews.com
Popular PAX PoS systems used in countless stores worldwide are vulnerable to crippling attacks.
0
44
0
It's the tip of the iceberg :).
We are releasing the first wave of vulnerabilities targeting @paxtechnology PAX Android POS terminals. The list includes pre-auth RCE on the root account by exploiting a hidden bootloader functionality via USB. You can expect more POS CVEs soon™ :).
0
1
4
RT @stm_cyber: We are releasing the first wave of vulnerabilities targeting @paxtechnology PAX Android POS terminals. The list includes pre….
blog.stmcyber.com
In this article, we present details of 6 vulnerabilities on the Android POS devices made by the worldwide known company PAX Technology.
0
31
0
RT @gynvael: [PL] Oprócz Paged Out!, wypuściliśmy dzisiaj też wywiad z 𝗣𝗼𝗹𝗮𝗻𝗱 𝗖𝗮𝗻 𝗜𝗻𝘁𝗼 𝗦𝗽𝗮𝗰𝗲, tj. (@p4_team + @DragonSectorCTF + przyjaciel….
0
17
0
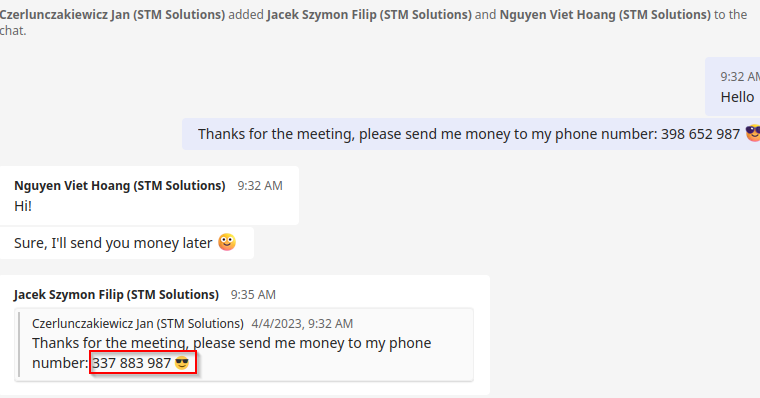
RT @stm_cyber: Our pentesters Janek and Szymon pranked us in our Microsoft Teams group using interesting phishing 🎣 trick!.Check out what t….
blog.stmcyber.com
Earlier this year, we discovered an interesting behavior in Microsoft Teams chat functionality that allowed us to phish our coworkers and earn a free pizza. By modifying the request it’s possible to...
0
3
0
RT @CERT_Polska: 🎆Zostaliśmy CNA czyli CVE Numbering Authority! Od dziś nadajemy podatnościom numery i dbamy o jakość bazy, która jest publ….
0
27
0
RT @p4_team: Get Ready! p4 ctf finals at #CS23_EXPO @CYBERSECEU starts in 17 hours!.Brace yourself for the clash of elite hackers from:.@ju….
0
11
0
RT @p4_team: p4 CTF 2023 teaser is over!.🥇@justCatTheFish.🥈 NeSE (Never Stop Exploiting).🥉 @r3kapig.Congrats to all players! Great hakz and….
0
13
0
RT @p4_team: Are you ready for a #cybersecurity challenge? Join the #p4ctf teaser contest on May 13th! The finals will take place at the Cy….
0
8
0
As 🇵🇱 we scored third 🥉 in #LockedShields2023. I had the pleasure of being the leader of the Web Application sub-team, which had the best score 🏆 in the whole NATO. We detected and fixed almost every vuln and threat 🛡️. With the best ppl and hard work, you can do anything!.
#LockedShields2023 has concluded! This year was even more competitive than previous years. As organisers, we saw a big jump in quality within the Blue Teams. The most effective participants were the 🇸🇪-🇮🇸 joint team, followed by the 🇪🇪-🇺🇸 joint team and the 🇵🇱 team. Good job!
1
2
19
See you in Vegas 🙂.
Today Poland Can Into Space placed fourth on @hack_a_sat qualifier and we're going to Vegas!.This year's finals will include hacking the Moonlighter platform on orbit! Can 🇵🇱🥫🚀 conquer real 🛰️? We'll find out during DEFCON 31.
0
1
0
RT @p4_team: p4ctf 2022 is over. The winners are C4T BuT S4D, @justCatTheFish and @id10t_ctf. Congrats!
0
14
0
Finally, I Have Them All
Third time's a charm! Once again @p4_team and @DragonSectorCTF have joined forces as the Poland Can Into Space team to conquer space 🇵🇱🚀🌌 and this time we did🏆! We won @hack_a_sat, the space security competition! Thanks to🥈SpaceBitsRUs and🥉@solarwine_ctf for a fierce fight!
0
0
5
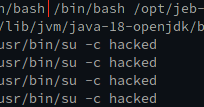
RT @stm_cyber: The best feature of the decompiler is one that spawns random processes and gives you a heart attack. Check out our story on….
blog.stmcyber.com
Finding RCE during deobfuscation in JEB decompiler running on Java 18.
0
14
0
RT @p4_team: Winner winner chicken dinner 🦆Poland stronk 🇵🇱 💪 Once again we won @hack_a_sat quals 🚀 together with @DragonSectorCTF and frie….
0
11
0
RT @hacking_dept: Poniżej zamieszczamy częściowe wyniki konkursu CYBERSEC CTF by HackingDept #CS22_EXPO.Zwycięzcom i wszystkim uczestnikom….
0
3
0
RT @hacking_dept: Jeżeli jesteś studentem spróbuj swoich sił!.Mija ostatnia szansa aby się zarejestrować i wziąć udział w konkursie i konfe….
0
3
0