Threatscape
@Threatscape
Followers
604
Following
39
Media
66
Statuses
267
#CyberSecurity solutions that perform at scale. We secure your critical IT assets at endpoints, across networks, and in the cloud.
London, UK & Dublin, Ireland
Joined August 2010
RT @yeti195: A big shoutout to @WillTheFrenchie @Threatscape for their help and expertise is helping me setup a zero trust conditional acce….
0
1
0
Huge congratulations to Nathan Hutchinson on becoming a Microsoft Security #MVP!. With his award in Identity & Access Management, Threatscape is now home to two Microsoft Security MVPs, demonstrating our expertise and commitment to the security community.
0
2
7
With attackers targeting user identities as their primary entry point, protecting access is no longer just an IT task; it’s a business imperative. #MicrosoftEntra #IdentitySecurity #CyberResilience.
threatscape.com
Microsoft Entra ID (formerly Azure AD) is a cloud-based identity and access management service. But what's included, and what are the business benefits?
0
0
1
In today’s threat landscape, trusting users or devices without rigorous verification is a recipe for disaster. Conditional access is the gatekeeper your organisation needs to enforce Zero Trust Security. #ZeroTrust #ConditionalAccess #CyberSecurity .
threatscape.com
Conditional access is the key to Zero Trust success. Find out the signals driving conditional access, and its practical applications for cyber security.
0
0
1
Even the best-intentioned policies can leave gaps, creating hidden vulnerabilities that attackers exploit. Avoid these five common mistakes and fortify your defences:. #ConditionalAccess #CyberSecurity #ZeroTrust.
threatscape.com
Conditional Access offers a powerful way to enhance security, but it's not without its complexities. Avoid these common mistakes to maximise identity security.
0
0
1
Your cloud isn’t as secure as you think. While cloud adoption accelerates, so do the risks—misconfigurations, exposed APIs, and shadow IT are leaving organisations vulnerable to attack. Check out the blog:. #CloudSecurity #Threatscape #CyberResilience.
threatscape.com
Understanding cloud vulnerabilities, including insecure APIs and weak access management, is key to maintaining a secure cloud-based business presence.
0
0
1
Adversary-in-the-Middle (AiTM) attacks are bypassing even the strongest Multi-Factor Authentication, exposing organisations to devastating breaches. 👉 Read our blog to protect against AiTM attacks. #CyberSecurity #AiTM #Threatscape #ZeroTrust.
threatscape.com
The risks associated with Adversary in The Middle (AiTM) attacks, how to detect an attack-in-progress, and protecting your organisation from AiTM threats.
0
0
2
🎙️ @rucam365 & @DeviceDeploy delve into 3 critical ways #Intune Endpoint Privilege Management (#EPM) protects local admin:. 1️⃣ User Confirmed Elevation.2️⃣ Automatic Elevation .3️⃣ Support Approved Elevation. Watch the full episode here: .
0
0
1
RT @rucam365: New video: 5 common Entra Conditional Access mistakes (and how to avoid them). Catch it here: Big sh….
0
17
0
We did it again! Delighted to be awarded Security Partner of the Year at the @Microsoftirl Partner of the Year awards last night. Huge thanks to the team for another incredible year!
0
0
3
RT @rucam365: Learned a ton chatting to @kj_ninja25 about Defender for Endpoint on @Threatscape's latest podcast:. • open-source tools for….
0
18
0
RT @TodayFM: Many different scams managed to dupe investors into giving over €9 million in 2023. Niamh Davenport, @BPFINews and Dermot Wil….
todayfm.com
Many different scams managed to dupe investors into giving over €9 million in 2023.Niamh Davenport, Head of Financial Crime with the Banking and Payments F...
0
1
0
Tune into TodayFM from 4.30 as our CEO Dermot Williams joins Matt Cooper on The Last Word 👇🏻.
📻From 4.30 @cooper_m. 🔵Spike in sophisticated investment scams @NiamhDavenport @Threatscape.🟡Farmers protest rising costs @farmersjournal @ShonaMurray_.🔵Zuckerberg told he has blood on his hands @ADODonoghue.🟡Preview the 2024 hurling season.🔵Plus environment, movies & more
0
0
0
RT @emmetjryan: Dermot Williams of @Threatscape is simply brilliant at explaining complex IT security issues in clear language. It was gre….
open.spotify.com
The Elio Business Podcast · Episode
0
10
0
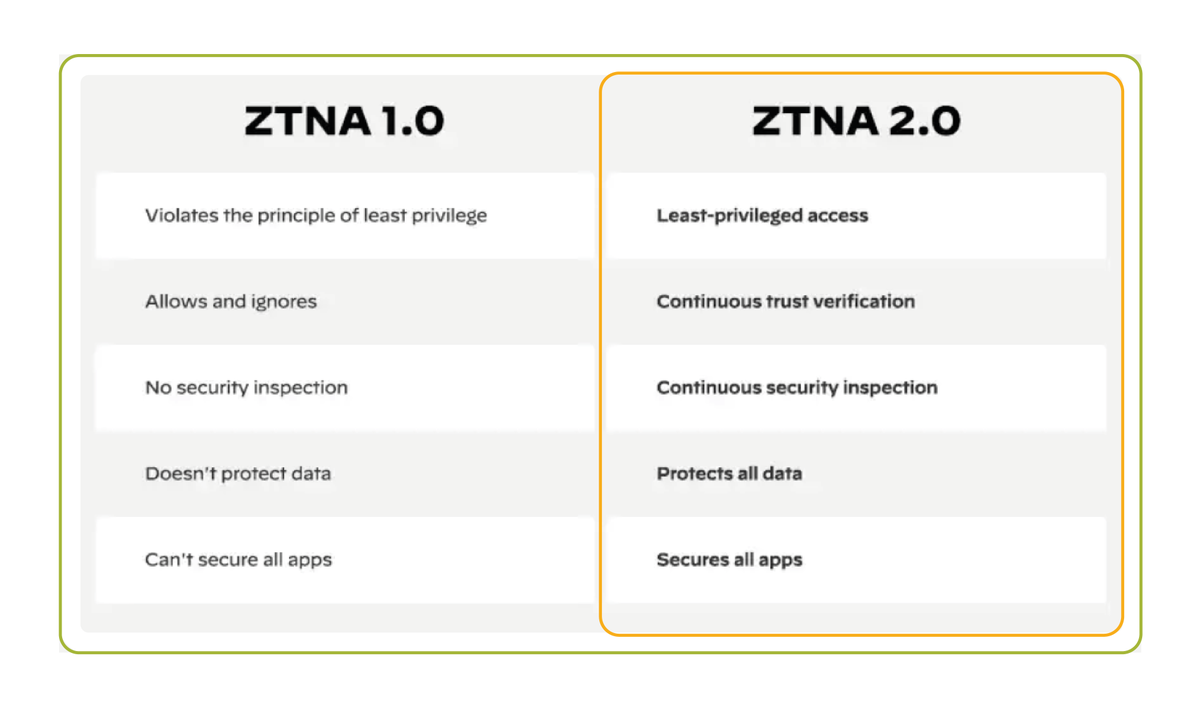
Does your organisation employ a Zero Trust model of verification? And if so, have you considered the move to ZTNA 2.0 in light of the fast-paced network security developments over the past few years? . Graphic source: @PaloAltoNtwks.#ZeroTrust #ZTNA #Cybersecurity #sase
0
0
1
Left of Bang – Get Ahead of Threats with Proactive Optimisation. Check out this blog to learn more: . #cybersecurity #proactivesecurity #incidentresponse #securityplanning #securityoptimization
0
1
0
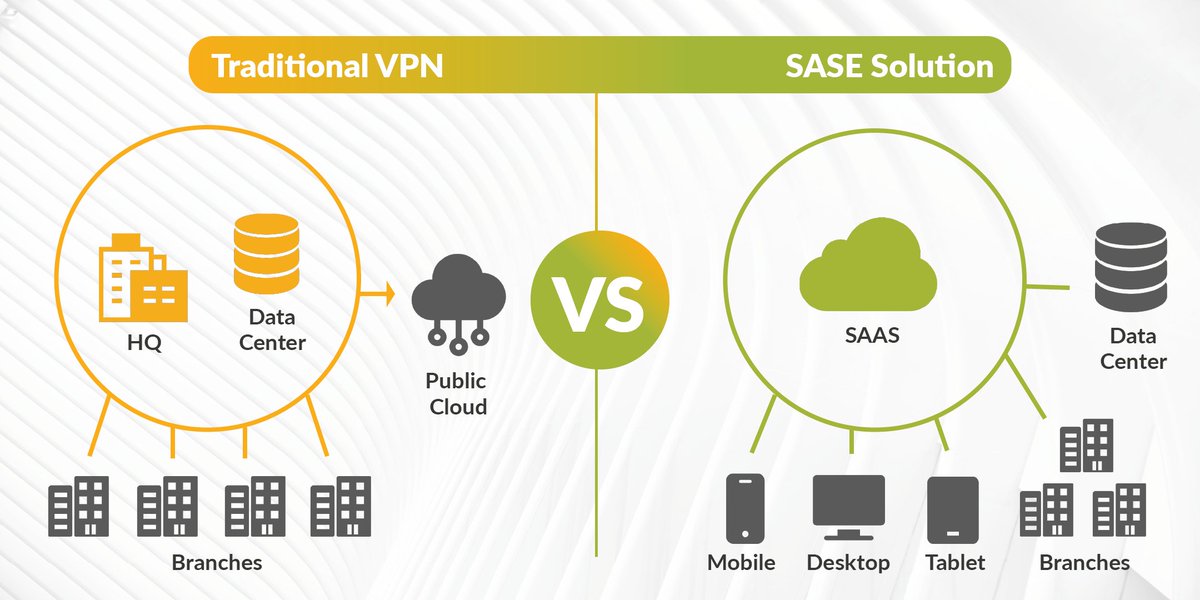
While VPN provides a secure tunnel for remote access to corporate resources, SASE provides a more comprehensive and integrated security solution making it a better choice. #SASEsecurity #CloudSecurity #RemoteWorkforce #Cybersecurity #VPN. *Read More*.
0
0
1
Learn about the key components of a SASE solution and how it can help you improve your security posture, increase visibility and control, simplify management, and reduce costs. Click the link to read the full article. #SASE #cybersecurity #cloud #ZTNA .
threatscape.com
A SASE is a security solution designed to enable businesses to fully and safely utilise cloud-based services while maintaining a robust network security posture
0
1
0
Is your business utilizing Microsoft 365 Security to its full potential? Download our eBook which outlines 10 key areas for optimization for a better security posture. #Microsoft365Security #Cybersecurity #M365security #securitybestpractices.
threatscape.com
Maximising Security Optimisation for M365 using these 10 settings recommended by cyber security experts at Threatscape
0
1
3
The opportunities with M365 E3 or E5 are endless, but with so many capabilities at your fingertips. are you making the most of them? And even if you are, it can be confusing and insecure out of the box. Meet Overwatch for #M365Security 👇🏻.
0
1
0