Sysdum
@systemDumb
Followers
571
Following
443
Media
21
Statuses
239
Synack Red Team | Coder | Bug Bounty Hunter Interested in desktops, tabletops, all kinds of tops really.
Joined January 2020
If you think you've found a path traversal, instead of throwing /etc/passwd and similar paths, check if the app is java-based using Wappalyzer. I've scored a few bounties by trying the following:. ?file=. /WEB-INF/web.xml.?file=. /META-INF/MANIFEST.MF.#bugbountytips #BugBounty.
1
0
3
RT @adragos_: Finished in 1st place at the Red Team CTF @ #DEFCON 31. @RedTeamVillage_ . Started off playing the event solo, but I was join….
0
9
0
RT @RedTeamVillage_: 🚨 Attention 🚨 . We’re asking everyone that was at the RTV CTF today in Cesar’s Forum to CHECK their swag bags. Unfortu….
0
52
0
RT @pwnEIP: Swag packing day! We're all busily packing for the big show. @systemDumb @j0nk1m @santosomar @lazzslayer @ds1nk @NopResearcher….
0
14
0
RT @trick3st: We've recently added jsluice by @bishopfox to our library, a great tool for uncovering URLs, paths, secrets and more from Jav….
0
17
0
RT @piedpiper1616: GitHub - vchan-in/CVE-2023-35078-Exploit-POC: CVE-2023-35078 Remote Unauthenticated API Access Vulnerability Exploit POC….
0
29
0
RT @liadeliyahu: Exploit is so easy it fits in a tweet🔥.unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;.setcap cap_setuid+eip l/pytho….
0
276
0
RT @RedTeamVillage_: 🔴 Red Team Village presents another exclusive interview with our amazing sponsor, @buddobot with @Jhaddix, now availab….
0
9
0
RT @infosec_au: shout out to all the brave engineers who decided to write VPN appliances in C.
0
16
0
RT @pwnEIP: Overdone meme but so real right now. You can feel the energy of 1000's of speakers, instructors, organizers, and volunteers hus….
0
16
0
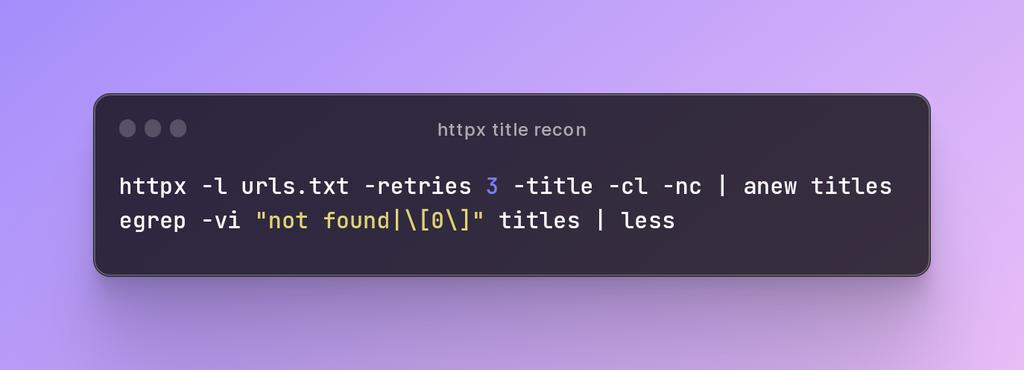
Web servers handing you a fake 200 during recon? Pipe the results to a file and use grep -v to pull out garbage responses. You can use | as an OR operator with egrep to filter out WAF/custom 404s. #bugbountytips #bugbounty
2
2
6
RT @RedTeamVillage_: Guess who’s back. Back again. Red Team Village is back, tell a friend…👀 😈. @defcon #DC31
0
56
0
Recently found an SSRF domain white list bypass. The app was looking for vulnerable[.]com in the request. I made a CNAME on my domain pointing to localhost, allowing for internal service access. vulnerable[.]com.mydomain[.]com --> 127.0.0.1.#bugbountytip #bugbounty.
0
1
4