StrongBox IT
@strongboxit
Followers
71
Following
19
Media
710
Statuses
951
Strongbox IT collaborates with IT companies by providing complete Security solution to secure their web applications and infrastructure. Modshield SB -
Chennai, India
Joined August 2017
🔐 GDPR vs DPDP: What’s the Real Difference?.Both laws aim to protect personal data, but their scope, rights, and enforcement vary. Swipe through to learn how India’s #DPDP stacks up against the EU’s #GDPR. 💡 Stay compliant. Stay secure. #DataPrivacy #CyberSecurity #Compliance
0
0
0
Simplify Your SOC 2 Compliance Journey!. From identifying gaps to fixing controls, we guide you through every step to ensure your business meets SOC 2 compliance standards with ease. Learn more: #SOC2Compliance #CyberSecurity #StrongBoxIT #SOC2Audit
0
0
0
Compliance gaps are silent threats!.Many SMBs unknowingly leave gaps that hackers and regulators won't overlook. Swipe through to discover the 6 common compliance gaps SMBs must fix now. #Compliance #GDPR #ISO27001
0
0
0
🔐Secure Your Access Like a Pro.▶️Follow these 8 Credential Management Best Practices to keep hackers out and data safe. #CyberSecurity #CredentialManagement #InfoSec #DataProtection #IdentitySecurity #CyberAwareness #ITSecurity #StrongPasswords #MFA #SecureAccess
0
1
3
🔐 Cybercrime is set to cost the world $10.5 trillion by the end of 2025. Here’s how smart companies are fighting back with strategy, tech, and resilience. 💻⚔️.#CyberSecurity #DataProtection #Infosec #CyberThreats #BusinessSecurity #RiskManagement #Cybercrime
0
0
2
6 Million Records Exposed in Qantas Breach — Just Days After FBI's Industry Warning.Follow us - #cyberattacks #Qantas #Qantasairlines #Australia #databreach #CybersecurityNews
0
0
1
🔐Types of IoT Security You Must Know.Uncover the different types of IoT security that protect your data, devices, and networks from breaches and bad actors. ➡️ Slide to learn more.#IoTSecurity #CyberSecurity #SmartDevices #NetworkSecurity #DeviceAuthentication #SecureIoT #Tech
0
0
0
🔍 IAST vs RASP – What's the difference?.Discover how these app security tools detect threats, secure your code, and defend in real-time! 🛡️💻.Swipe through to learn more ➡️.#IASTvsRASP #AppSecurity #CyberSecurity #DevSecOps #IAST #RASP #SecureCode #RealTimeProtection
0
0
0
🚨 16 billion passwords leaked in 2025's biggest data breach!.Not just a hack — it's a blueprint for mass exploitation. 🔗Read: #CyberSecurity #DataLeak #Passwords #InfoSec #HackAlert
0
0
1
🚨 Your business could be one click away from a major breach. Know the most common cyber attacks targeting organizations today. #CyberResilience #SOC #Ransomware #BreachAlert #VAPT #CyberSecurity #CyberRisk #vaptservices
0
0
1
Fake CAPTCHA = new malware trap! 🐛🚫 Don’t click “I’m Not a Robot” until you know the risks. Follow us - #CyberSecurity #Malware #Phishing #OnlineSafety #TechNews
0
0
1
🛡️ StrongBox IT’s expert-led Endpoint VAPT secures your laptops, mobiles & more. 🔍 Identify threats.⚙️ Simulate real attacks.✅ Stay compliant.Strengthen your last line of defense. 👉 #VAPT #EndpointSecurity #CyberSecurity #I
0
0
1
EchoLeak: First-Ever Zero-Click AI Security Flaw. A quiet flaw in an AI assistant showed how even smart tech can go wrong — without a single click. As AI advances, our security must too. Follow us & stay updated : #EchoLeak #AIsecurity #CyberAwareness
0
0
0
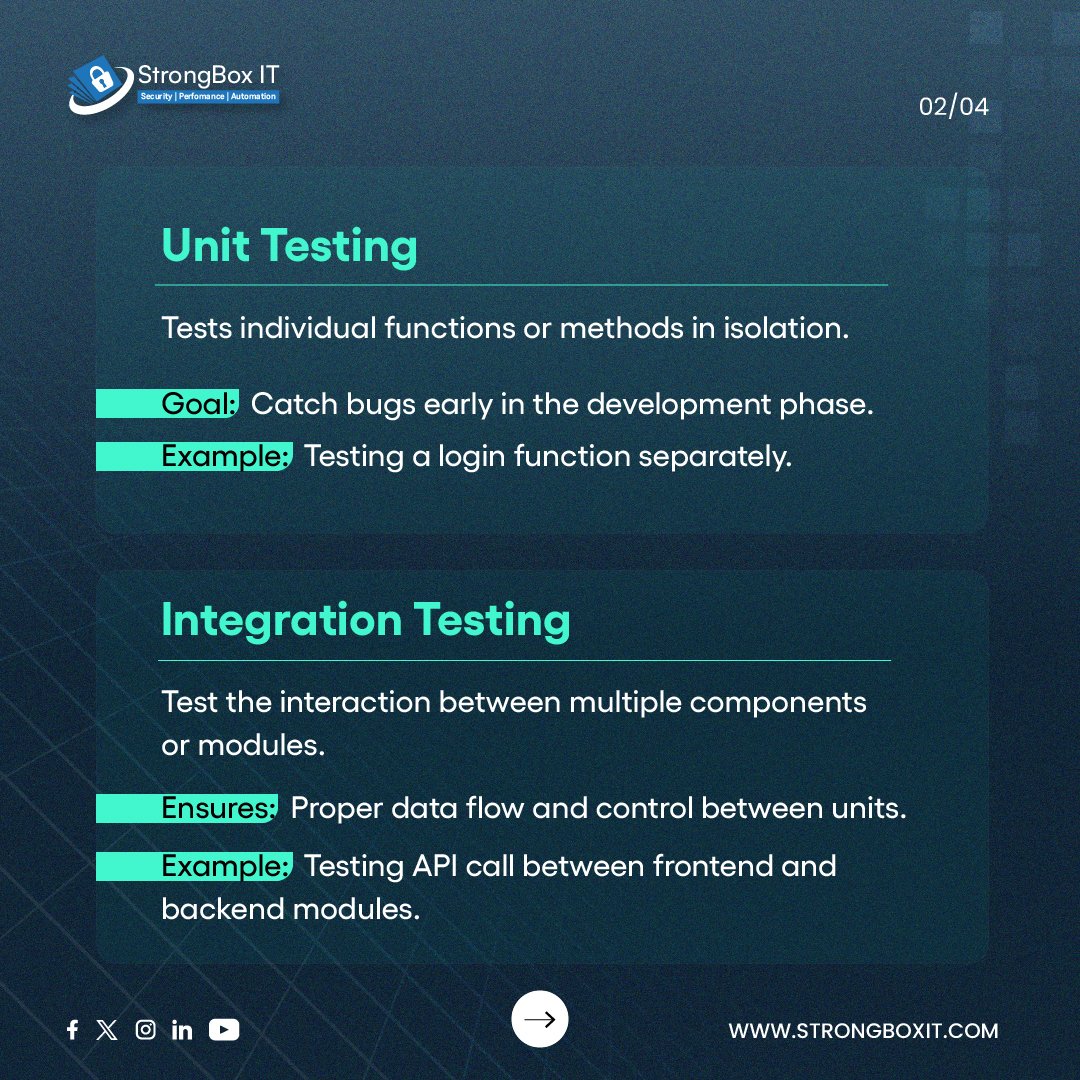
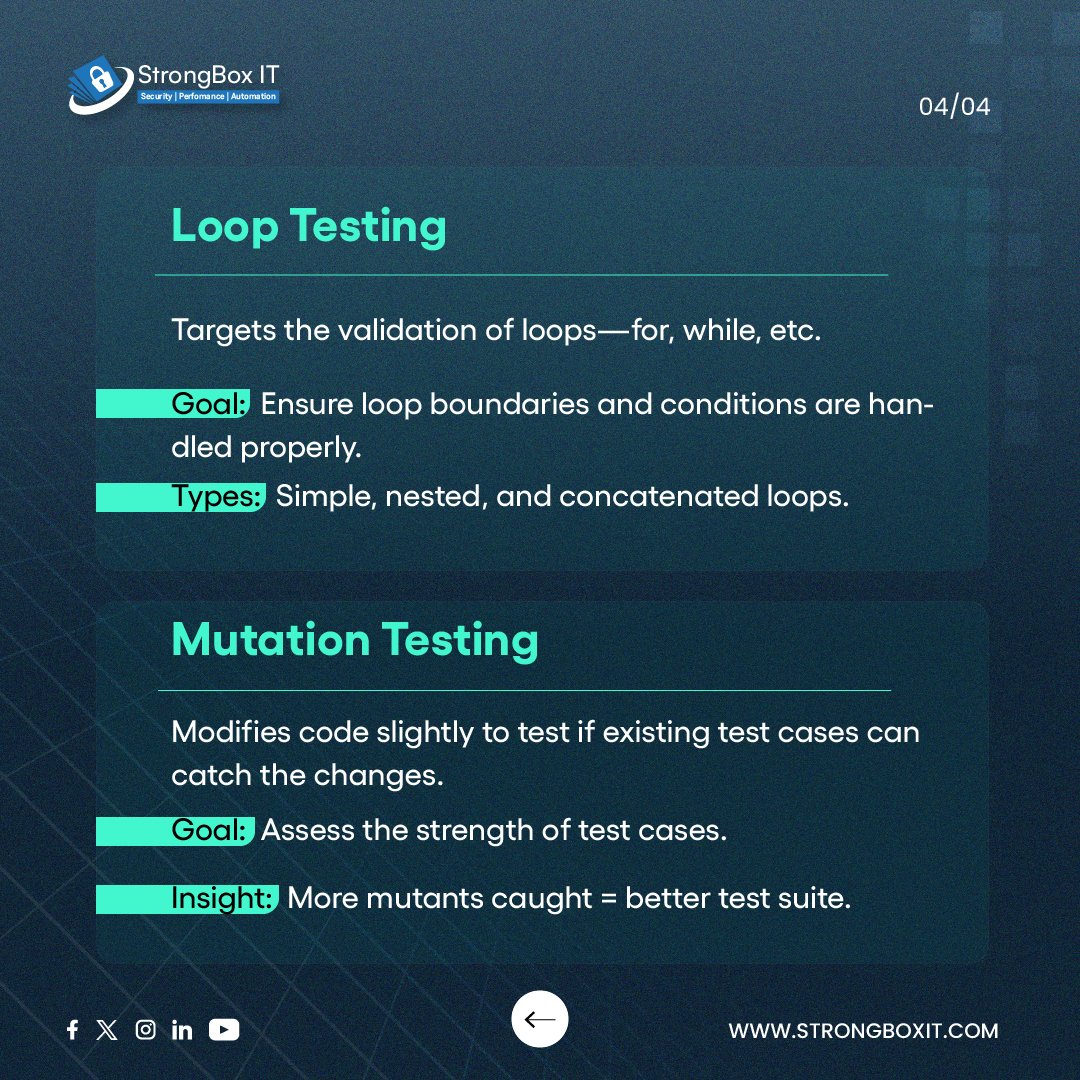
White Box Testing isn’t just one type It covers a range of testing types that examine the inner workings of code — structure, logic, and flow. This post breaks down the types used to ensure clean, reliable, and secure software. #WhiteBoxTesting
0
0
0
Why choose one when you can align all three?. a unified compliance strategy can cut through complexity, enhance your security posture, and build greater client trust. Read the full blog 👉 #CyberSecurity #ComplianceStrategy #ISO27001 #SOC2 #GDPR.
0
0
0
Asymptomatic doesn’t mean safe. Zero Knowledge Cyber Attacks operate in stealth, bypassing your defenses without a sound. 🎥 Watch the video to uncover what you never saw coming. #CyberSecurity #ZeroKnowledgeAttack #HiddenThreats #StaySafeOnline
0
0
0
Not all clouds are safe — without the right Cloud Security Assessment. From identifying assets to scanning for vulnerabilities, every step matters in securing your cloud environment. Know the process and keep your cloud secure. #CloudSecurity
0
0
0
Not all threats break in — some just log in. HEAT attacks hide in browsers & cloud apps, using trusted tools against you. Stay updated on modern threats with StrongBox IT. #HEATattacks #Cybersecurity #LivingOffTheLand #ZeroTrust
0
0
0