pygrum
@spygrum
Followers
96
Following
45
Media
3
Statuses
12
opinions are not my own, im being controlled
Joined May 2023
RT @0xLegacyy: Developing a scriptable (pwndbg-like) debugger for windows. Few more things we need to iron out but will be releasing soon 🐸….
0
19
0
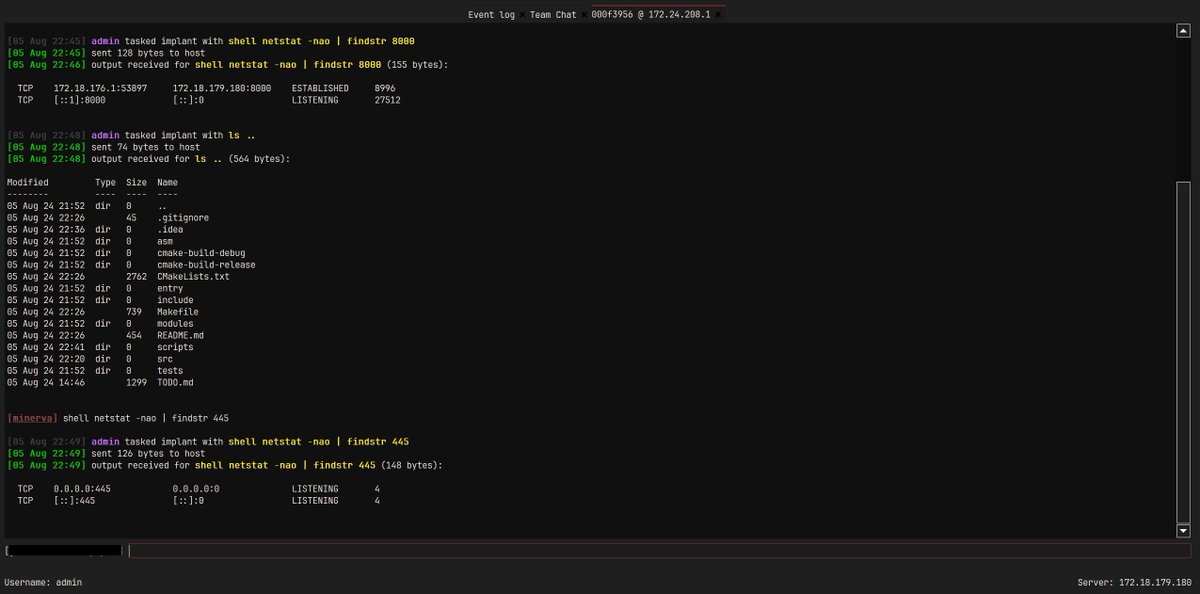
I've most recently added liveness info for registers / flags. No more pushf / popf pairs to make things a bit harder for analysts \( -_-)/
github.com
Rewrite and obfuscate code in compiled binaries. Contribute to badhive/stitch development by creating an account on GitHub.
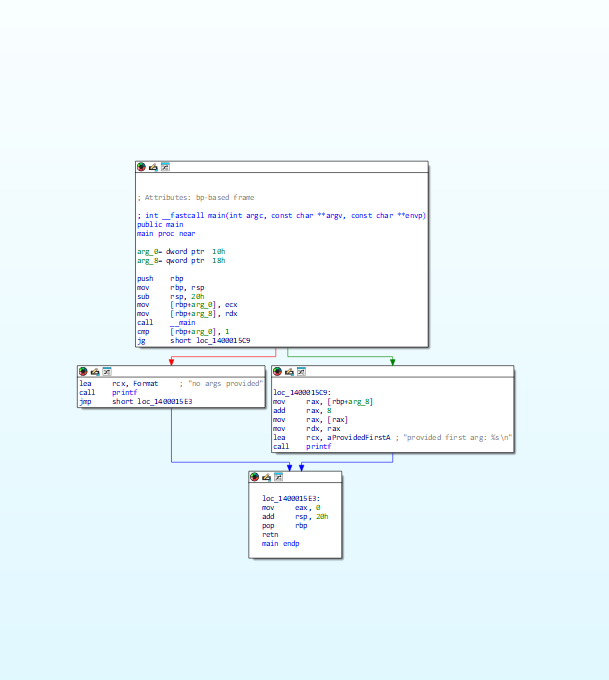
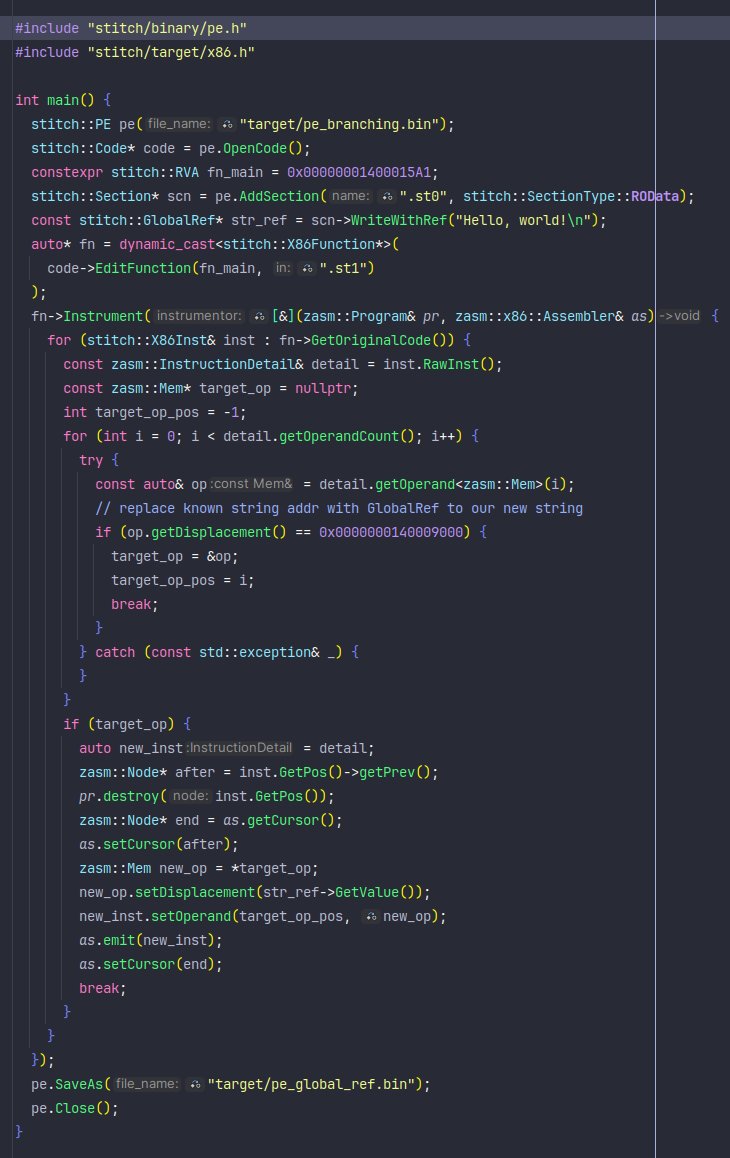
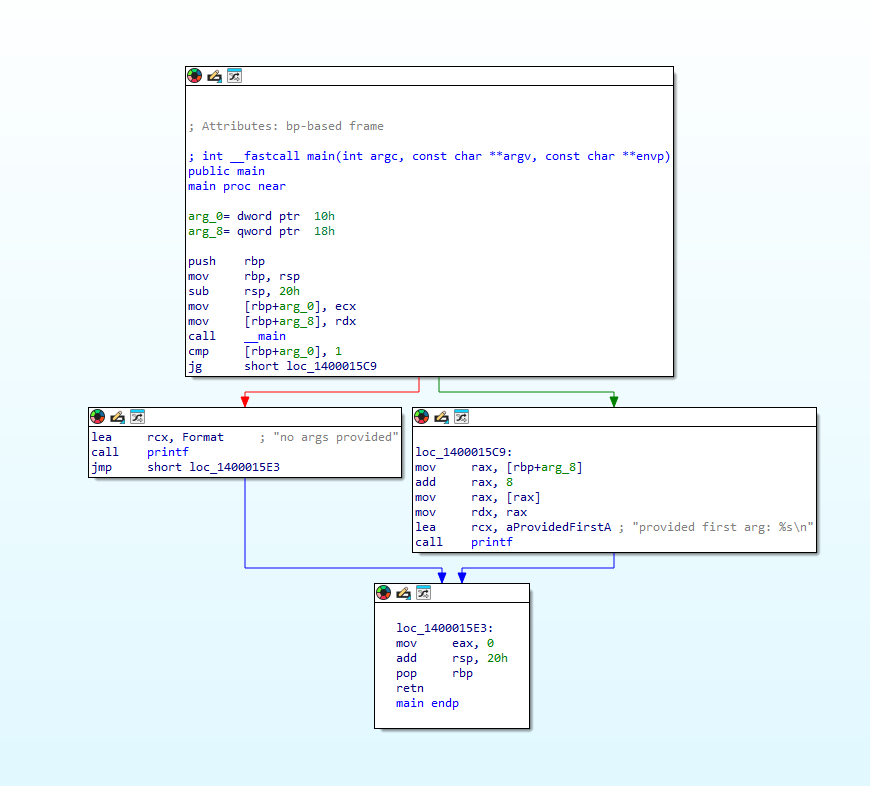
Wrote a cross-platform library for rewriting / modifying code in executable files on a function level. Pretty simple to write advanced binary obfuscators using it. Below shows what ~30 LOC using Stitch transforms a function into:
0
0
8
I've finished most of the development for Governor, the flagship Windows 'sensor' / telemetry source for the ALCA engine. Governor can now be used alongside ALCA for dynamic signaturing of Windows malware .
github.com
Flagship Windows Sensor for the ALCA Engine. Contribute to badhive/governor development by creating an account on GitHub.
0
2
7
Been working on a rule engine for dynamic malware analysis - ingests telemetry from a 'sensor' and runs rules and sequences of rules on event data it receives. Currently writing the flagship sensor, but the library itself is available to experiment with:.
github.com
Rule Engine for Dynamic Malware Analysis and Research - badhive/alca
0
3
9
Gimmick - an in-memory payload obfuscation technique & POC via thread-safe, on-demand section decryption.
github.com
Section-based payload obfuscation technique for x64 - pygrum/gimmick
1
6
39