Sam Stepanyan
@securestep9
Followers
7K
Following
11K
Media
1K
Statuses
5K
@OWASPLondon Chapter Leader (#OWASP #OWASPLondon). OWASP Board Member. Application Security (#AppSec) Consultant. OWASP #Nettacker Project co-leader. #CISSP
London, UK
Joined September 2013
#Gemini Zero-Click #Vulnerability Let Attackers Access Gmail, Calendar, and Docs. No clicks or warnings were needed. An attacker simply shared a poisoned Google Doc, Calendar invite, or email embedding hidden prompt injections. #AISecurity 👇
cybersecuritynews.com
A critical zero-click vulnerability dubbed "GeminiJack" in Google Gemini Enterprise and previously Vertex AI Search that let attackers siphon sensitive corporate data from Gmail, Calendar, and Docs...
0
0
3
#OWASP Agentic AI Summit has started in London! You can watch the 📺 live-stream here: 👇 https://t.co/ts2tuSrJgI
0
1
4
Quickly and easily evaluate borrowers' income with our award-winning Income Calculator. Let our technology work harder for you, so you can do great work for your borrowers. Learn more.
4
21
162
The official #OWASP Training is coming to London in February 2026!🇬🇧💂♂️ Register now:
Fantastic trainers, top-tier content, and a chance to kick off the new year by upskilling alongside like-minded members of the community, what��s not to love? Register now for our first-ever OWASP London Training Days! https://t.co/eJDbr1e9HG
#appsec #training #cybersecurity
0
1
4
#Swiss government urges citizens to ditch #Microsoft365 and other #Cloud providers due to lack of proper E2E encryption citing US Cloud Act requirement to hand over data to US authorities, even if it’s stored in Switzerland: #DataSecurity 👇 https://t.co/nsQL6FvCnO
techradar.com
Switzerland is worried about data privacy
0
0
3
#Wordpress: 100,000+ WordPress Websites Affected by Remote Code Execution (#RCE) #vulnerability in Advanced Custom Fields Plugin: 👇 https://t.co/jt1ID95ruU
wordfence.com
100,000 WordPress Sites Affected by Remote Code Execution Vulnerability in Advanced Custom Fields: Extended WordPress Plugin
0
0
1
#VSCode: 24 malicious VS Code and #OpenVSX extensions are stealing developer credentials - spreading through popular names like Flutter, React, and Tailwind. Full list of malicious VSCode extensions in the article below: #SoftwareSupplyChainSecurity 👇 https://t.co/PBzTnsuzb0
thehackernews.com
GlassWorm spreads again using 24 fake extensions across Visual Studio Marketplace and Open VSX, hiding Rust implants & Solana-based C2 to target devs.
0
0
0
#npm: Malicious NPM Package eslint-plugin-unicorn-ts-2 Uses Hidden Prompt and Script to Evade #AI Security Tools: #SoftwareSupplyChainSecurity 👇 https://t.co/ilkaKNNc2k
thehackernews.com
Malicious npm package mimics an ESLint plugin, embeds an AI-tricking prompt, and steals environment variables via a post-install script.
0
1
0
Brand new #OWASP #Top10 for Agentic #AI Applications is ready and we are privileged to have @JohnSotiro presenting a deep dive into the #Agentic Top 10 risks at the last @OWASPLondon meetup. If you missed it - watch the recording: 👇
Many thanks to John Sotiropoulos (@JohnSotiro) for presenting a talk on the #OWASP Top 10 for Agentic #AI Applications at the #OWASP London Chapter meetup last week! The video recording is now available to watch on the #OWASPLondon YouTube channel 📺: 👇 https://t.co/bV3PaTZcoB
0
2
5
Many thanks to Dr Katie Paxton-Fear (@InsiderPhD) for presenting her talk "AI Agents gone Rogue" at the #OWASP London Chapter meetup last week! The video recording of the talk is now available to watch on the #OWASPLondon YouTube channel 📺: 👇 https://t.co/VRFrD5ASLs
1
5
9
#OpenAI API Data Breach: OpenAI has disclosed a #databreach affecting some API customers due to a hack at third-party vendor #Mixpanel. What was exposed: Names & Emails, Approximate Location, UserID/Org IDs 👇 https://t.co/jitPeKgn9h
bleepingcomputer.com
OpenAI is notifying some ChatGPT API customers that limited identifying information was exposed following a breach at its third-party analytics provider Mixpanel.
0
0
0
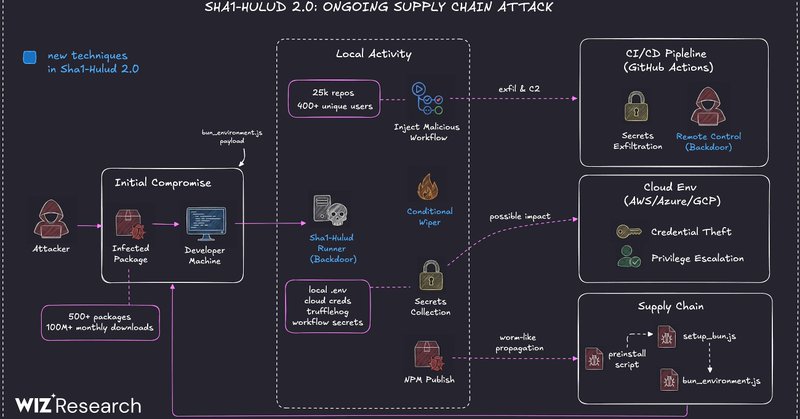
#Maven: hundreds of packages just got caught running Shai-Hulud v2 - the same malware that hijacked npm two days ago. It spread through automated rebuilds, infecting devs who never used npm stealing & leaking secrets across thousands of GitHub repos: 👇
thehackernews.com
Shai-Hulud v2 breached npm and Maven, impacting 28,000+ repos and leaking 11,858 secrets.
0
0
0
Over 80,000 files with #passwords and keys from governments, banks, and tech firms were found online pasted into public code tools like #JSONFormatter and #CodeBeautify. Cybercriminals are already scraping and using the data. And yes - it’s still live! 👇
thehackernews.com
Researchers uncovered 5GB of leaked credentials from JSONFormatter and CodeBeautify, exposing sensitive data across critical sectors.
0
0
0
#NPM: Second Shai-Hulud Infection Wave Affects 25,000+ Repositories via npm Preinstall Credential Theft: #SoftwareSupplyChainSecurity 👇 https://t.co/hCo216Ta5Q
thehackernews.com
Security vendors warn Sha1-Hulud has hijacked 25,000+ GitHub repos via npm packages, stealing cloud credentials or wiping dev home directories.
0
0
0
#AWS launched Agentic AI Security Scoping Matrix – a framework designed to help organizations securely deploy autonomous AI systems: #AISecurity 👇 https://t.co/IJADpvlFrm
aws.amazon.com
As generative AI became mainstream, Amazon Web Services (AWS) launched the Generative AI Security Scoping Matrix to help organizations understand and address the unique security challenges of...
0
7
5
The NPM module `glob` (230M downloads per week) packages a command-line tool that includes a command injection flaw. This high-severity vulnerability (CVE-2025-64756 CVSSv3=7.5) allows malicious file names to serve as injection vectors for code exection.. Vulnerability affects
0
2
4
#WhatsApp: Largest data leak in history - the entire directory of 3.5bln of WhatsApp was available online unprotected for retrieval. Austrian researchers were able to download all phone numbers, profile pictures & data including public keys: 👇 https://t.co/XwVvKElleI
heise.de
Vienna researchers retrieved all WhatsApp numbers. The 3.5 billion profiles represent the largest data leak in history—and it's worse than you might think.
1
1
2
#Cloudflare: A Cloudflare outage is taking down big parts of the internet: #CloudflareDown 👇 https://t.co/bnejfVnz0b
techradar.com
Cloudflare issues fixed following major outage
0
0
0
#GitHub: Downdetector and social media platforms are currently filled with reports about a GitHub outage, and the official GitHub Status portal has confirmed the problem: #GitHubDown 👇 https://t.co/55k1Dwqc18
howtogeek.com
Hope you didn't need to work today.
0
0
0
#Cloudflare: Cloudflare apologises for outage which took down most of the Internet today, including X and ChatGPT: #CloudflareDown
https://t.co/VZq5BpYQyb
bbc.co.uk
"We apologise to our customers and the Internet in general" the web infrastructure company said.
0
0
1
#Fortinet: Critical vulnerability in Fortinet FortiWeb (CVE-2025-64446), is under active exploitation - CISA adds it to KEV catalog: https://t.co/2a6TpK2iTd
cybersecuritydive.com
The company faces criticism as multiple researchers claim a silent patch was issued weeks before official guidance was released.
0
0
1