sctocs
@sctocs25
Followers
1
Following
0
Media
243
Statuses
316
SCtoCS provides threat intelligence and security services to protect you from cyber threats. Learn more: https://t.co/vv1te0p45H
USA
Joined August 2025
Russia-linked hackers are using Microsoft 365 device code phishing to hijack accounts — tricking users into entering authentication codes that hand over valid access tokens. Stay vigilant with meeting invites and phishing lures! 🔗
sctocs.com
Russia linked threat actors are using Microsoft 365 device code phishing to hijack accounts, enabling stealthy access and long term compromise.
0
0
0
Cracked software and YouTube videos are being used to spread CountLoader & GachiLoader malware. These loaders can deliver data-stealing payloads and compromise systems. Stay safe—avoid pirated software! 🔗
sctocs.com
Threat actors are abusing cracked software and YouTube videos to distribute CountLoader and GachiLoader malware to unsuspecting users.
0
0
0
WatchGuard warns of active exploitation of a critical Fireware OS VPN flaw (CVE-2025-14733)! Attackers can execute arbitrary code on Firebox devices via IKEv2 VPN. Patch now! 🔗
sctocs.com
WatchGuard is warning about active exploitation of a critical Fireware OS VPN vulnerability, urging organizations to apply fixes immediately.
0
0
0
Arrest made in major Microsoft 365 phishing case! Nigeria Police, with help from Microsoft & FBI, detained the main developer of the RaccoonO365 phishing toolkit used to steal Microsoft 365 credentials via fake login pages. 🔗
sctocs.com
Nigerian authorities have arrested the developer behind RaccoonO365 phishing tools linked to widespread Microsoft 365 credential theft attacks.
0
0
0
Cisco warns of active attacks on unpatched AsyncOS 0-day (CVE-2025-20393)! China-linked actors are exploiting a critical flaw in Secure Email Gateway & Web Manager appliances. Restrict exposure & harden now — no patch yet. 🔗
sctocs.com
Cisco is warning about active attacks exploiting an unpatched zero day vulnerability in AsyncOS email security appliances, urging immediate mitigation.
0
0
0
North Korea-linked hackers stole $2.02B in crypto in 2025, accounting for most global thefts and marking a record year for state-affiliated cybercrime. https://t.co/vUdvC8KzRI
sctocs.com
North Korea linked hackers stole 2.02 billion dollars in cryptocurrency in 2025, making them the top source of global crypto theft activity.
0
0
0
China-aligned threat actor uses Windows Group Policy to spread malware LongNosedGoblin deploys custom espionage tools like NosyHistorian & NosyDoor across compromised government networks using Group Policy, with C&C via OneDrive/Google Drive. 🔗
sctocs.com
A China aligned threat group is using Windows Group Policy to deploy espionage malware, enabling stealthy compromise of targeted environments.
0
0
0
Critical HPE OneView RCE (CVSS 10.0) Unauthenticated attackers can execute code remotely on HPE OneView systems (all versions before v11.00). Patch ASAP — hotfixes & v11.00 available. 🔗
sctocs.com
A critical HPE OneView vulnerability rated CVSS 10.0 allows unauthenticated attackers to execute remote code, posing severe risks to enterprise systems.
0
0
0
Kimsuky mobile malware alert The North Korea-linked group is spreading DocSwap Android malware via QR phishing disguised as a delivery app — granting remote access once installed. 🔗
sctocs.com
Kimsuky is distributing DocSwap Android malware using QR code phishing that masquerades as a delivery app, targeting unsuspecting mobile users.
0
0
0
CISA flags ASUS Live Update flaw (CVE-2025-59374) This critical vulnerability — tied to a past supply chain compromise and now actively exploited in the wild — was added to CISA’s KEV catalog. Discontinue or patch ASUS Live Update ASAP. 🔗
sctocs.com
CISA has flagged a critical ASUS Live Update vulnerability after confirming active exploitation, warning users to patch systems immediately.
0
0
0
SonicWall security update SonicWall patched CVE-2025-40602 — an actively exploited privilege escalation bug in SMA 1000 appliances that could lead to root RCE when chained with another flaw. Patch ASAP. 🔗
sctocs.com
SonicWall has fixed the actively exploited CVE-2025-40602 vulnerability affecting SMA 100 appliances, urging users to apply updates immediately.
0
0
0
Kimwolf botnet hijacks ~1.8 M Android TVs! Threat actors are using compromised Android TV boxes to launch huge DDoS attacks, proxy traffic, and more. Patch/secure your devices now. 🔗
sctocs.com
The Kimwolf botnet has taken over 1.8 million Android TVs and is using them to conduct large scale DDoS attacks worldwide.
0
0
0
APT28 phishing campaign targeting UKR(.)net users! Russian state-linked APT28 is running a long-running credential-harvesting operation using fake https://t.co/s4TSbzUjRU login pages and PDF lures to steal credentials and 2FA codes. 🔗
sctocs.com
APT28 is running a long term credential phishing campaign targeting Ukrainian UKR net users, aiming to steal accounts and gather intelligence.
0
0
0
ForumTroll phishing attacks hitting Russian scholars Fake eLibrary emails are being used to steal credentials and spread malware. Be cautious, verify senders! 🔗
sctocs.com
ForumTroll phishing campaigns are targeting Russian scholars using fake eLibrary emails to steal credentials and conduct targeted espionage.
0
0
0
GhostPoster malware in Firefox add-ons! 17 compromised extensions (50,000+ downloads) hid malicious JS inside logo icons to hijack links, inject tracking, and commit ad fraud. Remove suspicious extensions now! 🔗
sctocs.com
GhostPoster malware has been found embedded in 17 Firefox add ons with more than 50,000 downloads, posing serious risks to user security.
0
0
0
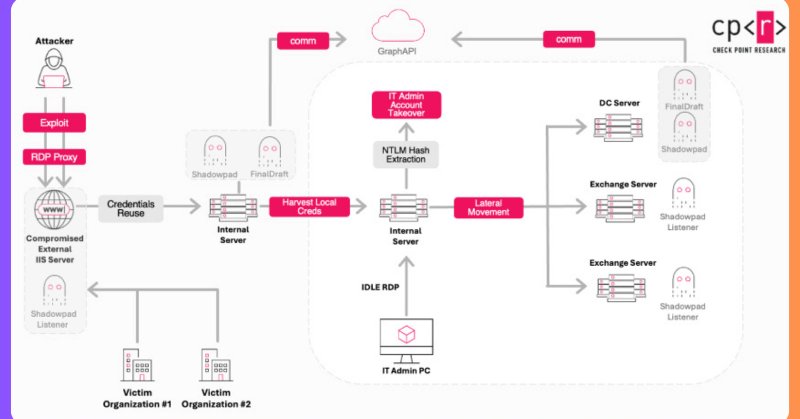
China-linked Ink Dragon cyber espionage uncovered Govts targeted using ShadowPad & FINALDRAFT malware; compromised servers turned into covert C2 nodes. Patch and monitor now. 🔗
sctocs.com
China linked Ink Dragon is targeting government entities using ShadowPad and FINALDRAFT malware in ongoing cyber espionage operations.
0
0
0
AWS crypto mining campaign uncovered Compromised IAM credentials are being used to fuel a large-scale crypto mining operation in AWS. Monitor usage and lock down IAM access now. 🔗
sctocs.com
Stolen IAM credentials are being abused to run a large scale AWS crypto mining campaign, leading to cloud resource abuse and financial losses.
0
0
0
Malicious NuGet package alert A fake Tracer Fody NuGet package is stealing cryptocurrency wallet data. Developers should audit dependencies and remove rogue packages immediately. 🔗
sctocs.com
A rogue NuGet package pretending to be Tracer.Fody is stealing cryptocurrency wallet data from developers, raising supply chain security concerns.
0
0
0
FortiGate under active attack A SAML SSO authentication bypass is being actively exploited in Fortinet FortiGate devices. Patch immediately and review access logs. 🔗
sctocs.com
Fortinet FortiGate devices are under active attack through a SAML SSO authentication bypass flaw, putting enterprise networks at risk.
0
0
0
React2Shell security alert Active exploitation of React2Shell is being used to deploy Linux backdoors. Patch exposed applications and monitor servers urgently. 🔗
sctocs.com
The React2Shell vulnerability is being actively exploited to deploy Linux backdoors, allowing attackers to gain persistent access to affected systems.
0
0
0