Riptides
@riptidesio
Followers
21
Following
0
Media
0
Statuses
25
Riptides is a comprehensive solution for securing workload-to-workload communication, with identity as its foundation.
San Francisco
Joined March 2025
Riptides brings identity-first, zero-trust security to Kafka without requiring any code or configuration changes. We transparently upgrade every connection to mTLS and eliminate secret sprawl, keystores, and operational overhead, all at the kernel layer. https://t.co/zPut2rc7D1
riptides.io
Riptides brings identity-first, zero-trust security to Kafka with no application changes, eliminating secrets, automating mTLS, and removing the operational burden of managing keystores and trustst...
0
3
3
Riptides’ Conditional Access delivers time-aware, fine-grained policies that enforce least-privilege access, revoke credentials after use, and enable safe break-glass workflows, with zero changes to your application code. https://t.co/do1n2dkBHQ
riptides.io
Riptides Conditional Access extends workload identity with time-based, HTTP-aware, and usage-based policoes. Our XACML-inspired model and OPA evaluation let you enforce real zero-trust decisions...
0
4
4
How do you debug a kernel module under real workloads, real traffic, and real Kubernetes scheduling quirks and do it repeatedly without guessing? https://t.co/q1CtsVpyoH
riptides.io
At Riptides, SPIFFE-based identities and encrypted communication start in the kernel. When your trust fabric lives that deep, fast builds and full test coverage aren't optional, they're essential. In...
0
4
4
SPIFFE-backed OAuth is emerging as a strong fit for the MCP ecosystem, enabling AI agents to self-authenticate without secrets and laying the foundation for a secure, identity-first model. https://t.co/iGT9dHV7FP
#AI #AIAgent #MCP
riptides.io
Built on emerging OAuth RFC drafts and using SPIFFE based identities, workloads in an MCP environment can authenticate and obtain tokens without client secrets. This approach enables self-registeri...
0
0
1
Every SPIFFE ID, certificate, and mTLS handshake at Riptides originates in the Linux kernel and starts with one question: can we prove who this workload is? This post explores how process-level evidence builds verifiable trust. https://t.co/8rIHo1tcmb
riptides.io
Every SPIFFE ID, certificate, and mTLS handshake at Riptides originates in the Linux kernel and begins with a single question: can we prove who this workload really is? This post explores how...
0
1
3
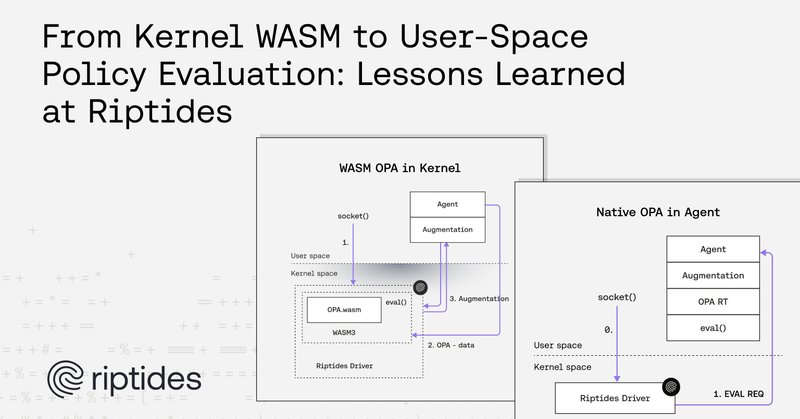
We ran WebAssembly inside the Linux kernel to evaluate Open Policy Agent policies in real-time. It was fast. It was elegant. It was... a nightmare to maintain. Here's what we learned moving from kernel-space WASM to user-space policy evaluation. https://t.co/mgyWoSwjRH
riptides.io
At Riptides, we issue identities directly to workloads in the kernel and use OPA policies to secure and orchestrate their communication. These policies govern socket connections in real time,...
0
4
4
OAuth2 solved human consent. Now it must evolve for workloads and AI agents. In our new post we explore how SPIFFE + emerging OAuth2 standards enable secure workload identity. https://t.co/DIbuVMTo1r
#OAuth2 #SPIFFE #WorkloadIdentity #AgenticAI #security
riptides.io
OAuth2 is evolving beyond human consent into a universal model for secure workload identity. Learn how SPIFFE and emerging OAuth2 standards form the foundation for safe, auditable agentic AI.
0
2
2
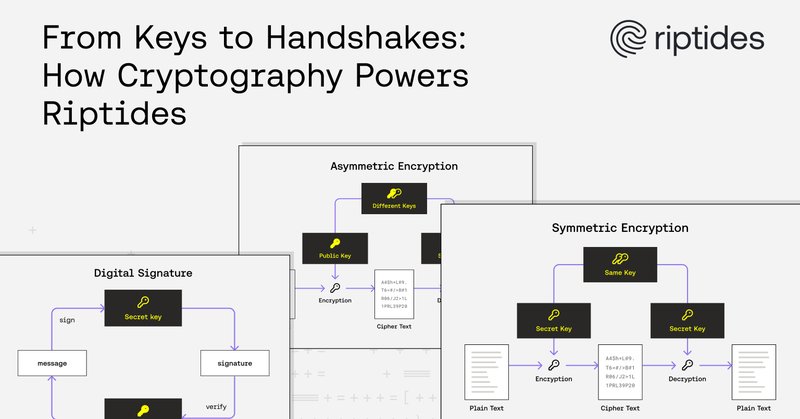
Riptides anchors non-human identity in the kernel with SPIFFE, kTLS & in-kernel mTLS handshakes, merging identity and encrypted communication seamlessly. Cryptography is the foundation that makes it all possible. https://t.co/B9oJSegE7W
#Security #Cryptography
riptides.io
In this blog post, we take a closer look at the cryptography that powers Riptides, the non-human identity fabric for workloads and AI agents. We break down the fundamentals of symmetric and asymmet...
0
0
1
Riptides delivers credentials straight into the request stream. No app changes, no secret handling. AWS, GCP, Azure, or OAuth2 tokens, secure invocation is seamless. https://t.co/dynyaxxDMK
#security #NHI #devops #secops
riptides.io
Riptides brings secretless, on-the-wire credential injection to non-human clients. Instead of storing long-lived credentials, workloads receive short-lived credentials dynamically and transparently...
0
2
2
We’ve open sourced libsigv4, a lightweight C library for AWS SigV4 signatures. It runs inside the Linux kernel to transparently sign outgoing requests. No app changes, no secret leaks, just secure AWS integration. https://t.co/7P8i5qyaZG
#kernel #aws #security
riptides.io
We’ve released libsigv4, a lightweight and portable C implementation of AWS SigV4 signatures, built for kernel-based and embedded environments. It requires zero allocations, supports pluggable crypto...
0
1
2
Current identity federation isn't workload-aware, lacks granularity, and falls short of true zero trust. For modern-day security, you need fine-grained, SPIFFE-based secure identities, ephemeral credentials, and seamless multi-cloud integration. https://t.co/VzKkMqHjRT
riptides.io
Cloud-native federation isn’t enough for secure, per-workload identity. AWS, GCP, and Azure support external IDPs, but today’s federation approaches fail to meet the needs of modern, large-scale...
0
0
0
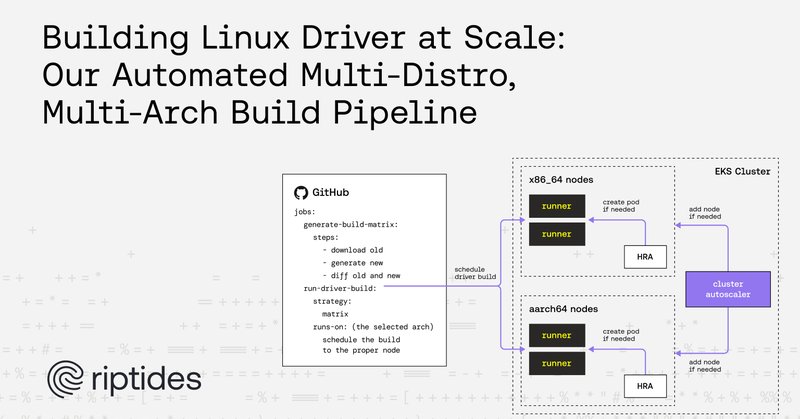
Shipping a pre-built kernel module across distros and architectures isn’t trivial. A fully automated pipeline was built to compile, test, and package a Linux kernel module at scale. https://t.co/EviD2pXHrZ
riptides.io
Managing driver builds for every major Linux distribution, kernel version, and architecture can be challengeing.
0
5
5
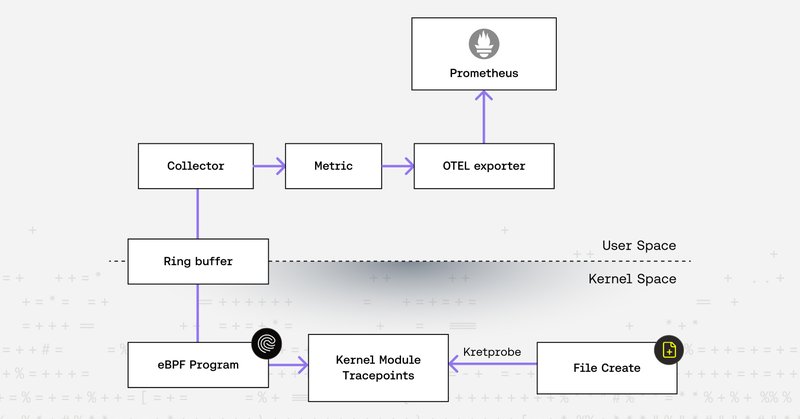
A zero-overhead telemetry path was built from Linux kernel tracepoints to Prometheus. Observability is treated as a foundation for identity, posture, and policy. Here’s how it was done, kernel-first. https://t.co/DbRDvmbiAB
#kernel #ebpf #observability #prometheus
riptides.io
This blog post illustrates how to build a complete end-to-end telemetry pipeline—from kernel space to Prometheus, using Linux tracepoints, eBPF, and OpenTelemetry (OTEL). We start with a custom...
0
4
4
Most workload identity systems are flawed: – Identity is assigned to neighboring processes – Trust boundaries are blurred – Lateral movement becomes trivial It's time for kernel-level identity. No sidecars, no proxies. https://t.co/0OOpjep7ym
riptides.io
Today’s workload identity systems are overengineered, inefficient, and fundamentally misplaced. Relying on userspace constructs like sidecars and proxies have worked at smaller scale — but they break...
0
3
3
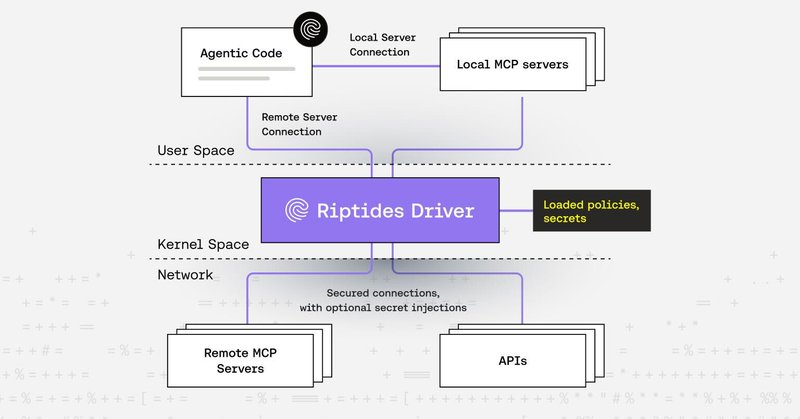
When Agents Talk, Riptides Listens and Secures. Inside MCP Communication Hardening. https://t.co/rfPo5Mpyyh
riptides.io
Agentic workload security is becoming increasingly important in today’s AI-driven world. This post explores how Riptides secures communication between agents and MCP servers using kernel-level mTLS,...
0
5
5
Secure your services with cryptographic identity, not IPs or tokens. Dive into how X.509 certificates build that foundation. https://t.co/uzYfkTdxHB
#X509 #mTLS #NHI #CyberSecurity #DevOps
riptides.io
X.509 certificates remain a core building block for establishing trust between services, even in today’s dynamic, machine-driven environments. This post explains how X.509 works, where it falls...
0
3
4
Let’s explore MCP (Model Context Protocol), a fast-emerging standard in the agentic ecosystem. Discover what it is, when to use it, and the key security pitfalls to watch out for. https://t.co/CQzENyCENp
riptides.io
MCP (Model Context Protocol) is quickly becoming a foundational standard for enabling tool-augmented LLMs to interact with external systems. As the agentic ecosystem matures, so does the need for...
0
1
1
Rethinking Non-Human Identity: Kernel-Enforced, Ephemeral, and Built for a Secretless Future. Deep dive into how Kernel TLS (kTLS) and SPIFFE unlock secure, zero-touch identity for workloads and AI agents. https://t.co/Z5R2DKJEr9
riptides.io
At Riptides, we believe that the future of secure, scalable computing starts in the kernel. By moving critical identity management and mutual TLS (mTLS) operations into the Linux kernel, we eliminate...
0
5
7
Observability starts in the kernel, Riptides brings it to user space. See how we turn low-level signals into high-impact metrics. https://t.co/TpmFISTJl3
riptides.io
In our previous post, we’ve explored how to define tracepoints inside the kernel to gain deep visibility into system behavior. But tracing is only half the challenge—getting that data to user-space...
0
1
2