Haseeb Raja
@raadhhaseeb
Followers
66
Following
1K
Media
56
Statuses
829
Learning Blockchain/ZK/Cryptography. Open to Work. Default and Offensive Privacy. INFJ-T. Søren’s intensity, Camus’ solution, Spinoza's World.
Joined August 2013
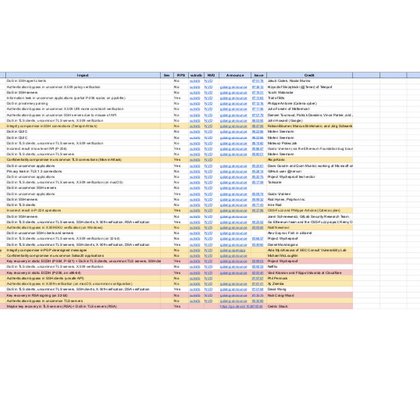
Attached link contains the list of vulnerabilities in the Go cryptography packages. All credits to Filippo Valsorda ( https://t.co/tDPLt6YZSo) for compiling and sharing this sheet. https://t.co/LSv8ritEnp
#golang
docs.google.com
0
0
0
2/ Baba Farid reminds us of the tragic paradox of sustenance and survival.
0
0
0
1/ توں کی جانیں یار فریدا روٹی بندہ کھا جاندی اے Little do you know, O (friend) Farid, The (pursuit of) bread eats (devours) the man. #poetry
1
0
1
A PQ, transparent, folding scheme (think IVC) that enables the APT to remain resourceful, mimics latching (the Venom), and remains evasive while maintaining obfuscation and forensic silence.
0
0
0
Academic science doesn’t need more money. It needs fewer administrators and fewer weak scientists clogging the system. The people who actually innovate mostly need one thing: for everyone else to step aside.
49
50
555
Yes, ZKPs are computationally brutal, for now. *winks in PQ-ZK
0
0
0
Offensive pipeline for the signed zk-APT: 1. Reach the target. 2. Enclave and stealth. 3. Recon. 4. Verify the proof of conditions. 5. Execute. Goals: Forensic immunity, obfuscation, stealth, autonomy. #zk #cryptography
2
0
0
A zk-aware, multistage terminal agent (optionally TEE-isolated) that runs an offensive cmd pipeline, unwrapping each stage only when a ZK proof of the right environment and privileges verifies, enabling cross-device CTF missions without exposing the when, the why, or the how.
Picture offensive privacy as Venom waiting for its prey in ZK. It clings onto the attacker without alarm or suspicion, until the predator becomes the prey. Now imagine it as a default.
1
0
0
Picture offensive privacy as Venom waiting for its prey in ZK. It clings onto the attacker without alarm or suspicion, until the predator becomes the prey. Now imagine it as a default.
0
0
0
I also want to note here that I've met people WAY smarter than me. I've met truly brilliant people yet I've passed them in the malware field. Intelligence is one thing, but if you're intelligent and you don't apply yourself and actually do something, then nothing will happen.
9
10
303
You’ll have a much easier time understanding ZK-STARKs if you already know how the Number Theoretic Transform works (Fast Fourier Transform for Polynomial evaluation in finite fields). The core subroutine in ZK-STARKs, FRI, is a close variant of the NTT. Now you can learn NTT
Imagine understanding an algorithm so well that you can carry it out - by hand - off the top of your head - and without memorizing any unnatural tricks The ZK Book has expanded again, this time to teach the Fast Fourier Transform -- specifically the Number Theoretic Transform
2
15
126
Even if you can't take as big mental leaps as someone else, you can often still compete on superior skillmaxxing. Obviously cognitive advantages give a huge leg up, but few people come anywhere close to maximizing the volume & efficiency of their upskilling.
2
11
88
Life hack to take control of your attention: Get up, walk away, come back in few minutes. Process: mental block --walk away--> stimulus changes --rest breaks loop--> mind enters diffuse mode --return--> pomodoro kicks in #lifehacks #ADHD
0
0
0
Cryptography is a tool for existential sovereignty against overwhelming, rabid forces and tech should be accessible, verifiable, and incorruptible. #cryptography
0
0
0
4/ The code serves as a practical example of a Key Agreement + Encryption flow in Go and Rust. https://t.co/bHIxp3YpCj
https://t.co/yGou0kz2yZ
#ecc #Programming #aes
github.com
[Rust] This repo contains an example implementation of encryption and decryption of a message using a shared key generated by ecdsa key pair between 2 different users. - GitHub - raadhshenshahhase...
0
0
0