Quentin Roland
@quent0x1
Followers
289
Following
277
Media
0
Statuses
65
Pentester @Synacktiv 🤖 https://t.co/FhHN2RnPym
Joined June 2022
RT @netbiosX: 🛠️ GroupPolicyBackdoor - a python utility for Group Policy Objects (GPOs) manipulation and exploitation. ✅ GPO attack vector….
github.com
Group Policy Objects manipulation and exploitation framework - synacktiv/GroupPolicyBackdoor
0
9
0
RT @Synacktiv: The GroupPolicyBackdoor tool, presented at #DEFCON 2025, is now available on Synacktiv's GitHub: Thi….
github.com
Group Policy Objects manipulation and exploitation framework - synacktiv/GroupPolicyBackdoor
0
98
0
RT @Synacktiv: 🔥 A few hours ago our experts took the stage at #DEFCON33, sharing cutting-edge research on SCCM exploitation and modern GPO….
0
23
0
RT @Synacktiv: Don't miss @kalimer0x00 at #DEFCON33! .His talk, "SCCM: The Tree That Always Bears Bad Fruits", covers modern attack paths a….
0
20
0
RT @Synacktiv: Catch us at #DEFCON33!.@quent0x1 and @wil_fri3d will show how to turn your Active Directory into the attacker’s C2. They'll….
0
15
0
RT @Synacktiv: Microsoft just released the patch for CVE-2025-33073, a critical vulnerability allowing a standard user to remotely compromi….
0
263
0
RT @wil_fri3d: Check out how I discover CVE-2025-33073 : RCE with NTLM reflectiv attack allowing authenticated user to compromise any machi….
0
24
0
RT @DirectoryRanger: Taking the Relaying Capabilities of Multicast Poisoning to the Next Level: Tricking Windows SMB Clients into Falling B….
synacktiv.com
Taking the relaying capabilities of multicast poisoning to the next
0
5
0
RT @Synacktiv: We still have a few talks for #SSTIC2025 last day! This morning, @hugoclout presents 2 proxy tools used during pentests 🌐 ht….
0
6
0
RT @Synacktiv: For our last talk, @croco_byte explains how to exploit SCCM policies to harvest credentials 🔑 #SSTIC2025 .
0
8
0
RT @Synacktiv: Synacktiv was at @ToulouseHacking this week!.For the first talk, @croco_byte presented "Tapping into the SCCM policies goldm….
0
4
0
RT @pentest_swissky: Abusing multicast poisoning for pre-authenticated Kerberos relay over HTTP with Responder and krbrelayx - @croco_byte….
synacktiv.com
Abusing multicast poisoning for pre-authenticated Kerberos relay over
0
19
0
RT @BlWasp_: Following the recent @Synacktiv 's article about abusing WebClient authentications from multicast poisoning, I have made a qui….
github.com
Hello! In this recent article, Synacktiv demonstrated that during multicast poisoning, depending on the error code returned by the SMB server at the end of the authentication process, it was possib...
0
25
0
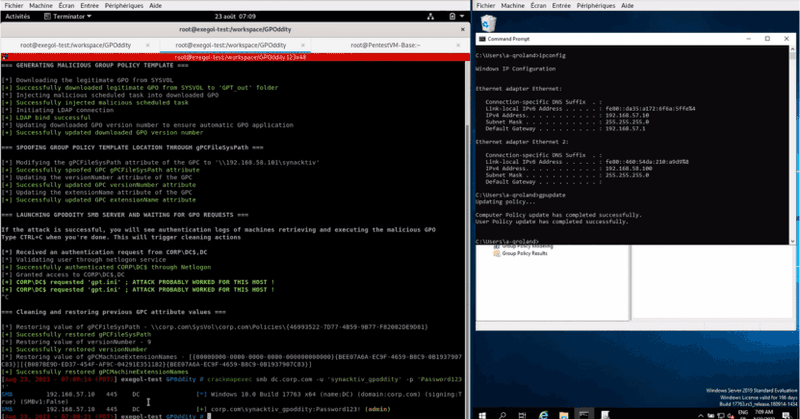
RT @Dinosn: GPOddity: automating GPO attack vectors through NTLM relaying
meterpreter.org
The GPOddity project aims at automating GPO attack vectors through NTLM relaying. For more details regarding the attack and a demonstration
0
51
0
RT @BlackAlpsConf: 🎥 RECORDED TALK #BlackAlps24 🎥. ⚡⚡⚡ Unveiling the offensive potential of Group Policy Objects in Active Directory: old -….
0
5
0
RT @hacknspeak: 🇫🇷🎙️Nouvel épisode du podcast Hack'n Speak accompagné du seul et unique @croco_byte le terrible CROCO 🐊🐊🐊. C'est la partie….
creators.spotify.com
Twitter: https://x.com/croco_byteTwitter: https://x.com/mpgn_x64Blog post - https://www.synacktiv.com/publications/relaying-kerberos-over-smb-using-krbrelayx- https://www.synacktiv.com/publicat...
0
8
0
RT @HackAndDo: That's gold 💎 Can't wait to try this out in an engagement.Long live HTTP relay.
0
4
0
RT @Synacktiv: In our latest article, @l4x4 revisits the secretsdump implementation, offering an alternative avoiding reg save and eliminat….
synacktiv.com
LSA Secrets: revisiting secretsdump
0
149
0
RT @Synacktiv: In our latest article, @croco_byte and @SScaum demonstrate a trick allowing to make Windows SMB clients fall back to WebDav….
synacktiv.com
Taking the relaying capabilities of multicast poisoning to the next
0
95
0