Puma Security
@puma_scan
Followers
309
Following
90
Media
154
Statuses
328
Experts in Cloud Security, DevOps, creators of Puma Scan. Let us help your team create and deliver secure software. #SecDevOps #CloudSecurity
West Des Moines, IA
Joined September 2016
RT @absoluteappsec: Absolute AppSec will be live tomorrow (12PM ET) with @sethlaw and a magnanimously guest-hosting @lojikil. Meanwhile, en….
0
3
0
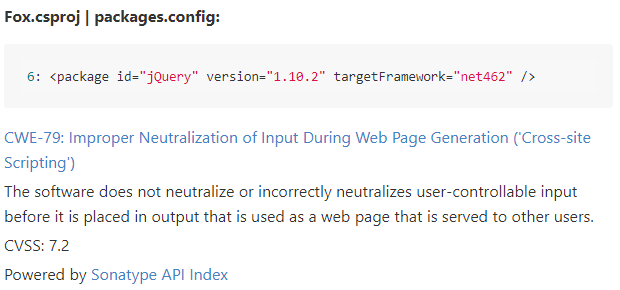
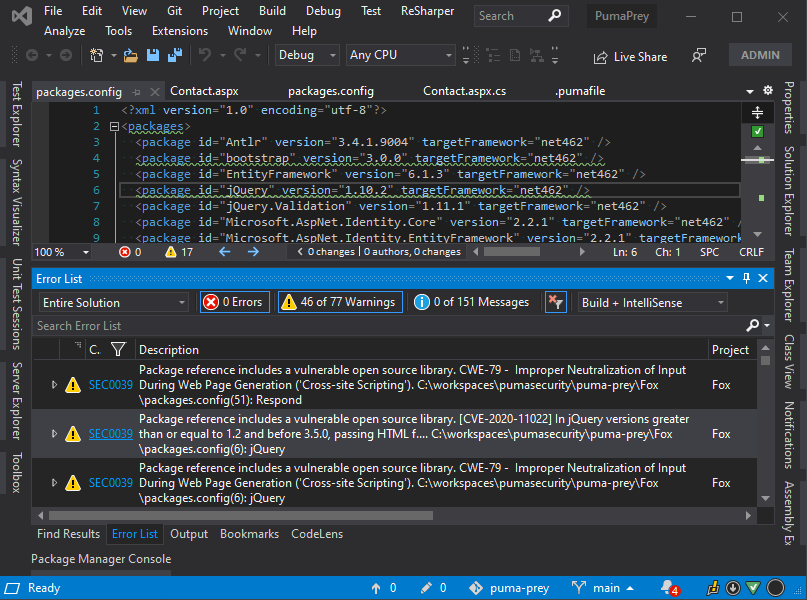
We are excited to announce a new feature in the Puma Scan Professional v1.1 release: @sonatype OSS Index Integration. Learn how to start scanning for vulnerable dependencies here:
0
0
4
Get your hands on a copy of Visual Studio 2019 Tricks & Techniques by @PaulBSchroeder & @curea. It features our favorite security tool, @puma_scan #pumascan #pumasecurity #visualstudio #securecoding
0
3
4
Upgrades to Puma Scan Professional are available! #Azure, Server & End User tools include an upgrade of the #.NET Compiler API to v3.0 to enable scanning of C# 8.0 projects. More information can be.found at
0
0
0
Our new product, Puma Scan Professional End User Edition now integrates with Visual Studio Code, a cross platform – Windows, Mac or Linux code editor from Microsoft. Contact us to get set up today! sales@pumascan.com.
0
0
0
Examine real-world scenarios that security professionals encounter defending Cloud workloads running on Serverless Infrastructure. 👉 #DevSecOps
0
3
6
Get faster Security Unit Testing feedback while building strong security checks in the #DevOps Pipeline. We provide the insight, consulting and customization necessary to enable secure product delivery.
0
0
1
Avoid falling victim to the #Cloud. Vulnerabilities occur when an application requests data from an untrusted URL location. Follow customer Cloud Security Responsibilities by writing secure code, no SSRF, enforcing least privilege execution IAM roles & configuring VPC Endpoints.
0
0
0
We can help you avoid falling victim to #Cloud. Server-side Request Forgery vulnerabilities occur when an application requests data from an URL that is supplied from an untrusted location, including: request parameters, web services and backend systems.
0
0
0
We can help you avoid falling victim to #Cloud. Server-side Request Forgery vulnerabilities occur when an application requests data from an URL that is supplied from an untrusted location, including: request parameters, web services and backend systems.
0
0
1
We can help you avoid falling victim to #Cloud. Server-side Request Forgery vulnerabilities occur when an application requests data from an URL that is supplied from an untrusted location, including: request parameters, web services and backend systems.
0
0
0
We can help you avoid falling victim to #Cloud. Server-side Request Forgery vulnerabilities occur when an application requests data from an URL that is supplied from an untrusted location, including: request parameters, web services and backend systems.
0
0
0
We can help you avoid falling victim to #Cloud. Server-side Request Forgery vulnerabilities occur when an application requests data from an URL that is supplied from an untrusted location, including: request parameters, web services and backend systems.
0
0
0
We can help you avoid falling victim to #Cloud. Server-side Request Forgery vulnerabilities occur when an application requests data from an URL that is supplied from an untrusted location, including:.request parameters, web services and backend systems.
0
0
0