pr0cf5
@pr0cf51
Followers
2K
Following
2K
Media
40
Statuses
2K
CS @ @GeorgiaTech, AIxCC w/ @TeamAtlanta24 ex. KAIST GoN 18, @SuperGuesser @osec_io
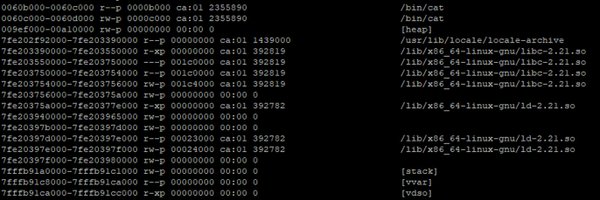
/proc
Joined April 2019
[Research] smart contracts auditing 101 for pwners - PART 1 (EN) https://t.co/NKVMl4qYLq Hello, this is d4tura. In this research post, I summarize the core concepts required to solve the smart contract wargame "Damn Vulnerable DeFi." From the perspective of a 'pwner' more
0
19
132
All web3 security researchers should read this 10/10 report on all web3 security incidents in 2024 and stats around them. Great job by @ChainLight_io. Read below👇 https://t.co/rxtn8n4dQO
18
65
370
a senior engineer at google just dropped a 400-page free book on docs for review: agentic design patterns. the table of contents looks like everything you need to know about agents + code: > advanced prompt techniques > multi-agent patterns > tool use and MCP > you name it
65
1K
10K
Checkout this open-sourced handy MCP server for JEB decompiler by us: https://t.co/LXSEFtSbFx . Contributions and use cases are always welcomed.
github.com
Contribute to flankerhqd/jebmcp development by creating an account on GitHub.
1
7
41
⚡ Going beyond the baseline, we forked Jazzer with LibAFL to push Java fuzzing further under AIxCC pressure — lessons learned. 👉 https://t.co/PF1XQow9rs
#AIxCC #Cybersecurity #CTF #AI #LLM #GenAI #AICyberChallenge #DARPA #DEFCON #Security #Vulnerability
team-atlanta.github.io
How we incorporated LibAFL as a new fuzzing backend for Jazzer
1
14
47
HITCON CTF 2025 Date: UTC 08/22 14:00 ~ 08/24 14:00 https://t.co/QDdiyGlv3y Thanks to @vinami from DeFiHackLabs for creating the web3 challenges for HITCON.
ctf2025.hitcon.org
Online Jeopardy, Jul 12-14 2024
0
3
11
This is just the beginning, more technical stuff coming up!
New blog out now! We’re answering the top questions from the DEFCON audience and sharing the behind-the-scenes story of our victory. https://t.co/2U6Ou9S3JS
#AIxCC
0
1
10
First, we use an LLM classifier. We provide the vuln report and relevant source code, requesting a single output token: whether the vulnerability is "likely" or "unlikely" to be real. By inspecting the logprobs of the completion, we can score candidate vulns by likelihood!
2
1
6
Got a knack for security? We've launched a rewards program for OSV-SCALIBR and want your help! Earn cash 💰 for creating new plugins that detect vulnerabilities, secrets, or extract software inventory. https://t.co/jvtVTSpCXs
bughunters.google.com
Check out our new Patch Rewards Program for OSV-SCALIBR, offering financial incentives for providing novel OSV-SCALIBR plugins for inventory, vulnerability, or secret detection.
2
16
68
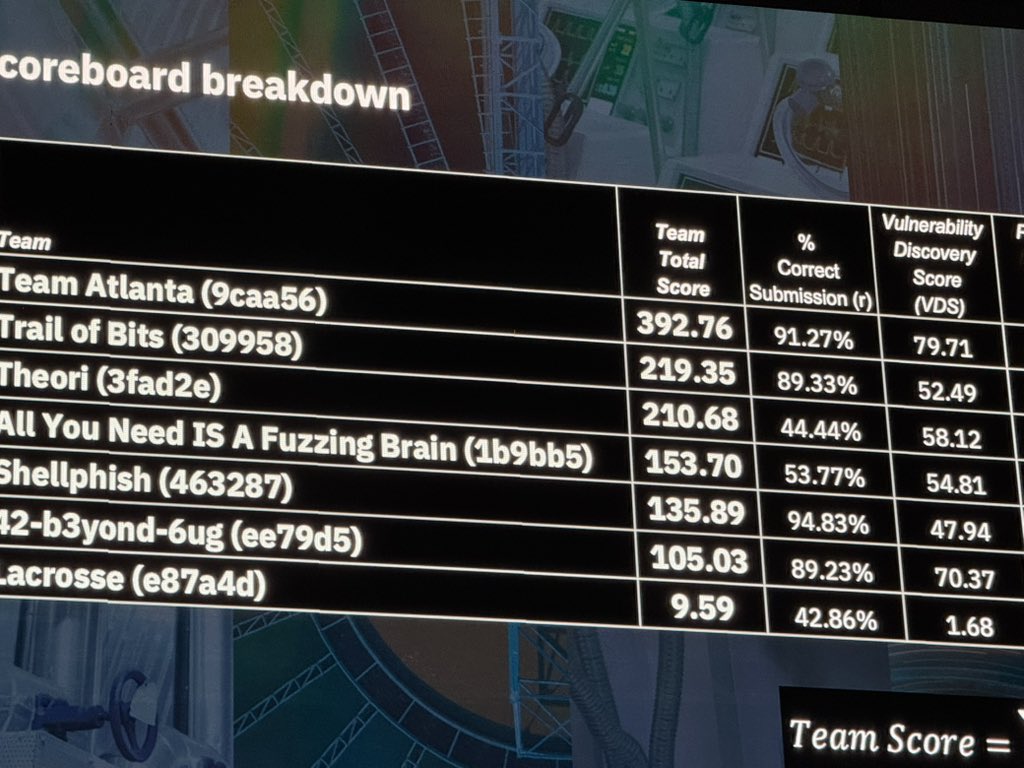
🚀 Proud to be part of DARPA #AIxCC Winner - @TeamAtlanta24 ! Our sub-team built one of the key components: Multilang LLM Agents for vulnerability detection.
2
3
32
Here’s the source code of our #AIxCC winning team @TeamAtlanta24, enjoy! https://t.co/jSA4H7mH4U More things TBA
github.com
Contribute to Team-Atlanta/aixcc-afc-atlantis development by creating an account on GitHub.
2
38
147
We did it!!!!!!!!!!!!!!!!!!!!
5
4
93
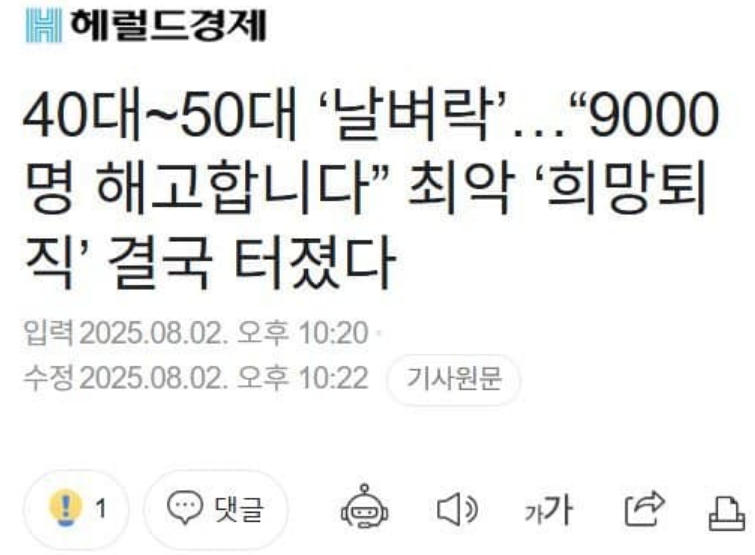
많은 기업들이 희망퇴직을 실시하기 시작했습니다. 4050 날아가기 시작하네요. [헤럴드경제] 40대~50대 ‘날벼락’…“9000명 해고합니다” 최악 ‘희망퇴직’ 결국 터졌다 https://t.co/jBilQ248IZ
96
460
1K
When you make a Bank ACH transaction, it’s literally just an SFTP upload. Sent as a NACHA file, it's 940 bytes of ASCII text. Bank-to-Bank transactions cost ~0.2 cents. As long as it travels via encrypted tunnel; it’s compliant! Here’s how the quirky system works:
218
1K
13K
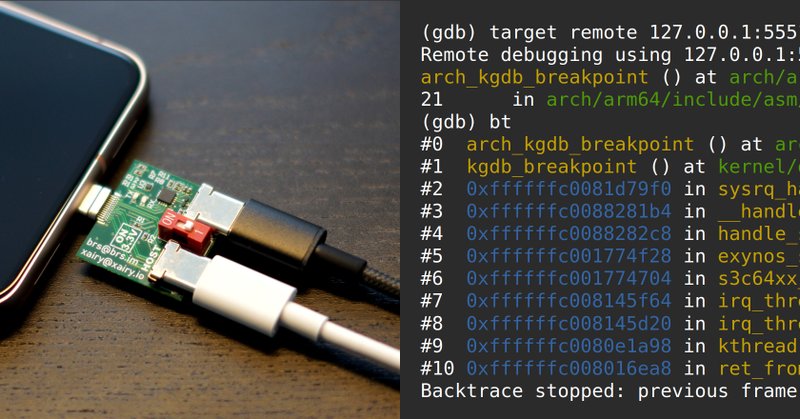
Documented instructions for setting up KGDB on Pixel 8. Including getting kernel log over UART via USB-Cereal, building/flashing custom kernel, breaking into KGDB via /proc/sysrq-trigger or by sending SysRq-G over serial, dealing with watchdogs, etc. https://t.co/vb4mgLDJrl
xairy.io
Instructions for getting kernel log, building custom kernel, and enabling KGDB on Pixel 8
5
143
474
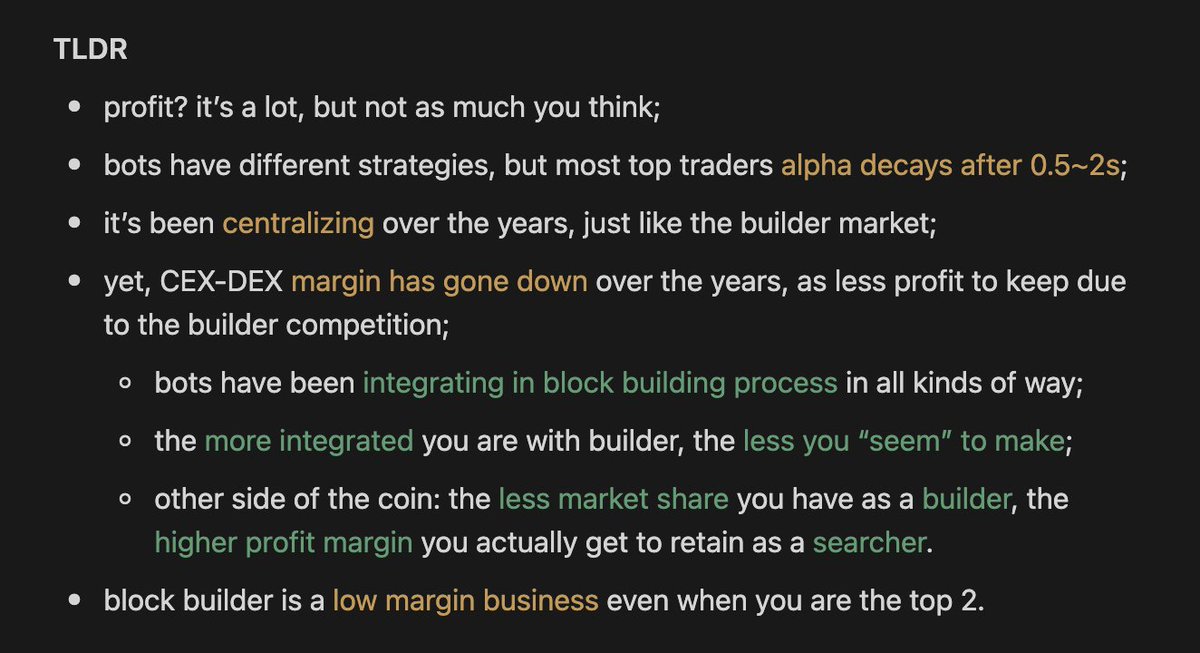
How much profits does MEV bots 🤖 really make from CEX-DEX Arbitrage? No one can answer this question before, but we are excited to share a new paper measuring it with formal methods finally! (We got accepted by AFT25' !🥳) I summarized all the alpha in one pic for you 😃
28
85
580
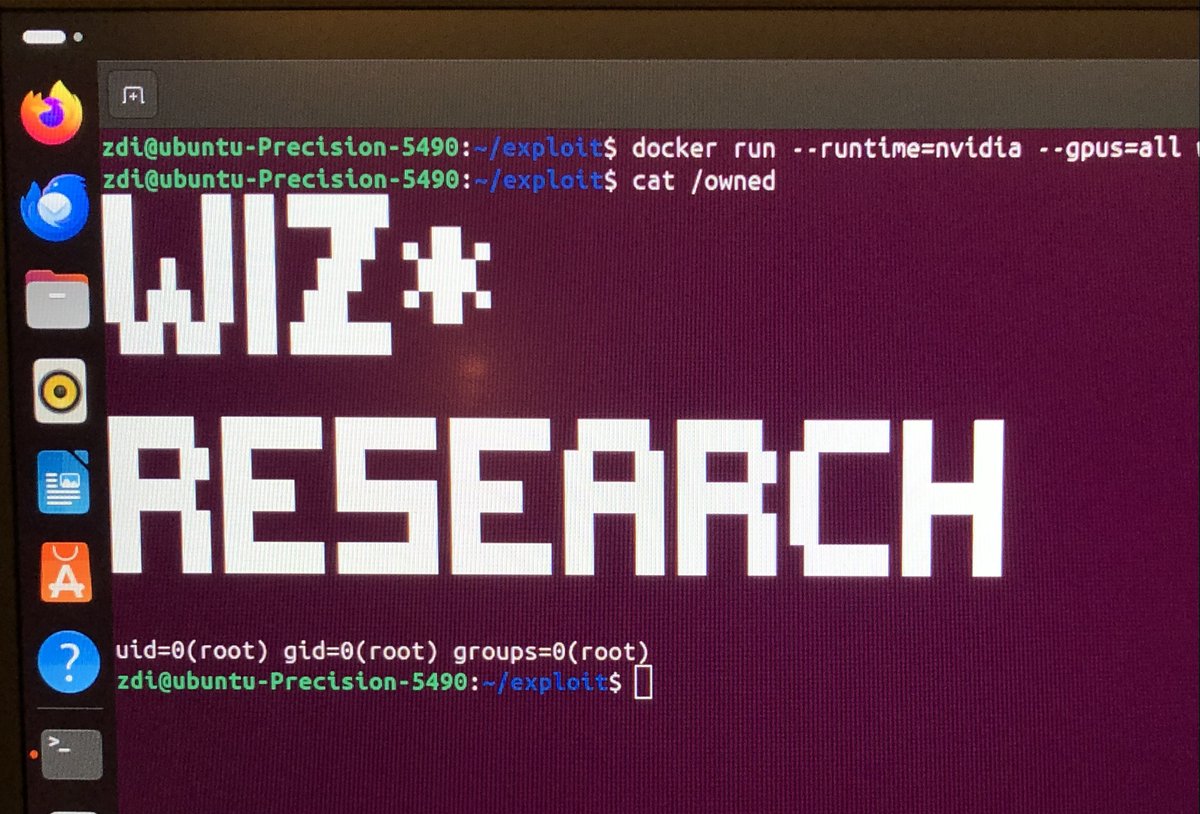
We found a new container escape affecting all container runtimes using @NVIDIA GPUs. The crazy part? The exploit is just three lines long 🤯 This is the story of #NVIDIAScape 🧵👇
9
135
639
Again an interesting bug, an excellent and very detailed report with PoC & exploit from 303f06e3🔥🔥🔥 [$50000][403211343][turboshaft]Improper Error Handling in LateLoadElimination for String Map -> RCE https://t.co/UWeDbeVNYh
[403211343][turboshaft] Remove LoopPeelingPhase https://t.co/bzvt5WPSWP
3
16
68
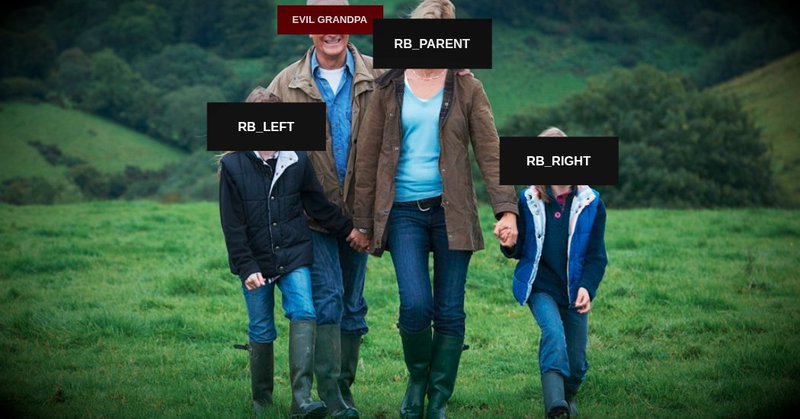
Here is our 0day for kernelCTF🩸 - 82k bounty - quickest submission ever - all instances pwned😎 https://t.co/0sb11m8ITD Disclaimer: We apologize for abusing the red black tree family. Turning grandparents against grandchildren is only acceptable in the context of pwn😤
syst3mfailure.io
CVE-2025-38001 is a Use-After-Free vulnerability in the Linux network packet scheduler, specifically in the HFSC queuing discipline. When the HFSC qdisc is utilized with NETEM and NETEM packet...
Exploit write-ups for our 🚨latest 0-day🚨and the tragedy that swept the red black tree family dropping soon 👀 Here is a tiktok style video for those of you with no attention span thanks to slop and social media. Turn on the audio!!!
0
76
308